| 序號 |
漏洞名 |
公佈時間 |
發現團隊 |
CVE編號 |
參考鏈接 |
致謝截圖 |
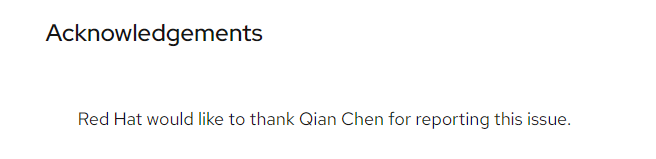
| 272 |
RedHat Open vSwitch |
2022-12-20 |
奇安信代碼安全實驗室 |
CVE-2022-4338 |
https://access.redhat.com/security/cve/CVE-2022-4338
|
 |
| 271 |
RedHat Open vSwitch |
2022-12-20 |
奇安信代碼安全實驗室 |
CVE-2022-4337 |
https://access.redhat.com/security/cve/CVE-2022-4337
|
 |
| 270 |
Windows Graphics Component |
2022-12-14 |
技術研究院天工實驗室 |
CVE-2022-4107 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41074
|
 |
| 269 |
Windows 打印機 |
2022-12-14 |
技術研究院天工實驗室 |
CVE-2022-44678 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-44678
|
 |
| 268 |
Windows Graphics Component |
2022-12-14 |
技術研究院天工實驗室 |
CVE-2022-44679 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-44679
|
 |
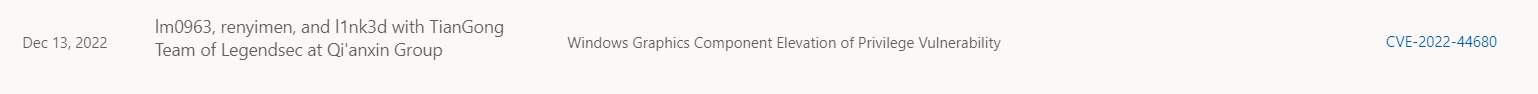
| 267 |
Windows Graphics Component |
2022-12-14 |
技術研究院天工實驗室 |
CVE-2022-44680 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-44680
|
 |
| 266 |
Windows 打印機 |
2022-12-14 |
技術研究院天工實驗室 |
CVE-2022-44681 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-44681
|
 |
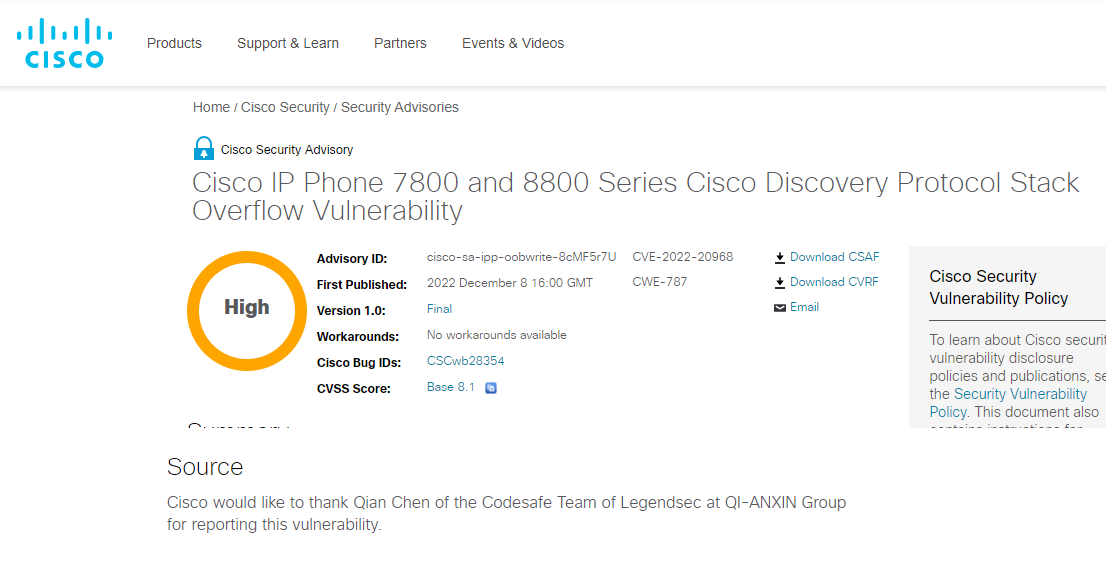
| 265 |
Cisco IP 電話7800 和 8800 系列 Cisco Discovery Protocol 棧溢出 |
2022-12-09 |
奇安信代碼安全實驗室 |
CVE-2022-20968 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipp-oobwrite-8cMF5r7U
|
 |
| 264 |
Mikrotik RouterOS 的snmp進程中存在界外讀漏洞 |
2022-12-09 |
奇安信代碼安全實驗室 |
CVE-2022-45315 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-45315
|
 |
| 263 |
Mikrotik RouterOS 的hotspot進程中存在界外讀漏洞 |
2022-12-09 |
奇安信代碼安全實驗室 |
CVE-2022-45313 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-45313
|
 |
| 262 |
紅帽QEMU VNC服務整數下溢 |
2022-09-26 |
奇安信威脅情報中心 |
CVE-2022-3165 |
https://access.redhat.com/security/cve/cve-2022-3165
|
 |
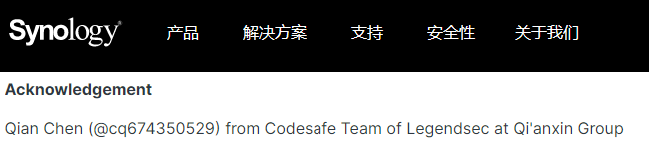
| 261 |
羣暉 |
2022-10-25 |
奇安信代碼安全實驗室 |
CVE-2022-43749 |
https://www.synology.cn/zh-cn/security/advisory/Synology_SA_22_19
|
 |
| 260 |
羣暉 |
2022-10-25 |
奇安信代碼安全實驗室 |
CVE-2022-43748 |
https://www.synology.cn/zh-cn/security/advisory/Synology_SA_22_19
|
 |
| 259 |
羣暉 |
2022-10-25 |
奇安信代碼安全實驗室 |
CVE-2022-27623 |
https://www.synology.cn/zh-cn/security/advisory/Synology_SA_22_18
|
 |
| 258 |
羣暉 |
2022-10-25 |
奇安信代碼安全實驗室 |
CVE-2022-27622 |
https://www.synology.cn/zh-cn/security/advisory/Synology_SA_22_18
|
 |
| 257 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20766 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 256 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20691 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 255 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20690 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 254 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20689 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 253 |
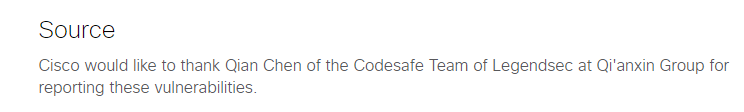
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20688 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 252 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20687 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 251 |
思科 |
2022-10-13 |
奇安信代碼安全實驗室 |
CVE-2022-20686 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ata19x-multivuln-GEZYVvs
|
 |
| 250 |
微軟 |
2022-10-12 |
奇安信代碼安全實驗室 |
CVE-2022-33645 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-33645
|
 |
| 249 |
思科 |
2022-09-23 |
奇安信代碼安全實驗室 |
CVE-2022-20846 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-xr-cdp-wnALzvT2
|
 |
| 248 |
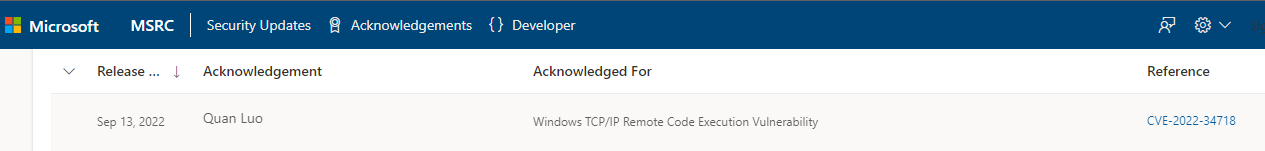
微軟 |
2022-09-14 |
奇安信代碼安全實驗室 |
CVE-2022-34718 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34718
|
 |
| 247 |
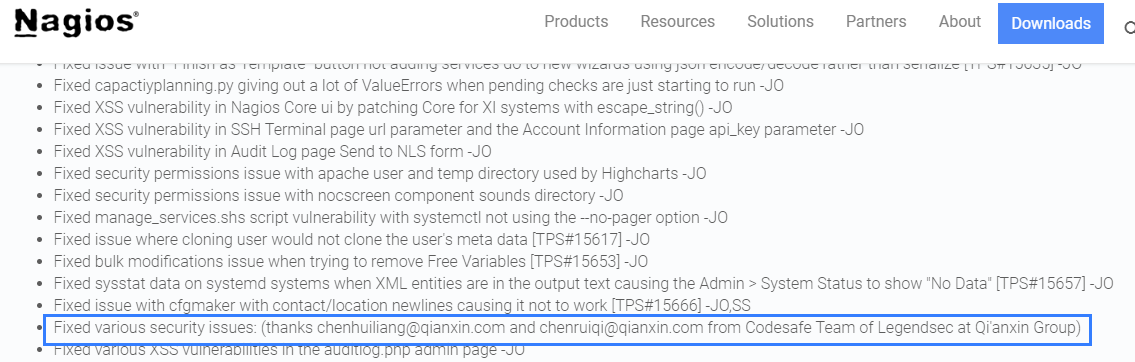
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38254 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 246 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38253 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 245 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38252 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 244 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38251 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 243 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38250 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 242 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38249 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 241 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38248 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 240 |
Nagios |
2021-11-02 |
奇安信代碼安全實驗室 |
CVE-2022-38247 |
https://www.nagios.com/downloads/nagios-xi/change-log/#5.8.7
|
 |
| 239 |
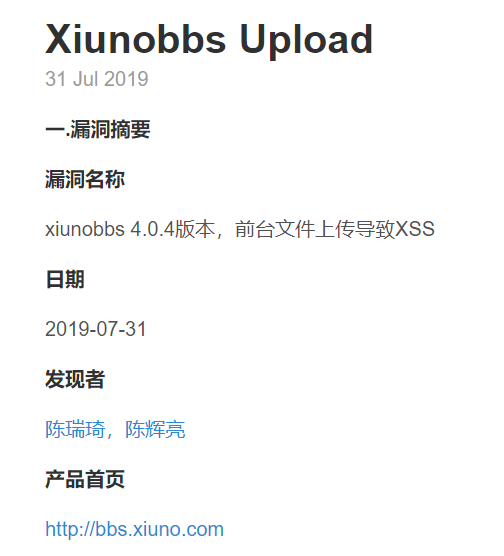
xiunobbs |
2022-07-13 |
奇安信代碼安全實驗室 |
CVE-2020-19914 |
https://kevinoclam.github.io/blog/2019/07/31/xiunobbs-upload/
|
 |
| 238 |
微軟 |
2022-07-13 |
奇安信代碼安全實驗室 |
CVE-2022-22042 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-22042
|
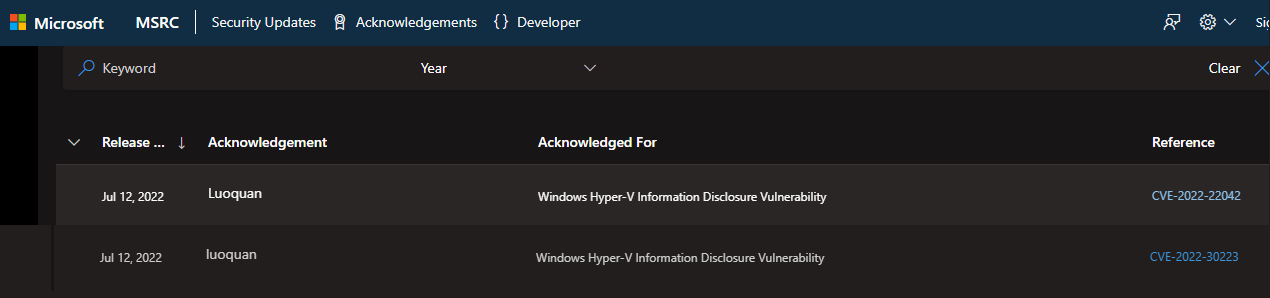 |
| 237 |
微軟 |
2022-07-13 |
奇安信代碼安全實驗室 |
CVE-2022-30223 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30223
|
 |
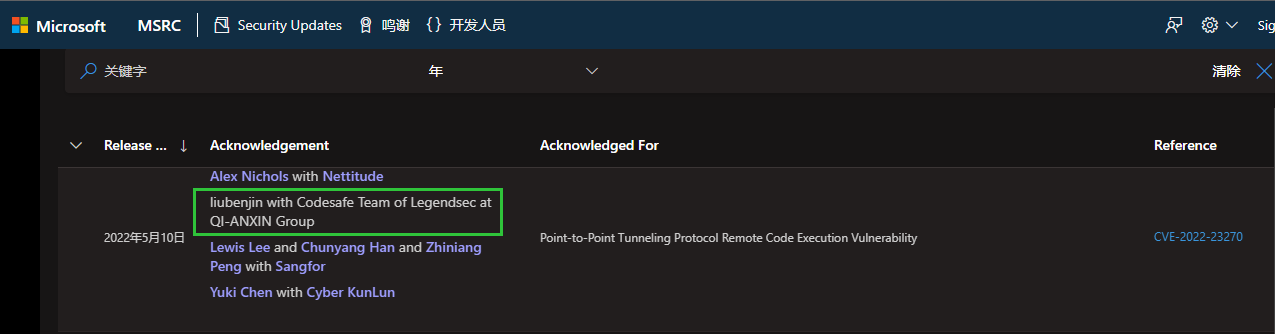
| 236 |
微軟 |
2022-05-10 |
奇安信代碼安全實驗室 |
CVE-2022-23270 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-23270
|
 |
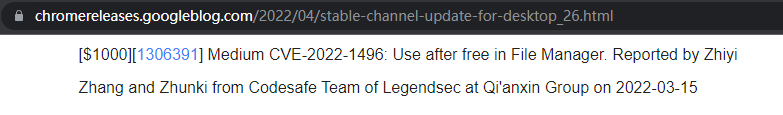
| 235 |
谷歌Chrome |
2022-04-28 |
奇安信代碼安全實驗室 |
CVE-2022-1496 |
https://chromereleases.googleblog.com/2022/04/stable-channel-update-for-desktop_26.html
|
 |
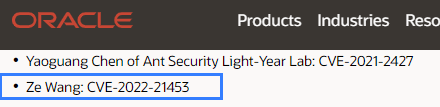
| 234 |
Oracle WebLogic Server |
2022-04-21 |
奇安信代碼安全實驗室 |
CVE-2022-21453 |
https://www.oracle.com/security-alerts/cpuapr2022.html
|
 |
| 233 |
Windows iSCSI Target Service信息泄露 |
2022-04-13 |
奇安信代碼安全實驗室 |
CVE-2022-24498 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-24498
|
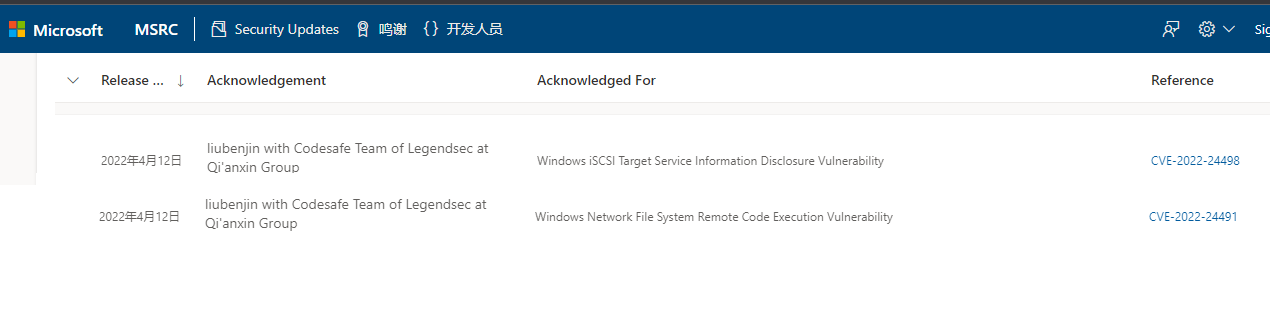 |
| 232 |
Windows Network File System遠程代碼執行 |
2022-04-13 |
奇安信代碼安全實驗室 |
CVE-2022-24491 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-24491
|
 |
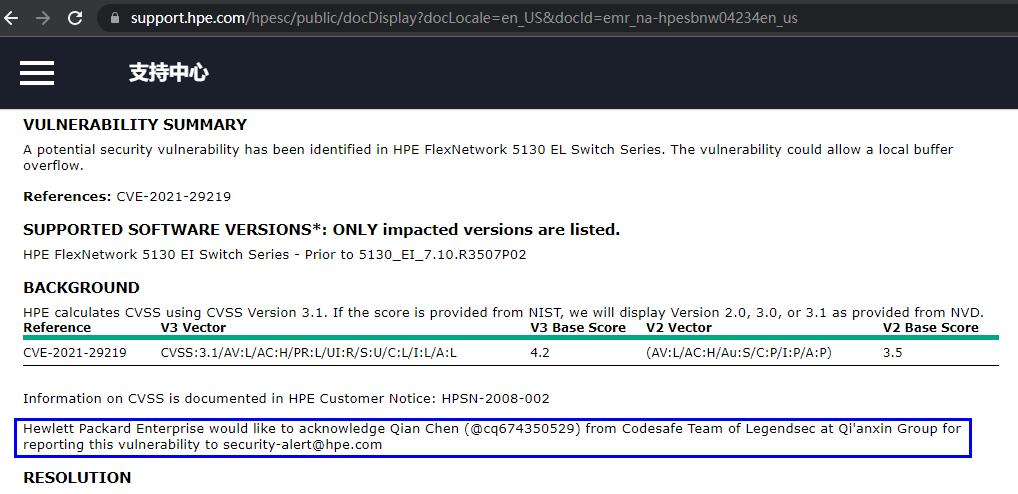
| 231 |
惠普企業HPE FlexNetwork 5130 EI 交換機系列本地緩衝溢出 |
2022-01-29 |
奇安信代碼安全實驗室 |
CVE-2021-29219 |
https://support.hpe.com/hpesc/public/docDisplay?docLocale=en_US&docId=emr_na-hpesbnw04234en_us
|
 |
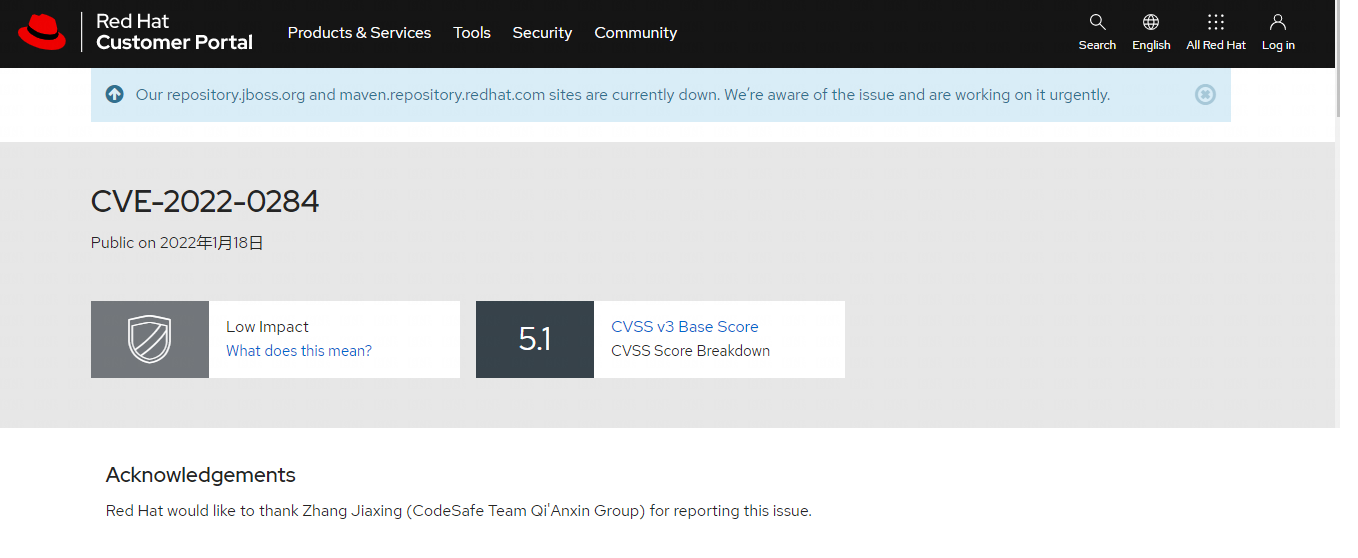
| 230 |
ImageMagick 堆緩衝區溢出讀漏洞 |
2022-02-01 |
奇安信代碼安全實驗室 |
CVE-2022-0284 |
https://access.redhat.com/security/cve/CVE-2022-0284
|
 |
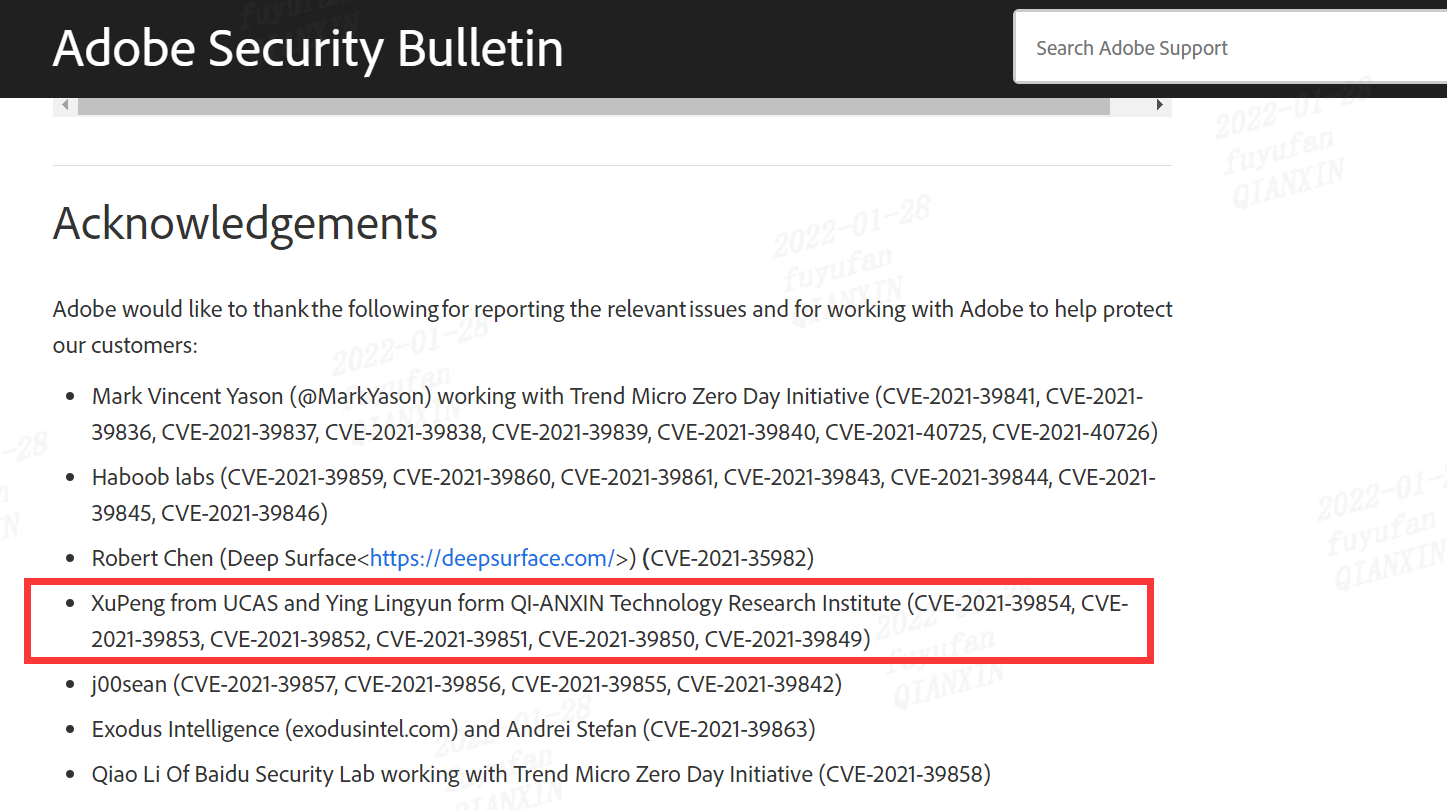
| 229 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39849 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
| 228 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39850 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
| 227 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39851 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
| 226 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39852 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
| 225 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39853 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
| 224 |
ADOBE:應用程序拒絕服務 |
2022-01-01 |
技術研究院 |
CVE-2021-39854 |
https://helpx.adobe.com/security/products/acrobat/apsb21-55.html
|
 |
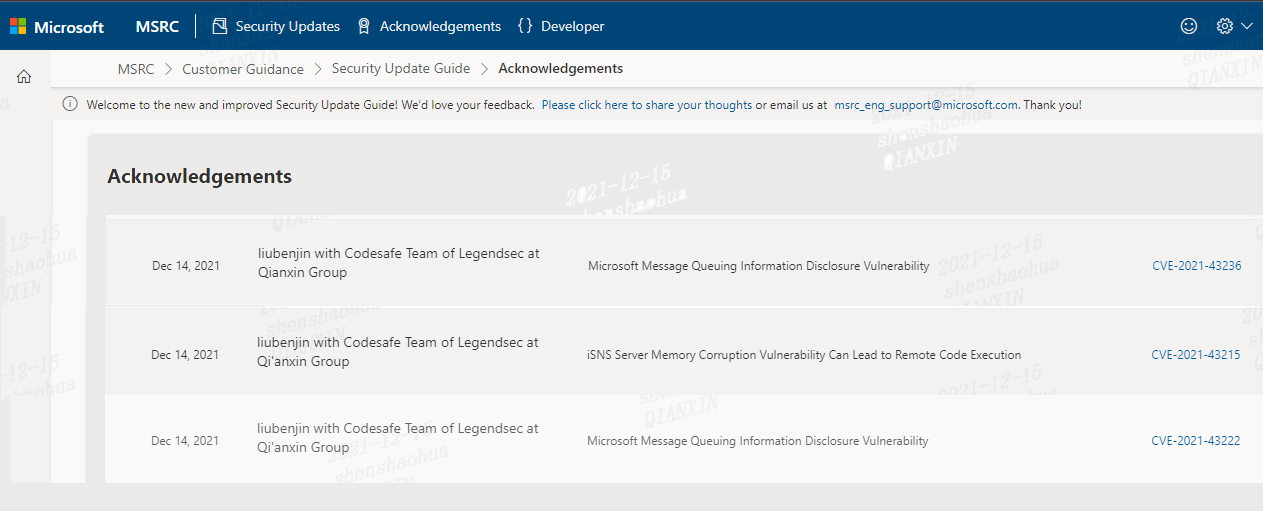
| 223 |
微軟Microsoft Message Queuing 信息泄露漏洞 |
2021-12-01 |
奇安信代碼安全實驗室 |
CVE-2021-43222 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-43222
|
 |
| 222 |
微軟Microsoft Message Queuing 信息泄露漏洞 |
2021-12-01 |
奇安信代碼安全實驗室 |
CVE-2021-43236 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-43236
|
 |
| 221 |
微軟iSNS 服務器內存損壞漏洞可導致RCE |
2021-12-01 |
奇安信代碼安全實驗室 |
CVE-2021-43215 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-43215
|
 |
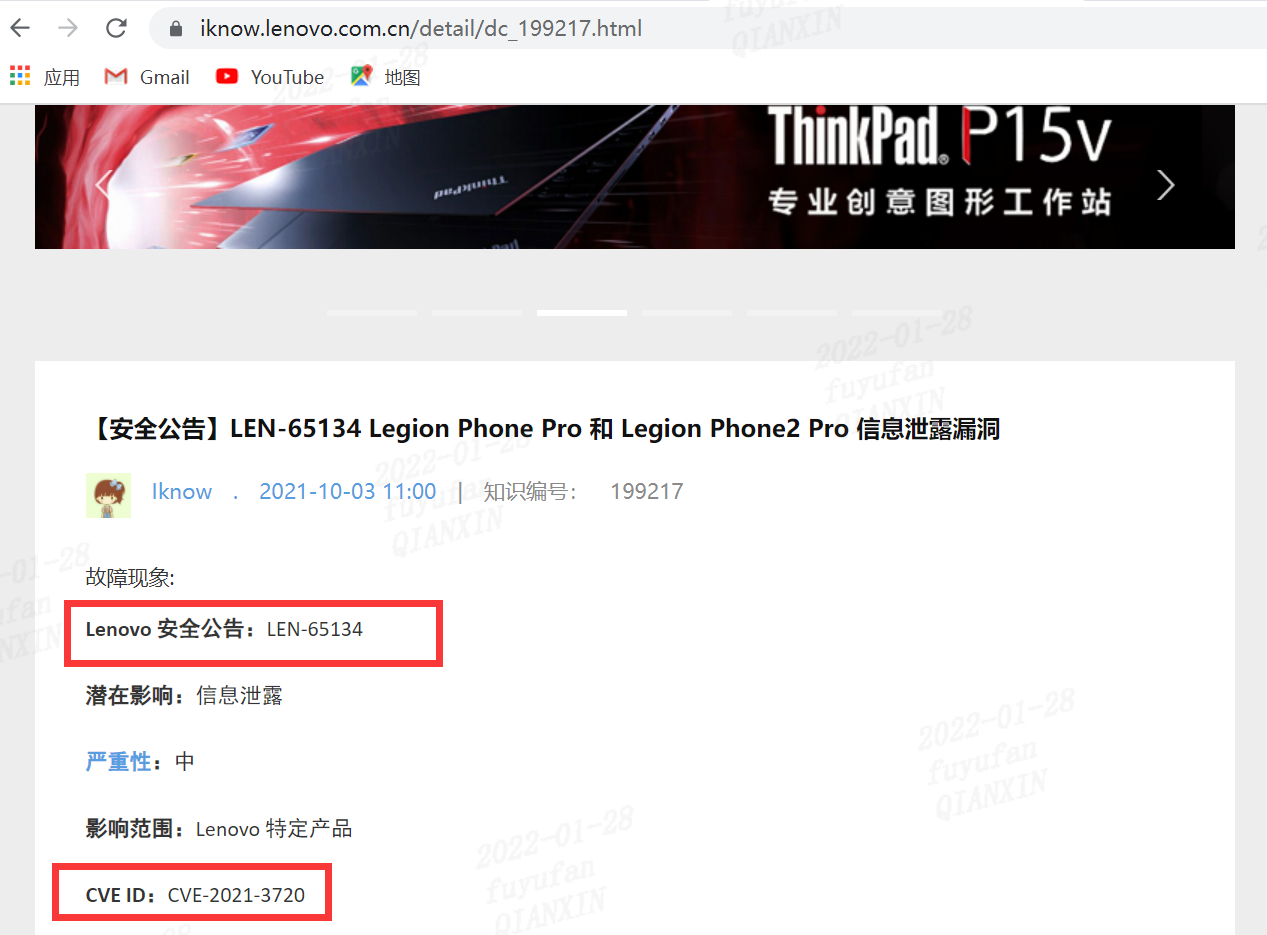
| 220 |
聯想手機:LEN-65134 Legion Phone Pro 和 Legion Phone2 Pro 信息泄露漏洞 |
2021-10-03 |
研究院 |
CVE-2021-3720 |
https://iknow.lenovo.com.cn/detail/dc_199217.html
|
 |
| 219 |
中興通訊一款手機的消息服務應用存在信息泄露漏洞 |
2021-09-24 |
研究院 |
CVE-2021-21742 |
https://support.zte.com.cn/support/news/LoopholeInfoDetail.aspx?newsId=1019064
|
 |
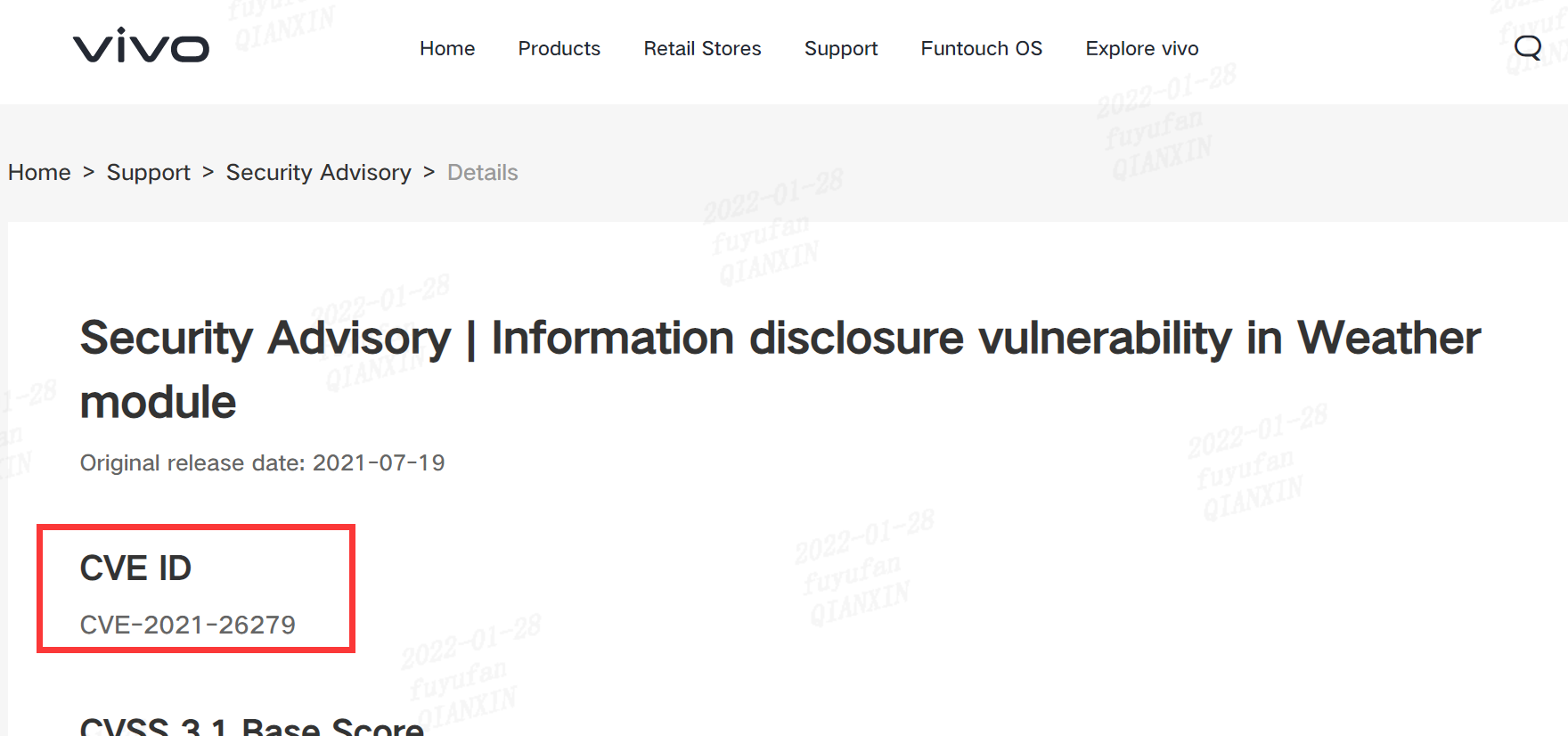
| 218 |
天氣模塊中的信息泄露漏洞 |
2021-07-19 |
研究院 |
CVE-2021-26279 |
https://www.vivo.com/en/support/security-advisory-detail?id=10
|
 |
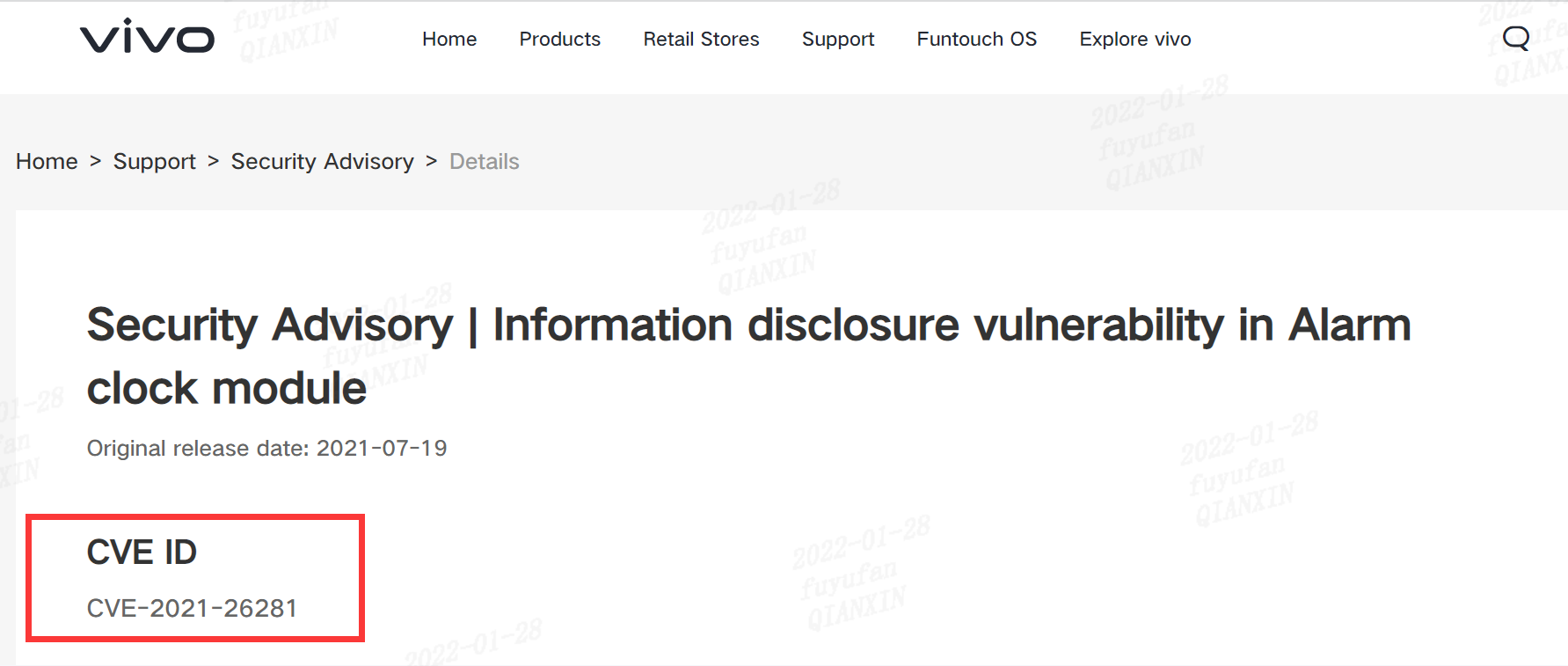
| 217 |
鬧鐘模塊中的信息泄露 |
2021-07-19 |
研究院 |
CVE-2021-26281 |
https://www.vivo.com/en/support/security-advisory-detail?id=9
|
 |
| 216 |
華為手機中的非標準化字段名稱 |
2021-09-01 |
研究院 |
CVE-2021-22486 |
https://consumer.huawei.com/gh/support/bulletin/2021/9/
https://device.harmonyos.com/cn/docs/security/update/security-bulletins-202108-0000001180965965
|
 |
| 215 |
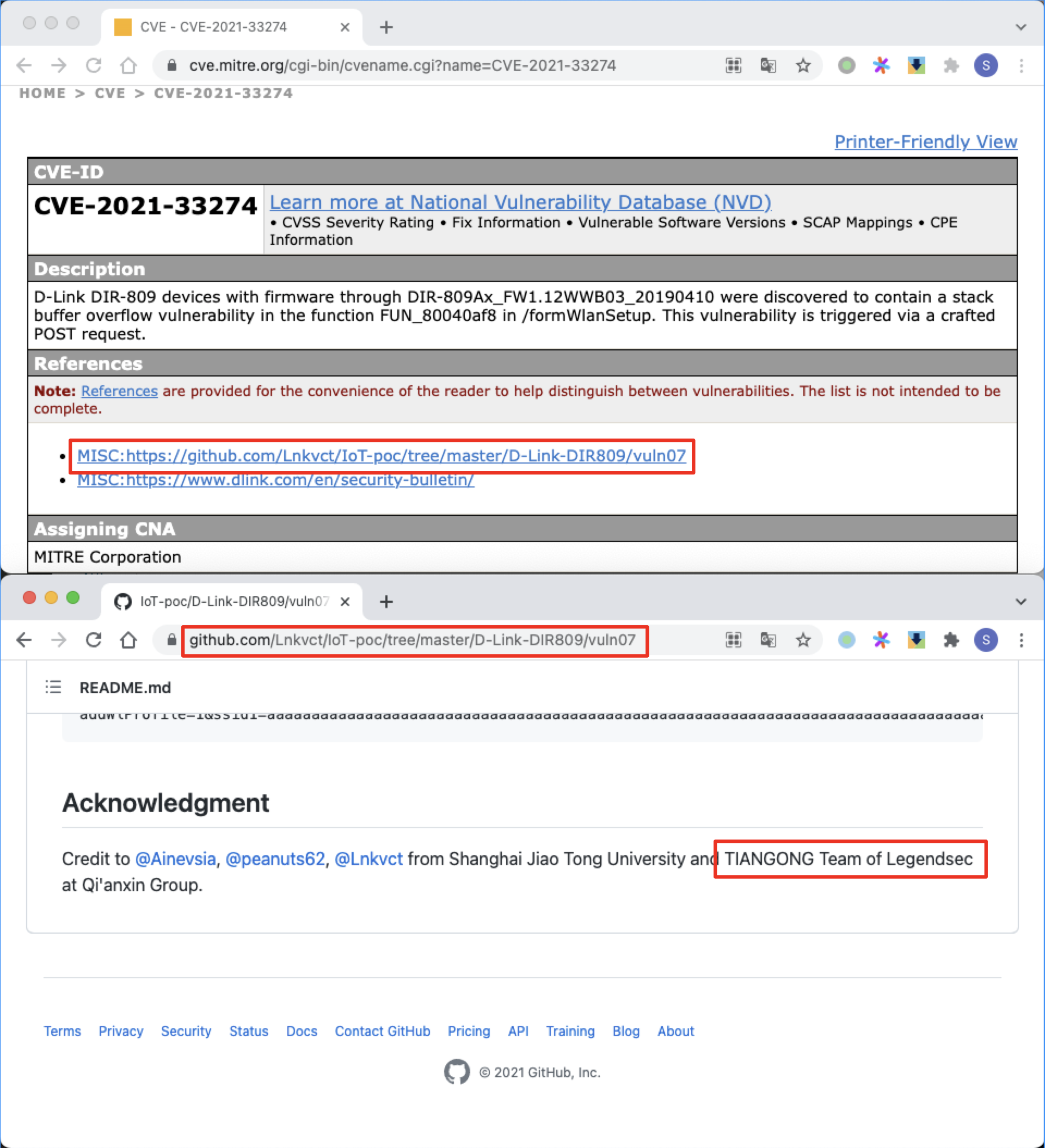
D-Link formWlanSetup 棧溢出 |
2021-05-20 |
研究院 |
CVE-2021-33274 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33274
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln07
|
 |
| 214 |
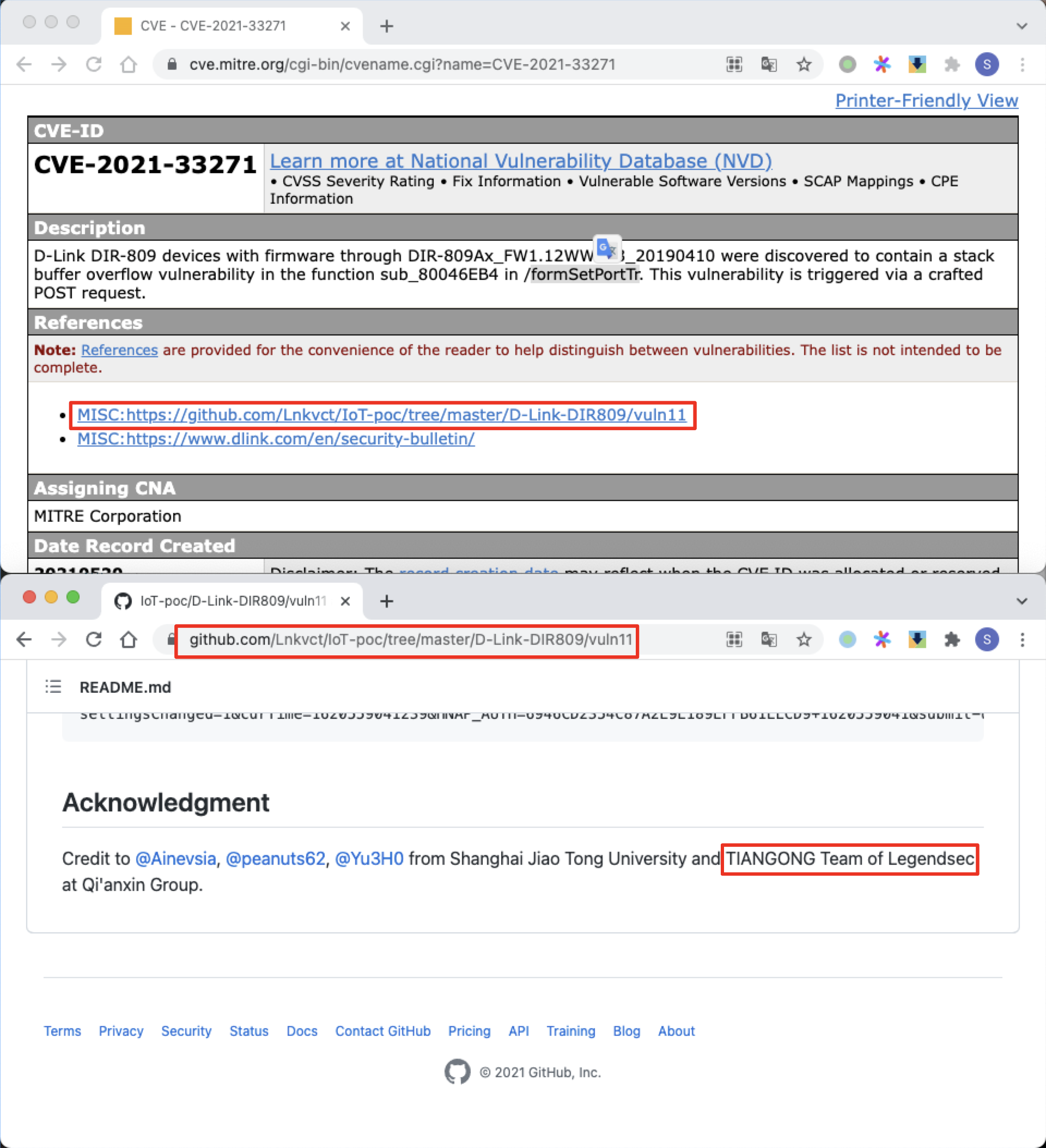
D-Link formSetPortTr 棧溢出 |
2021-05-20 |
研究院 |
CVE-2021-33271 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33271
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln11
|
 |
| 213 |
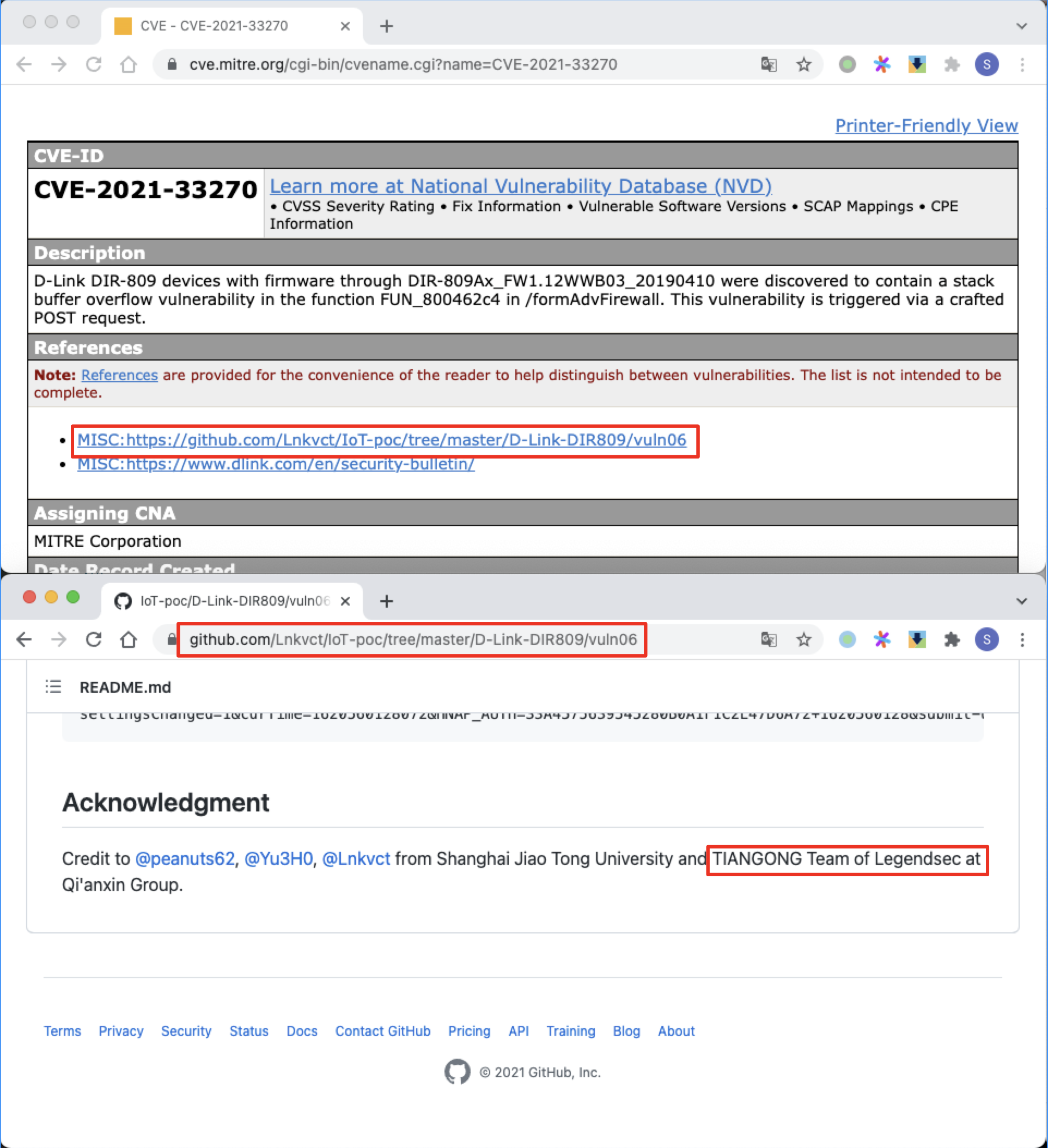
D-Link formAdvFirewall 棧溢出 |
2021-05-20 |
研究院 |
CVE-2021-33270 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33270
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln06
|
 |
| 212 |
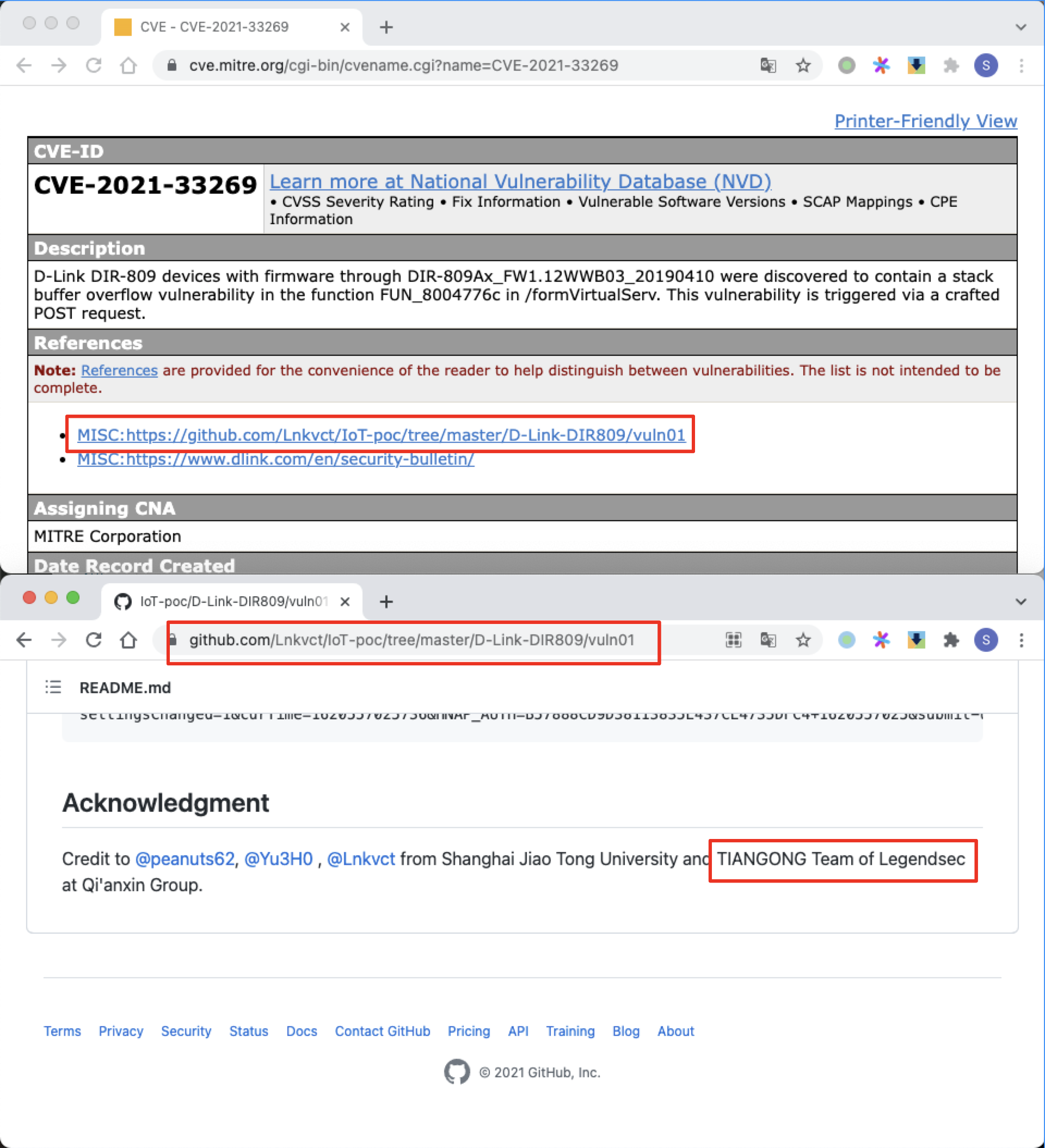
D-Link formVirtualServ 棧溢出 |
2021-05-20 |
研究院 |
CVE-2021-33269 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33269
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln01
|
 |
| 211 |
D-Link fromLogin 棧溢出 |
2021-05-20 |
奇安信技術研究院 |
CVE-2021-33268 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33268
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln03
|
 |
| 210 |
D-Link formStaticDHCP 棧溢出 |
2021-05-20 |
奇安信技術研究院 |
CVE-2021-33267 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33267
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln02
|
 |
| 209 |
D-Link formVirtualApp 棧溢出 |
2021-05-20 |
奇安信技術研究院 |
CVE-2021-33266 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33266
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln04
|
 |
| 208 |
D-Link formSetPortTr 棧溢出 |
2021-05-20 |
奇安信技術研究院 |
CVE-2021-33265 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-33265
https://github.com/Lnkvct/IoT-poc/tree/master/D-Link-DIR809/vuln05
|
 |
| 207 |
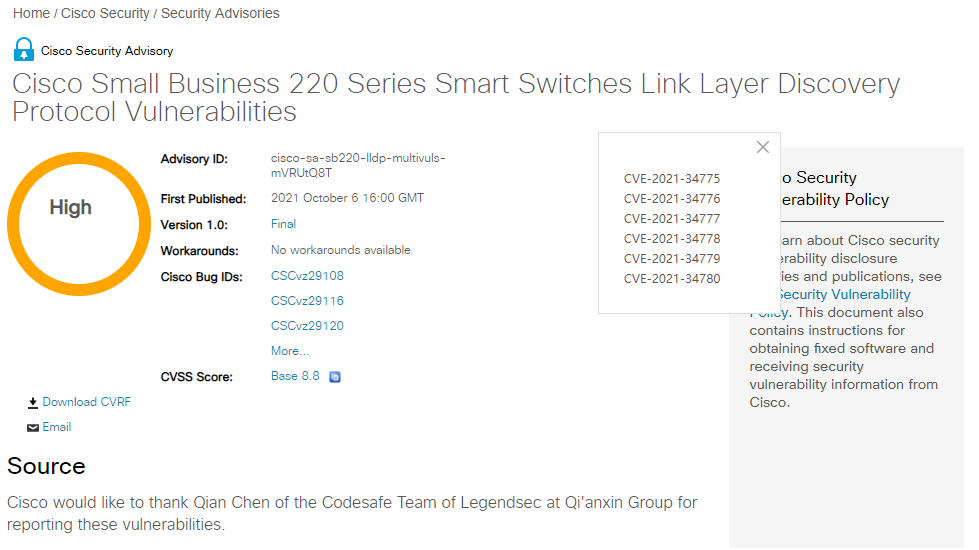
思科220系列小型交換機LLDP協議拒絕服務 |
2021-10-17 |
奇安信代碼安全實驗室 |
CVE-2021-34780 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 206 |
思科220系列小型交換機LLDP協議拒絕服務 |
2021-10-07 |
奇安信代碼安全實驗室 |
CVE-2021-34779 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 205 |
思科220系列小型交換機LLDP數據庫損壞漏洞 |
2021-10-02 |
奇安信代碼安全實驗室 |
CVE-2021-34778 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 204 |
思科220系列小型交換機LLDP數據庫損壞漏洞 |
2021-10-02 |
奇安信代碼安全實驗室 |
CVE-2021-34777 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 203 |
思科220系列小型交換機LLDP數據庫損壞漏洞 |
2021-10-02 |
奇安信代碼安全實驗室 |
CVE-2021-34776 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 202 |
思科220系列小型交換機LLDP數據庫損壞漏洞 |
2021-10-01 |
奇安信代碼安全實驗室 |
CVE-2021-34775 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb220-lldp-multivuls-mVRUtQ8T
|
 |
| 201 |
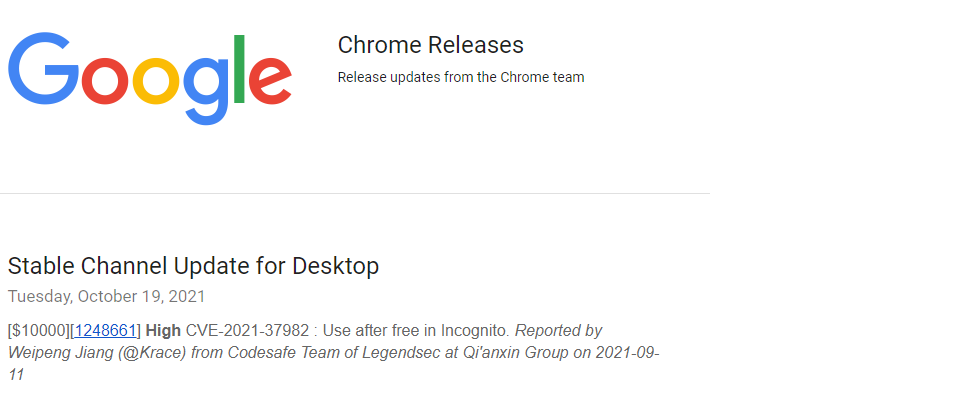
谷歌 Chrome Incognito 中的釋放後使用漏洞 |
2021-10-19 |
奇安信代碼安全實驗室 |
CVE-2021-37982 |
https://chromereleases.googleblog.com/2021/10/stable-channel-update-for-desktop_19.html
|
 |
| 200 |
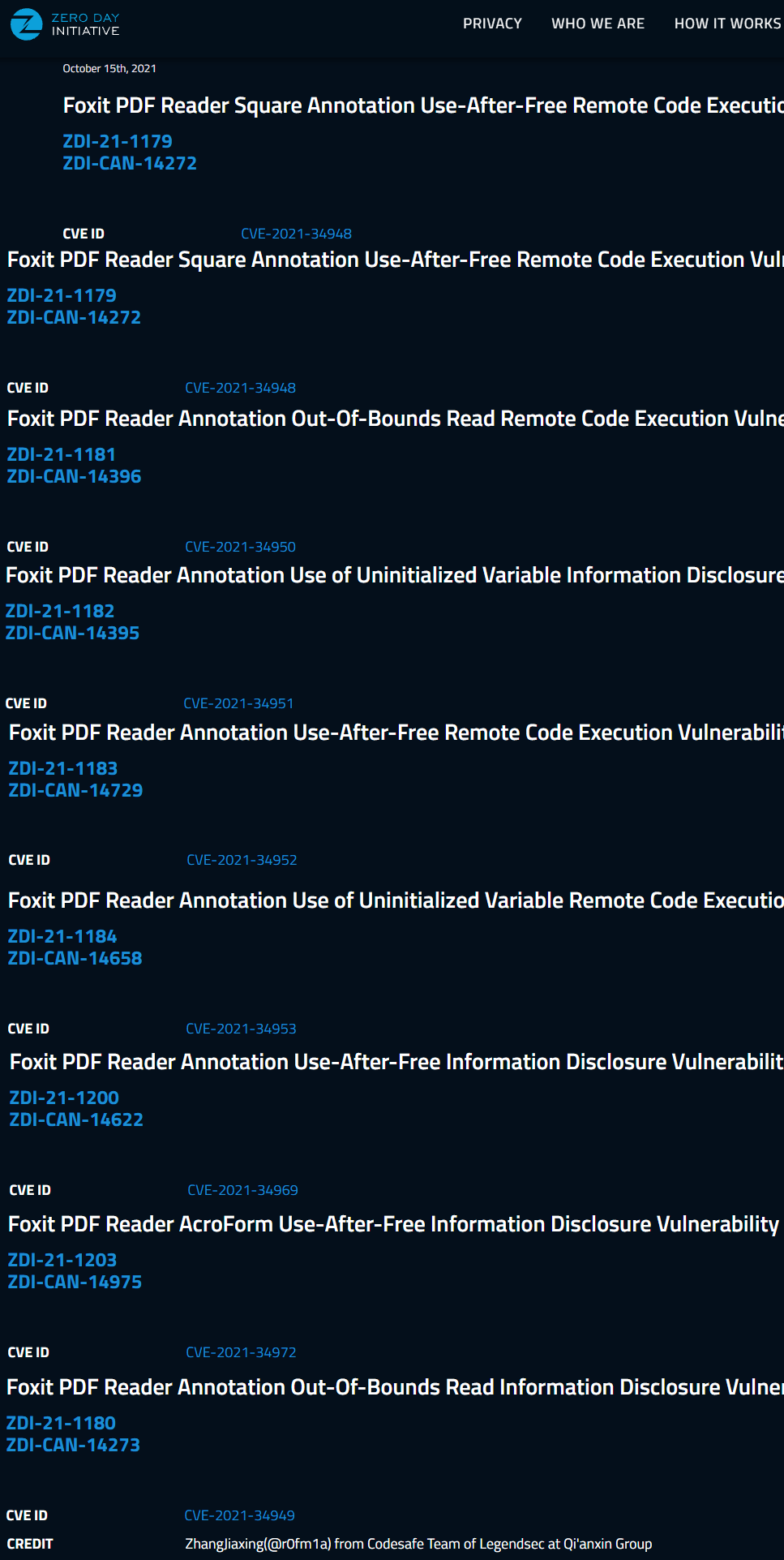
Foxit PDF Reader Annotation 釋放後使用信息泄露漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34972 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1203/
|
 |
| 199 |
Foxit PDF Reader Annotation 釋放後使用信息泄露漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34969 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1200/
|
 |
| 198 |
Foxit PDF Reader Annotation 使用未初始化變量信息泄露漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34953 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1184/
|
 |
| 197 |
Foxit PDF Reader Annotation 釋放後使用遠程代碼執行漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34952 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1183/
|
 |
| 196 |
Foxit PDF Reader Annotation 使用未初始化變量信息泄露漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34951 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1182/
|
 |
| 195 |
Foxit PDF Reader Square Annotation 界外讀遠程代碼執行漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34950 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1181/
|
 |
| 194 |
Foxit PDF Reader Annotation界外讀信息泄露漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34949 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1180/
|
 |
| 193 |
Foxit PDF Reader Square Annotation 釋放後使用遠程代碼執行漏洞 |
2021-10-09 |
奇安信代碼安全實驗室 |
CVE-2021-34948 |
https://www.zerodayinitiative.com/advisories/ZDI-21-1179/
|
 |
| 192 |
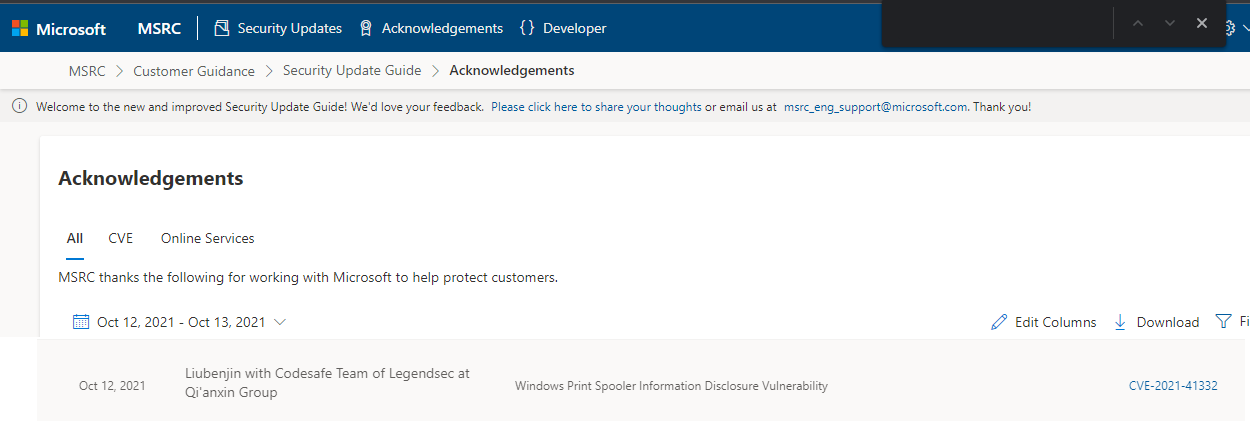
Windows Print Spooler 信息泄露漏洞 |
2021-10-01 |
奇安信代碼安全實驗室 |
CVE-2021-41332 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-41332
|
 |
| 191 |
谷歌Chrome Safe Browsing 中的釋放後使用漏洞 |
2021-09-01 |
奇安信代碼安全實驗室 |
CVE-2021-37974 |
https://chromereleases.googleblog.com/2021/09/stable-channel-update-for-desktop_30.html
|
 |
| 190 |
施耐德電氣Modicon PAC Controllers and PLC Simulator for EcoStruxure™ Control Expert and EcoStruxure™ Process Expert 空解指針解引用漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-22792 |
https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-222-04
|
 |
| 189 |
施耐德電氣Modicon PAC Controllers and PLC Simulator for EcoStruxure™ Control Expert and EcoStruxure™ Process Expert 界外寫漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-22791 |
https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-222-04
|
 |
| 188 |
施耐德電氣Modicon PAC Controllers and PLC Simulator for EcoStruxure™ Control Expert and EcoStruxure™ Process Expert 界外讀漏洞 |
2021-08-19 |
奇安信代碼安全實驗室 |
CVE-2021-22790 |
https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-222-04
|
 |
| 187 |
施耐德電氣Modicon PAC Controllers and PLC Simulator for EcoStruxure™ Control Expert and EcoStruxure™ Process Expert 內存緩衝區邊界內操作限制不當 |
2021-08-19 |
奇安信代碼安全實驗室 |
CVE-2021-22789 |
https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-222-04
|
 |
| 186 |
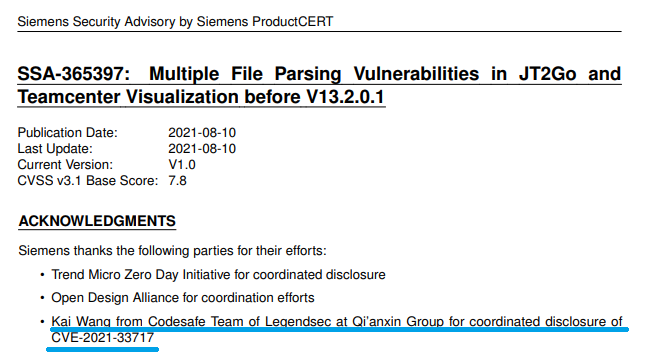
西門子 Siemens JT2Go and Teamcenter Visualization 13.2.0.0及之前版本中存在CGM 文件空指針解引用漏洞 |
2021-08-19 |
奇安信代碼安全實驗室 |
CVE-2021-33717 |
https://cert-portal.siemens.com/productcert/pdf/ssa-365397.pdf
|
 |
| 185 |
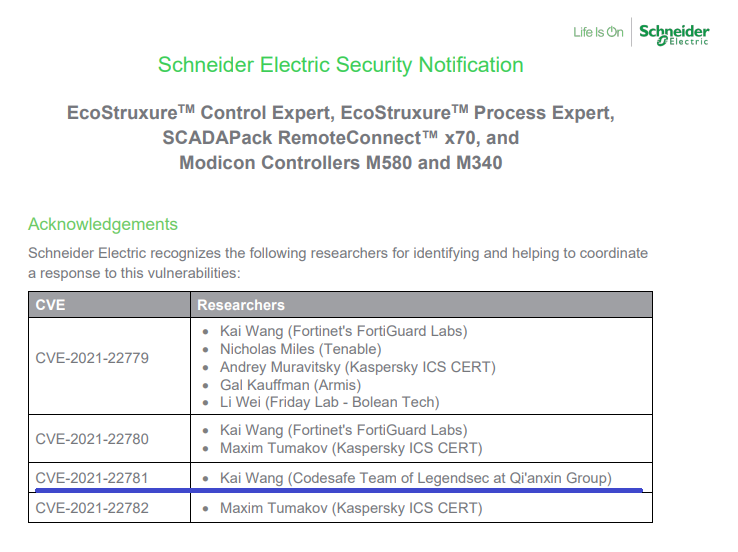
施耐德電氣EcoStruxureTM Control Expert, EcoStruxureTM Process Expert, SCADAPack RemoteConnect™ x70, and Modicon Controllers M580 and M340憑據保護不充分 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-22781 |
https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-194-01
|
 |
| 184 |
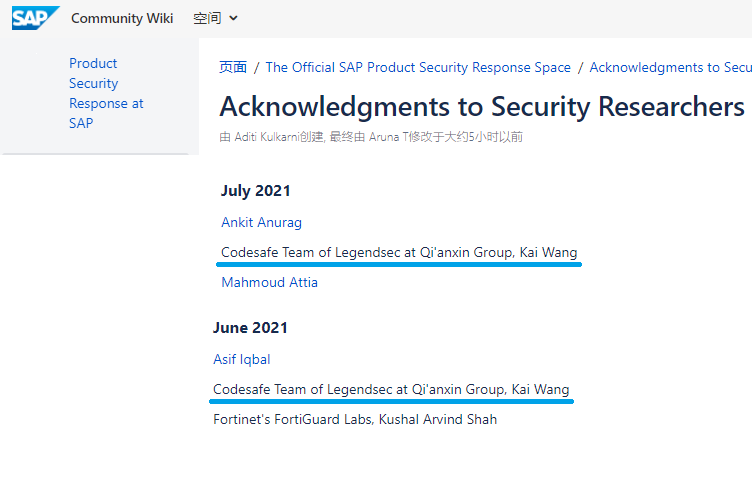
SAP 3D 可視化企業視圖版本9.1中的輸入驗證不當問題 |
2021-06-30 |
奇安信代碼安全實驗室 |
CVE-2021-33680 |
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=451071888
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=580617506
|
 |
| 183 |
SAP 3D 可視化企業視圖版本9.0中的輸入驗證不當問題 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-33681 |
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=580617506
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=451071888
|
 |
| 182 |
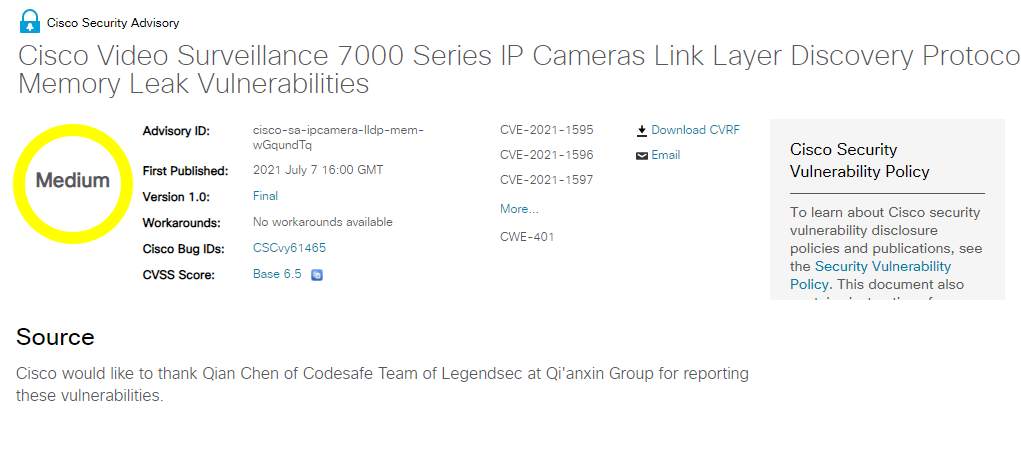
思科視頻監控7003系列 IP 攝像頭固件LLDP內存泄露漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-1598 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipcamera-lldp-mem-wGqundTq
|
 |
| 181 |
思科視頻監控7001系列 IP 攝像頭固件LLDP內存泄露漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-1597 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipcamera-lldp-mem-wGqundTq
|
 |
| 180 |
思科視頻監控7001系列 IP 攝像頭固件LLDP內存泄露漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-1596 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipcamera-lldp-mem-wGqundTq
|
 |
| 179 |
思科視頻監控7000系列 IP 攝像頭固件LLDP內存泄露漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-1595 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipcamera-lldp-mem-wGqundTq
|
 |
| 178 |
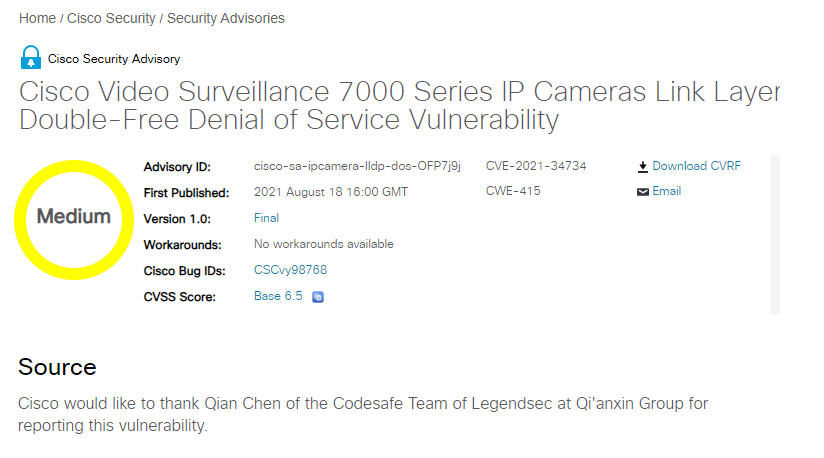
思科視頻監控7000系列 IP 攝像頭固件LLDP實現中的雙重釋放拒絕服務漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-34734 |
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ipcamera-lldp-dos-OFP7j9j
|
 |
| 177 |
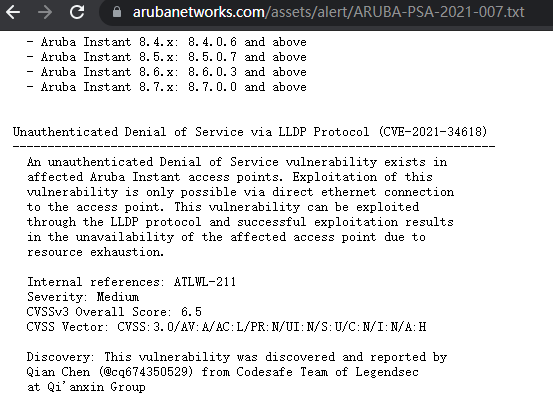
Aruba Instant 訪問點中的未認證拒絕服務漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-34618 |
https://www.arubanetworks.com/assets/alert/ARUBA-PSA-2021-007.txt
|
 |
| 176 |
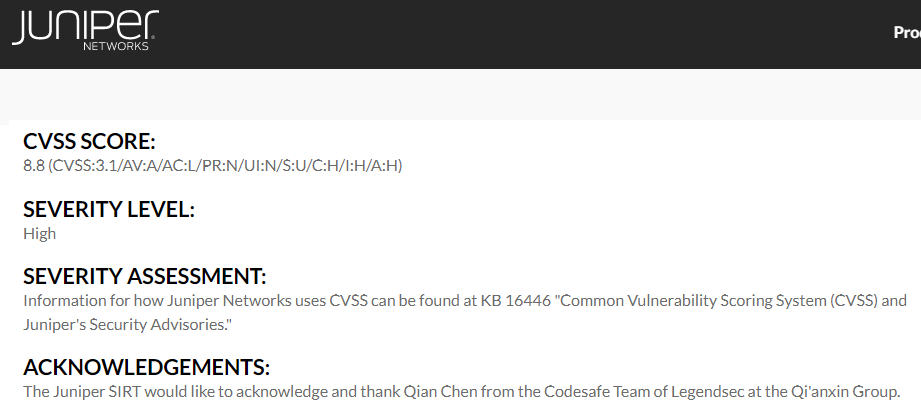
Juniper Networks Junos OS and Junos OS Evolved 的l2cpd中存在界外讀漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-0277 |
https://kb.juniper.net/InfoCenter/index?page=content&id=JSA11181&cat=SIRT_1&actp=LIST
|
 |
| 175 |
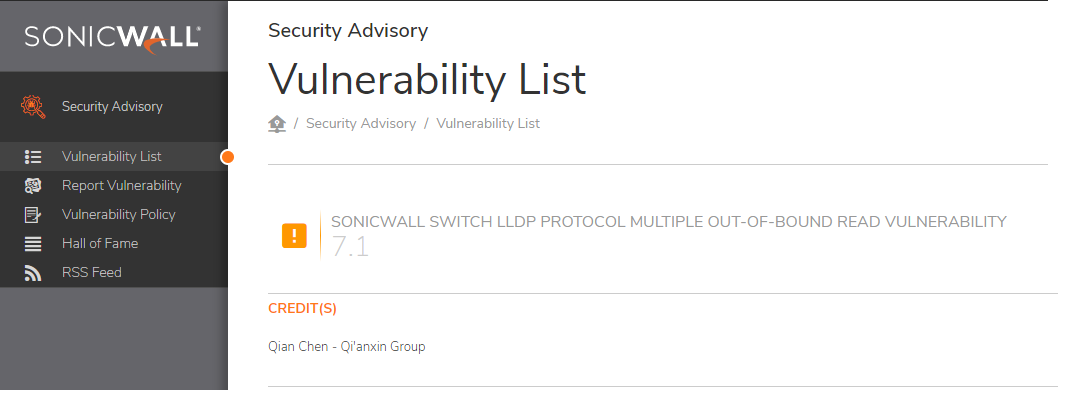
SonicWall 交換機中的界外讀漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-20024 |
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0011
|
 |
| 174 |
QNAP某些交換機中存在界外讀漏洞 |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-20024 |
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0011
|
 |
| 173 |
Chrome Permissions 中的使用後釋放漏洞 |
2021-09-19 |
奇安信代碼安全實驗室 |
CVE-2021-30629 |
https://chromereleases.googleblog.com/2021/09/stable-channel-update-for-desktop.html
|
 |
| 172 |
UI 框架中的釋放後使用漏洞 |
2021-05-01 |
奇安信代碼安全實驗室 |
CVE-2021-30579 |
https://chromereleases.googleblog.com/search?updated-max=2021-07-23T18:00:00-07:00&max-results=7&start=21&by-date=false
|
 |
| 171 |
Autofill 中的釋放後使用漏洞 |
2021-05-01 |
奇安信代碼安全實驗室 |
CVE-2021-30572 |
https://chromereleases.googleblog.com/search?updated-max=2021-07-23T18:00:00-07:00&max-results=7&start=21&by-date=false
|
 |
| 170 |
Chrome Permissions 中的使用後釋放漏洞 |
2021-09-01 |
奇安信代碼安全實驗室 |
CVE-2021-30607 |
https://chromereleases.googleblog.com/2021/08/stable-channel-update-for-desktop_31.html
|
 |
| 169 |
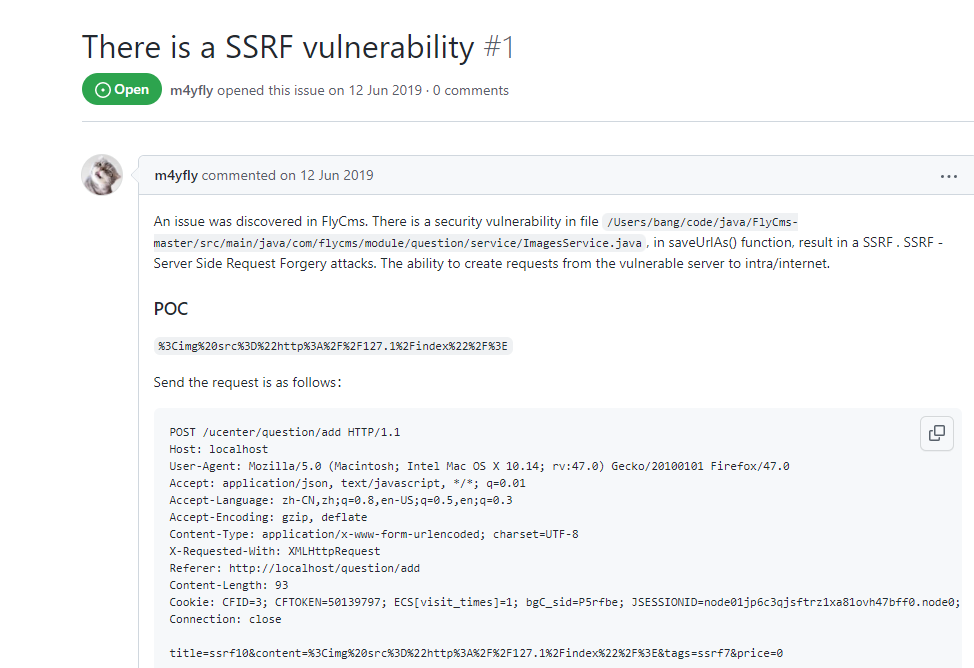
XSS in mblog |
2021-04-15 |
奇安信技術研究院 |
CVE-2020-19619 |
https://github.com/langhsu/mblog/issues/27
|
 |
| 168 |
XSS in mblog |
2021-04-15 |
奇安信技術研究院 |
CVE-2020-19618 |
https://github.com/langhsu/mblog/issues/27
|
 |
| 167 |
XSS in mblog |
2021-04-15 |
奇安信技術研究院 |
CVE-2020-19617 |
https://github.com/langhsu/mblog/issues/27
|
 |
| 166 |
XSS in mblog |
2021-04-15 |
奇安信技術研究院 |
CVE-2020-19616 |
https://github.com/langhsu/mblog/issues/27
|
 |
| 165 |
SSRF in FlyCMS |
2021-04-15 |
奇安信技術研究院 |
CVE-2020-19613 |
https://github.com/sunkaifei/FlyCms/issues/1
|
 |
| 164 |
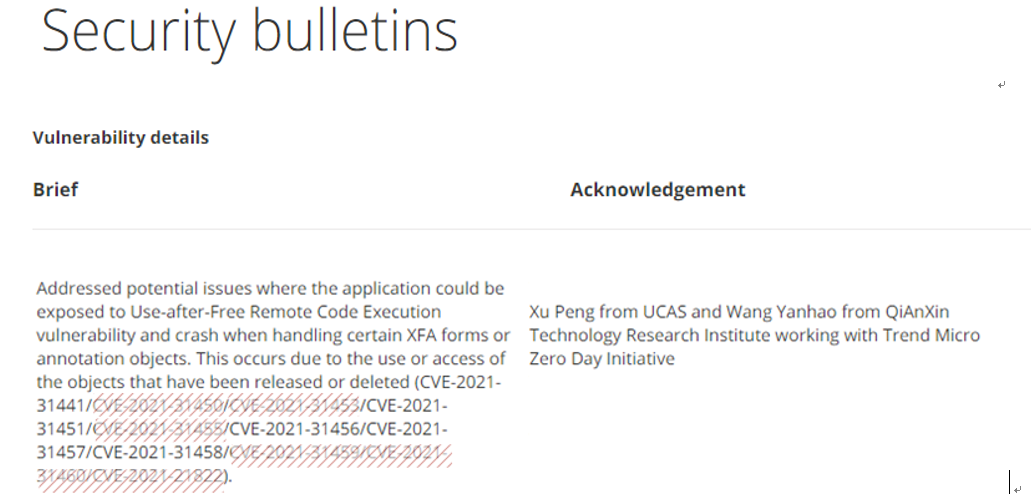
Foxit Reader and Foxit PhantomPDF |
2021-04-15 |
奇安信技術研究院 |
CVE-2021-31458 |
https://www.foxitsoftware.com/support/security-bulletins.html
|
 |
| 163 |
Foxit Reader and Foxit PhantomPDF |
2021-04-15 |
奇安信技術研究院 |
CVE-2021-31457 |
https://www.foxitsoftware.com/support/security-bulletins.html
|
 |
| 162 |
Foxit Reader and Foxit PhantomPDF |
2021-04-15 |
奇安信技術研究院 |
CVE-2021-31451 |
https://www.foxitsoftware.com/support/security-bulletins.html
|
 |
| 161 |
Foxit Reader and Foxit PhantomPDF |
2021-04-15 |
奇安信技術研究院 |
CVE-2021-31456 |
https://www.foxitsoftware.com/support/security-bulletins.html
|
 |
| 160 |
Foxit Reader and Foxit PhantomPDF |
2021-11-15 |
奇安信技術研究院 |
CVE-2021-31441 |
https://www.foxitsoftware.com/support/security-bulletins.html
|
 |
| 159 |
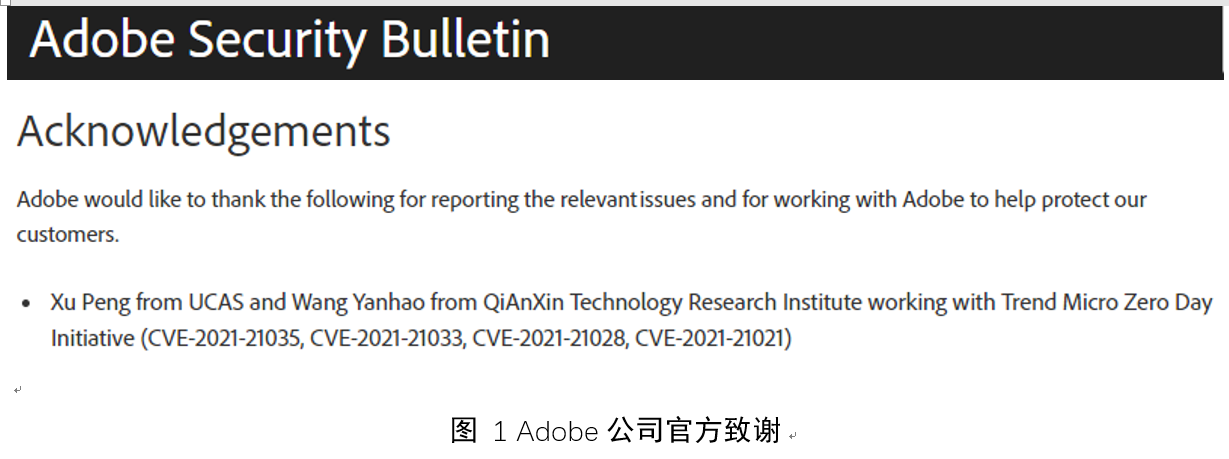
Adobe Acrobat and Reader |
2021-03-10 |
奇安信技術研究院 |
CVE-2021-21021 |
https://helpx.adobe.com/security/products/acrobat/apsb21-09.html
|
 |
| 158 |
Adobe Acrobat and Reader |
2021-03-10 |
奇安信技術研究院 |
CVE-2021-21028 |
https://helpx.adobe.com/security/products/acrobat/apsb21-09.html
|
 |
| 157 |
Adobe Acrobat and Reader |
2021-03-10 |
奇安信技術研究院 |
CVE-2021-21033 |
https://helpx.adobe.com/security/products/acrobat/apsb21-09.html
|
 |
| 156 |
Adobe Acrobat and Reader |
2021-03-10 |
奇安信技術研究院 |
CVE-2021-21035 |
https://helpx.adobe.com/security/products/acrobat/apsb21-09.html
|
 |
| 155 |
Windows TCP/IP 遠程代碼執行漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-26424 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26424
|
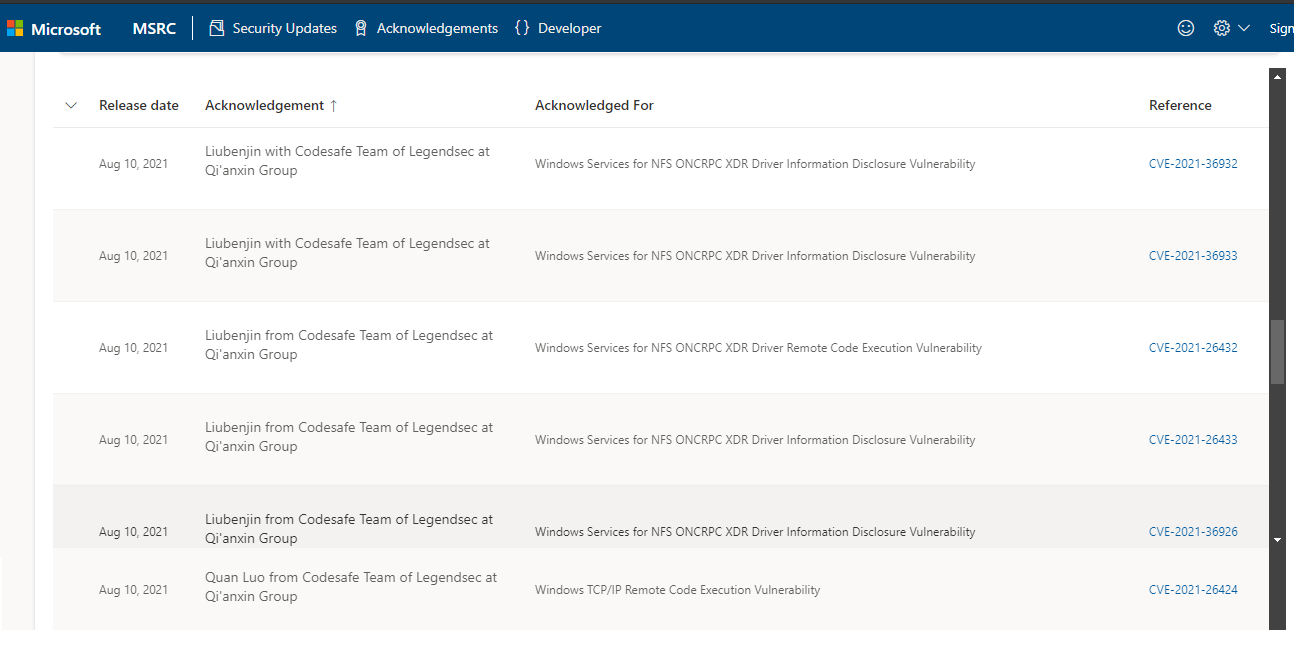 |
| 154 |
Windows Services for NFS ONCRPC XDR Drive 信息泄露漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-36926 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36926
|
 |
| 153 |
Windows Services for NFS ONCRPC XDR Drive 信息泄露漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-26433 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26433
|
 |
| 152 |
Windows Services for NFS ONCRPC XDR Drive 遠程代碼執行漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-26432 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26432
|
 |
| 151 |
Windows Services for NFS ONCRPC XDR Drive 信息泄露漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-36933 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36933
|
 |
| 150 |
Windows Services for NFS ONCRPC XDR Drive 信息泄露漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-36932 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36932
|
 |
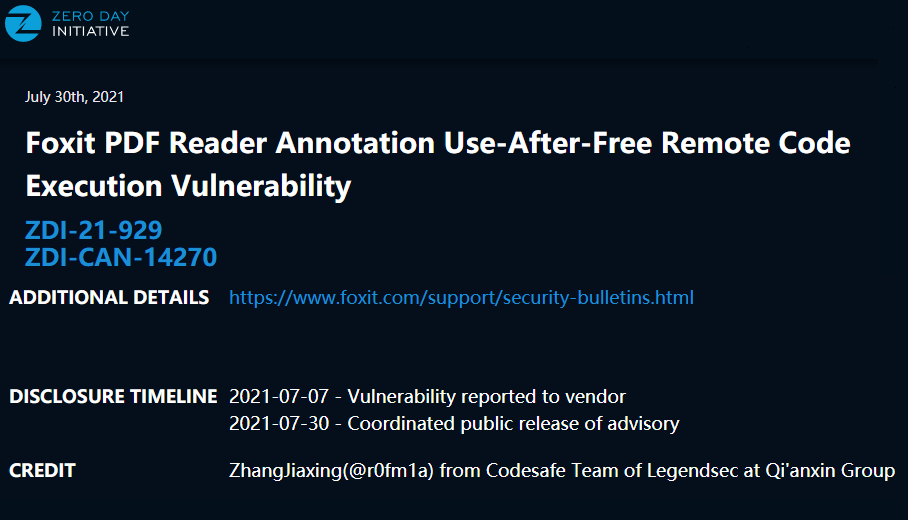
| 149 |
Foxit PDF Reader Annotation 釋放後使用遠程代碼執行漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-34847 |
https://www.zerodayinitiative.com/advisories/ZDI-21-929/
|
 |
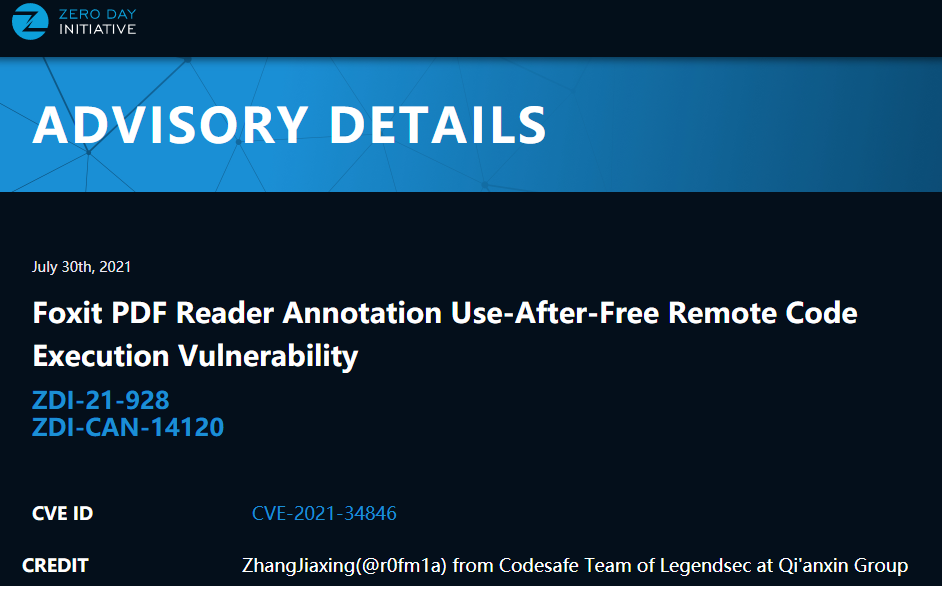
| 148 |
Foxit PDF Reader Annotation 釋放後使用遠程代碼執行漏洞 |
2021-08-01 |
奇安信代碼安全實驗室 |
CVE-2021-34846 |
https://www.zerodayinitiative.com/advisories/ZDI-21-928/
|
 |
| 147 |
Windows DNS 服務器拒絕服務漏洞 (RCE) |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-34444 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34444
|
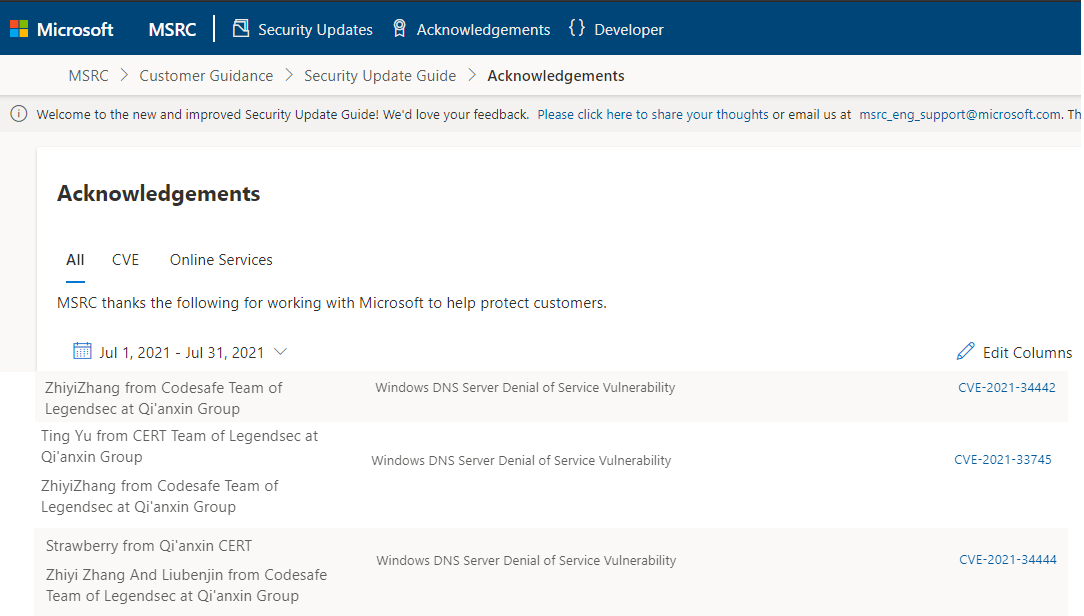 |
| 146 |
Windows DNS 服務器拒絕服務漏洞 (RCE) |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-34442 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34442
|
 |
| 145 |
Windows DNS 服務器拒絕服務漏洞 (RCE) |
2021-07-01 |
奇安信代碼安全實驗室 |
CVE-2021-33745 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-33745
|
 |
| 144 |
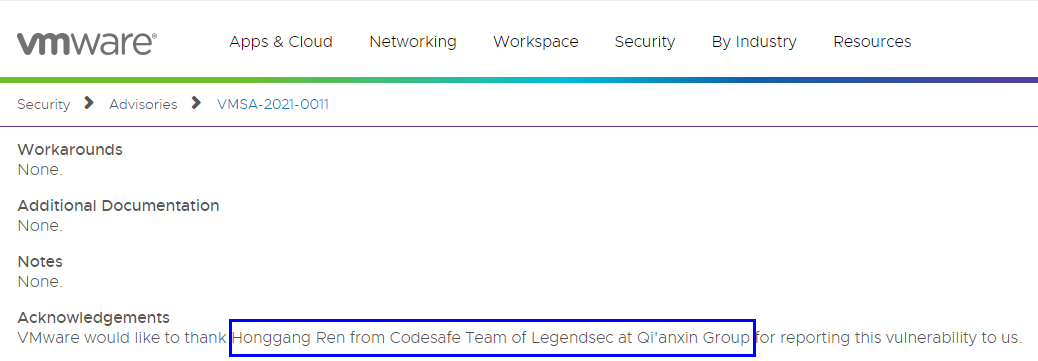
VMware Tools for Windows 的VM3DMP中存在拒絕服務漏洞 |
2021-06-01 |
奇安信代碼安全實驗室 |
CVE-2021-21997 |
https://www.vmware.com/security/advisories/VMSA-2021-0011.html
|
 |
| 143 |
RedHat coders/tiff.c 中ReadTIFFImage()中的ImageMagick存在堆緩衝區溢出漏洞 |
2021-06-01 |
奇安信代碼安全實驗室 |
CVE-2021-3610 |
https://bugzilla.redhat.com/show_bug.cgi?id=1973689
|
 |
| 142 |
谷歌Chrome Aura 組件中的競爭條件漏洞 |
2021-05-02 |
奇安信代碼安全實驗室 |
CVE-2021-30510 |
https://chromereleases.googleblog.com/2021/05/stable-channel-update-for-desktop.html
|
 |
| 141 |
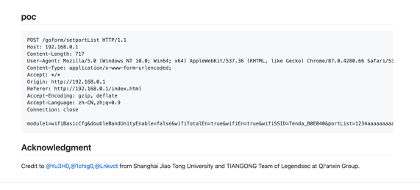
Tenda eCos遠程代碼執行漏洞4 |
2021-05-03 |
技術研究院天工實驗室 |
CVE-2021-31758 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-31758
|
 |
| 140 |
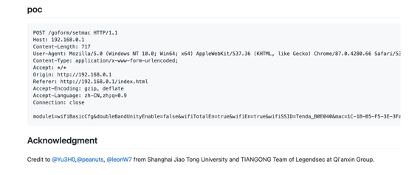
Tenda eCos遠程代碼執行漏洞3 |
2021-05-03 |
技術研究院天工實驗室 |
CVE-2021-31755 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-31755
|
 |
| 139 |
Tenda eCos遠程代碼執行漏洞2 |
2021-05-02 |
技術研究院天工實驗室 |
CVE-2021-31757 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-31757
|
 |
| 138 |
Tenda eCos遠程代碼執行漏洞1 |
2021-05-02 |
技術研究院天工實驗室 |
CVE-2021-31756 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-31756
|
 |
| 137 |
Apache Solr服務器端請求偽造漏洞 |
2021-04-20 |
奇安信CERT |
CVE-2021-27905 |
https://solr.apache.org/security.html#cve-2021-27905-ssrf-vulnerability-with-the-replication-handler
|
 |
| 136 |
Windows DNS 信息泄露漏洞 |
2021-04-14 |
奇安信代碼安全實驗室 |
CVE-2021-28323 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-28323
|
 |
| 135 |
Windows DNS 信息泄露漏洞 |
2021-04-14 |
奇安信代碼安全實驗室 |
CVE-2021-28328 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-28328
|
 |
| 134 |
Windows Network File System 遠程代碼執行漏洞 |
2021-04-14 |
奇安信代碼安全實驗室 |
CVE-2021-28445 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-28445
|
 |
| 133 |
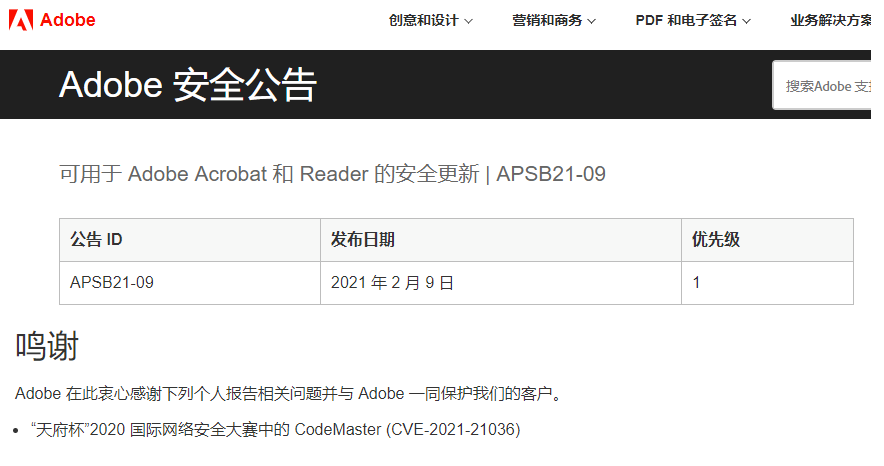
Adobe Acrobat 和 Reader 的 Windows 和 macOS 版任意代碼執行漏洞 |
2021-02-09 |
奇安信代碼安全實驗室 |
CVE-2021-21036 |
https://helpx.adobe.com/cn/security/products/acrobat/apsb21-09.html
|
 |
| 132 |
谷歌 Chrome Aura 組件中的釋放後使用漏洞 |
2021-03-31 |
奇安信代碼安全實驗室 |
CVE-2021-21199 |
https://chromereleases.googleblog.com/2021/03/stable-channel-update-for-desktop_30.html
|
 |
| 131 |
微軟DNS服務器遠程代碼執行漏洞 |
2021-02-10 |
奇安信代碼安全實驗室 |
CVE-2021-24078 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24078
|
 |
| 130 |
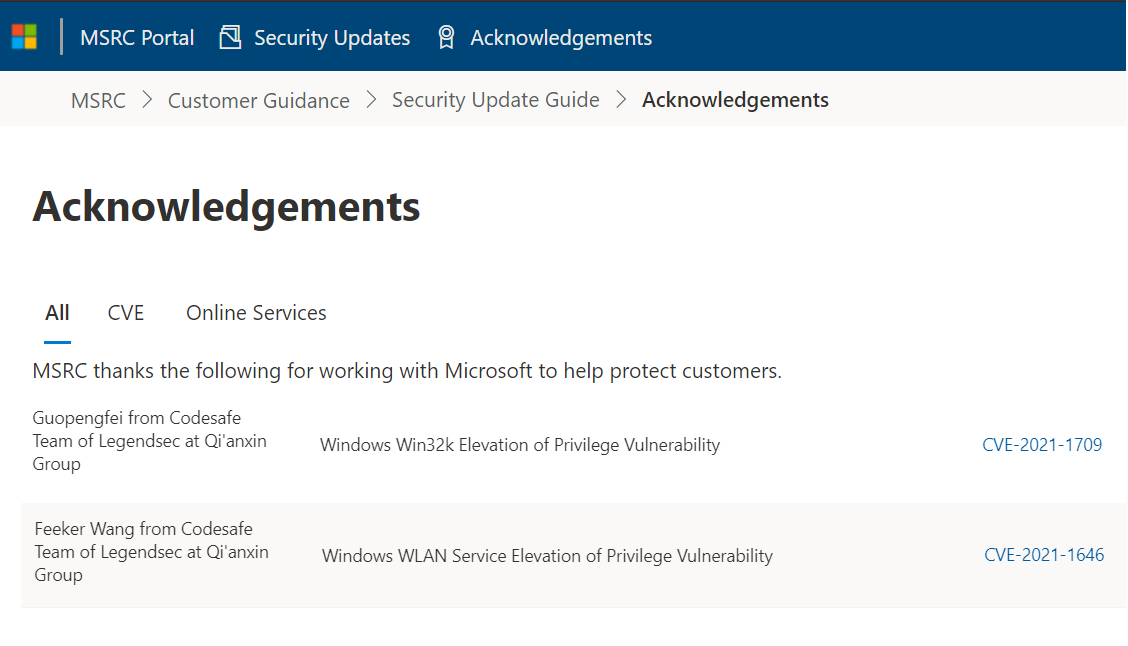
微軟Windows WLAN 服務提權漏洞 |
2021-01-13 |
奇安信代碼安全實驗室 |
CVE-2021-1646 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1646
|
 |
| 129 |
微軟Windows Win32k 提權漏洞 |
2021-01-13 |
奇安信代碼安全實驗室 |
CVE-2021-1709 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1709
|
 |
| 128 |
谷歌 Chrome自動填充組件中的沙箱外使用後釋放漏洞 |
2021-01-07 |
奇安信代碼安全實驗室 |
CVE-2020-21106 |
https://chromereleases.googleblog.com/
|
 |
| 127 |
Microsoft Exchange遠程代碼執行漏洞 |
2020-12-09 |
奇安信A-TEAM |
CVE-2020-17144 |
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-17144
|
 |
| 126 |
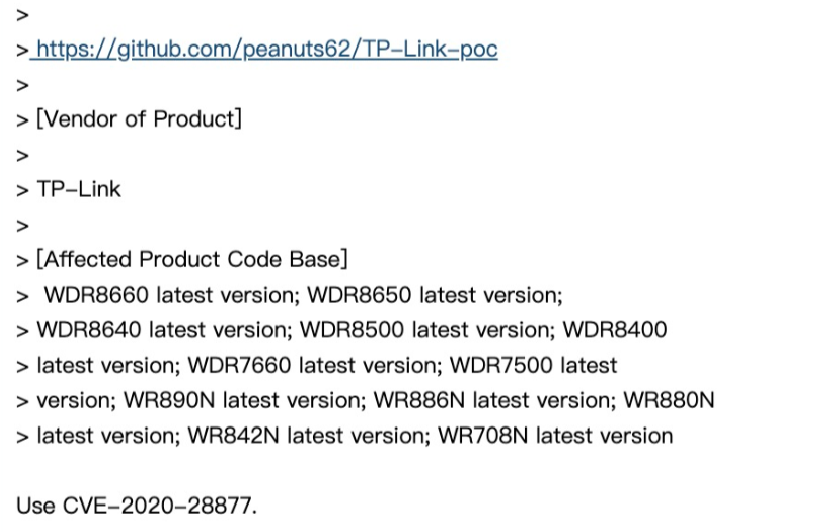
TP-Link 16款VxWorks路由器設備緩衝區溢出漏洞 |
2020-11-16 |
奇安信技術研究院 |
CVE-2020-28877 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28877
|
 |
| 125 |
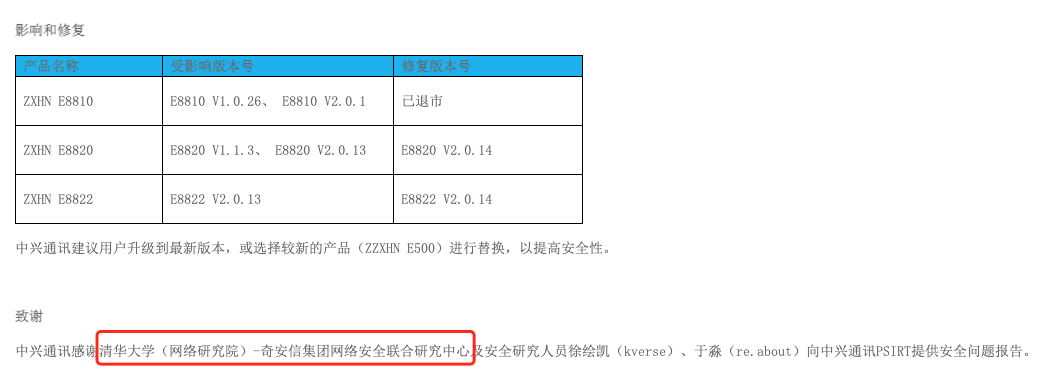
中興通訊E8810/E8820/E8822系列路由器存在信息泄露漏洞 |
2020-12-17 |
清華-奇安信聯合研究中心 |
CVE-2020-6882 |
http://support.zte.com.cn/support/news/LoopholeInfoDetail.aspx?newsId=1014182
|
 |
| 124 |
中興通訊E8810/E8820/E8822系列路由器存在MQTT拒絕服務漏洞 |
2020-12-17 |
清華-奇安信聯合研究中心 |
CVE-2020-6881 |
http://support.zte.com.cn/support/news/LoopholeInfoDetail.aspx?newsId=1014182
|
 |
| 123 |
Windows MSCTF Server信息泄漏漏洞 |
2020-11-11 |
奇安信代碼安全實驗室 |
CVE-2020-17030 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-17030
|
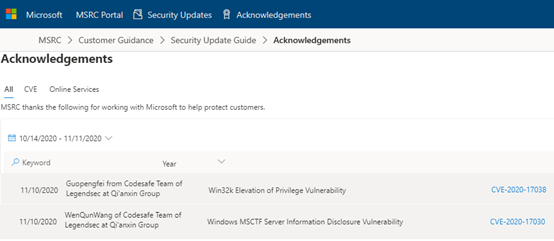 |
| 122 |
Win32k 提權漏洞 |
2020-11-11 |
奇安信代碼安全實驗室 |
CVE-2020-17038 |
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-17038
|
 |
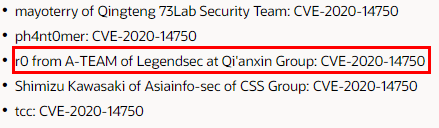
| 121 |
Oracle WebLogic Server遠程代碼執行漏洞 |
2020-11-01 |
奇安信A-TEAM |
cve-2020-14750 |
https://www.oracle.com/security-alerts/alert-cve-2020-14750.html
|
 |
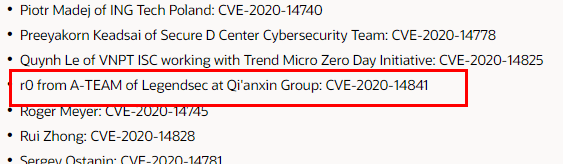
| 120 |
Oracle WebLogic Server 遠程代碼執行漏洞 |
2020-10-20 |
奇安信A-TEAM |
cve-2020-14841 |
https://www.oracle.com/security-alerts/cpuoct2020.html
|
 |
| 119 |
Oracle CVE-2020-14882 (WebLogic Server) 漏洞繞過 |
2020-11-02 |
奇安信代碼安全實驗室 |
CVE-2020-14750 |
https://www.oracle.com/security-alerts/alert-cve-2020-14750.html
|
 |
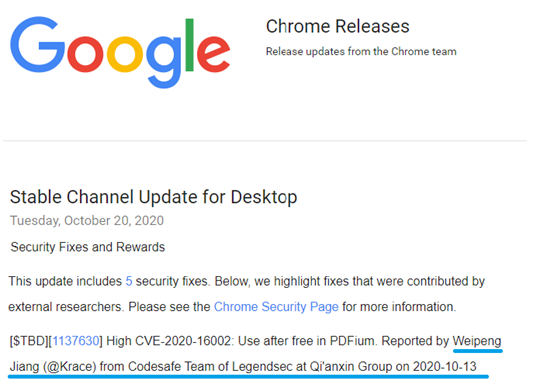
| 118 |
谷歌 PDFium 釋放後使用高危漏洞 |
2020-10-21 |
奇安信代碼安全實驗室 |
CVE-2020-16002 |
https://chromereleases.googleblog.com/2020/10/stable-channel-update-for-desktop_20.html
|
 |
| 117 |
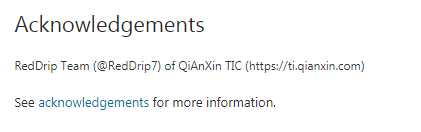
Windows Spoofing Vulnerability |
2020-10-14 |
奇安信威脅情報中心 |
CVE-2020-16922 |
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-16922
|
 |
| 116 |
Windows Text Services Framework信息泄漏漏洞 |
2020-10-14 |
奇安信代碼安全實驗室 |
CVE-2020-16921 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-16921
|
 |
| 115 |
Windows Application Compatibility Client Library 提權漏洞 |
2020-10-14 |
奇安信代碼安全實驗室 |
CVE-2020-16920 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-16920
|
 |
| 114 |
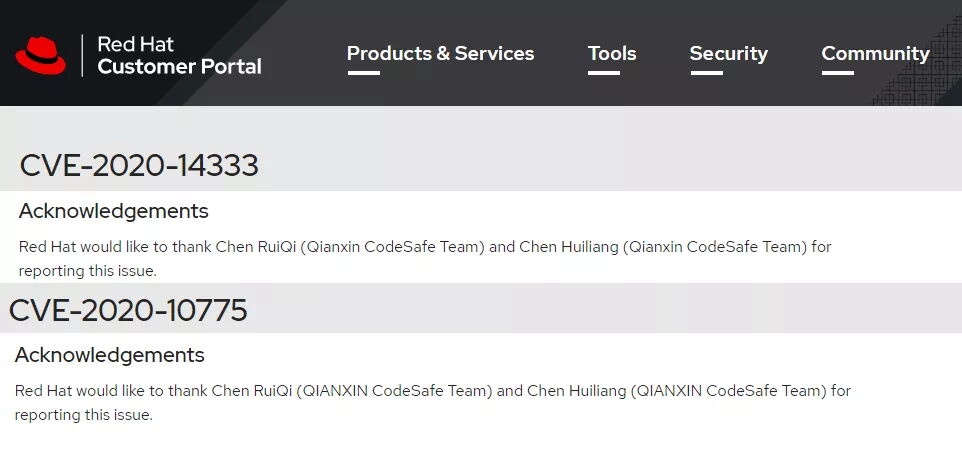
RedHat oVirt URL 重定向漏洞 |
2020-09-25 |
奇安信代碼安全實驗室 |
CVE-2020-10775 |
https://access.redhat.com/security/cve/CVE-2020-10775
https://gerrit.ovirt.org/#/c/111277/
https://github.com/oVirt/ovirt-engine/commit/362a2a8f8eca542b48a1bba7f9c827fbc44bc955
https://bugzilla.redhat.com/show_bug.cgi?id=1858184
https://bugzilla.redhat.com/show_bug.cgi?id=1866688
|
 |
| 113 |
RedHat oVirt XSS 漏洞 |
2020-09-25 |
奇安信代碼安全實驗室 |
CVE-2020-14333 |
https://access.redhat.com/security/cve/CVE-2020-14333
https://gerrit.ovirt.org/#/c/111277/
https://github.com/oVirt/ovirt-engine/commit/362a2a8f8eca542b48a1bba7f9c827fbc44bc955
https://bugzilla.redhat.com/show_bug.cgi?id=1858184
https://bugzilla.redhat.com/show_bug.cgi?id=1866688
|
 |
| 112 |
Win32k 信息泄露漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-1250 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1250
|
 |
| 111 |
Windows 提權漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-1052 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1052
|
 |
| 110 |
Windows DHCP 服務器信息泄露漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-1031 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1031
|
 |
| 109 |
Windows 內核信息泄露漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-0928 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0928
|
 |
| 108 |
Windows DNS 拒絕服務漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-1228 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1228
|
 |
| 107 |
Windows DNS 拒絕服務漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-0836 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0836
|
 |
| 106 |
Windows Cryptographic Catalog Services 提權漏洞 |
2020-09-09 |
奇安信代碼安全實驗室 |
CVE-2020-0782 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0782
|
 |
| 105 |
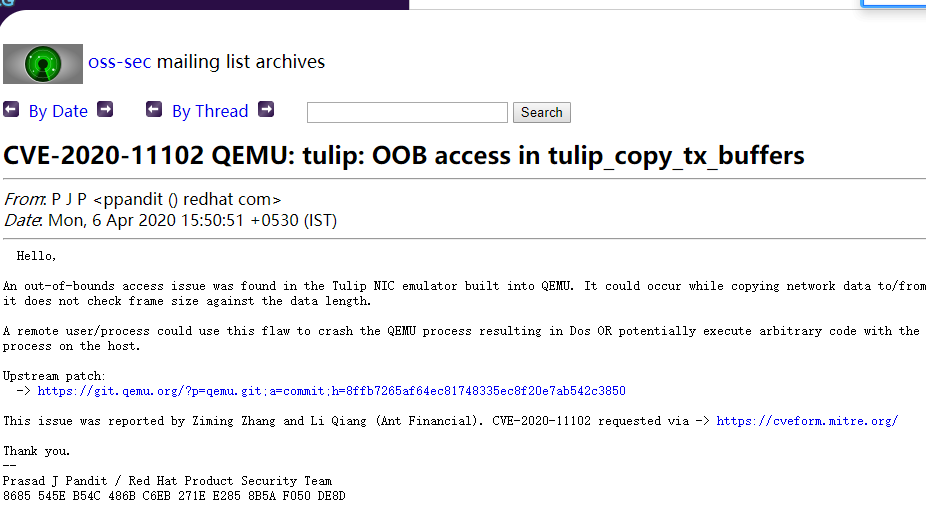
紅帽QEMU 界外訪問 |
2020-04-06 |
奇安信代碼安全實驗室 |
CVE-2020-11102 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11102
|
 |
| 104 |
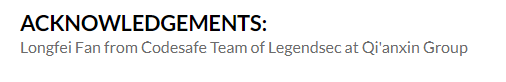
Juniper Networks Junos 15.1-19.2版本JDHCP 服務 |
2020-01-01 |
奇安信代碼安全實驗室 |
CVE-2020-1609 |
https://kb.juniper.net/InfoCenter/index?page=content&id=JSA10981
|
 |
| 103 |
Juniper Networks Junos 15.1-19.2版本JDHCP 服務 |
2020-01-01 |
奇安信代碼安全實驗室 |
CVE-2020-1605 |
https://kb.juniper.net/InfoCenter/index?page=content&id=JSA10981
|
 |
| 102 |
Juniper Networks Junos 15.1-19.2版本JDHCP 服務 |
2020-01-01 |
奇安信代碼安全實驗室 |
CVE-2020-1602 |
https://kb.juniper.net/InfoCenter/index?page=content&id=JSA10981
|
 |
| 101 |
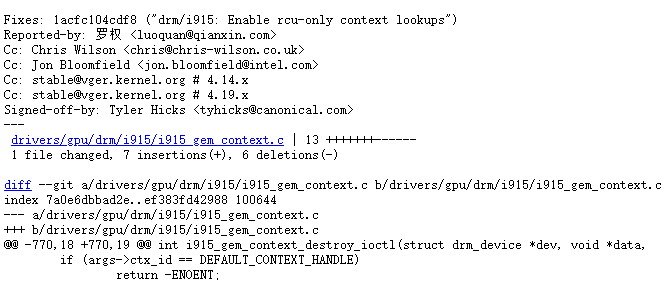
Linux 內核4.14.x 和4.19.x 穩定版內核中的釋放後使用漏洞 |
2020-01-14 |
奇安信代碼安全實驗室 |
CVE-2020-7053 |
https://lore.kernel.org/stable/20200114183937.12224-1-tyhicks@canonical.com/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-7053
|
 |
| 100 |
紅帽QEMU 仿真器 XGMAC 以太網控制器中的緩衝溢出 |
2020-08-25 |
奇安信代碼安全實驗室 |
CVE-2020-15863 |
https://access.redhat.com/security/cve/CVE-2020-15863
|
 |
| 99 |
紅帽網絡數據包處理組件中QEMU斷言失敗 |
2020-08-25 |
奇安信代碼安全實驗室 |
CVE-2020-16092 |
https://access.redhat.com/security/cve/CVE-2020-16092
|
 |
| 98 |
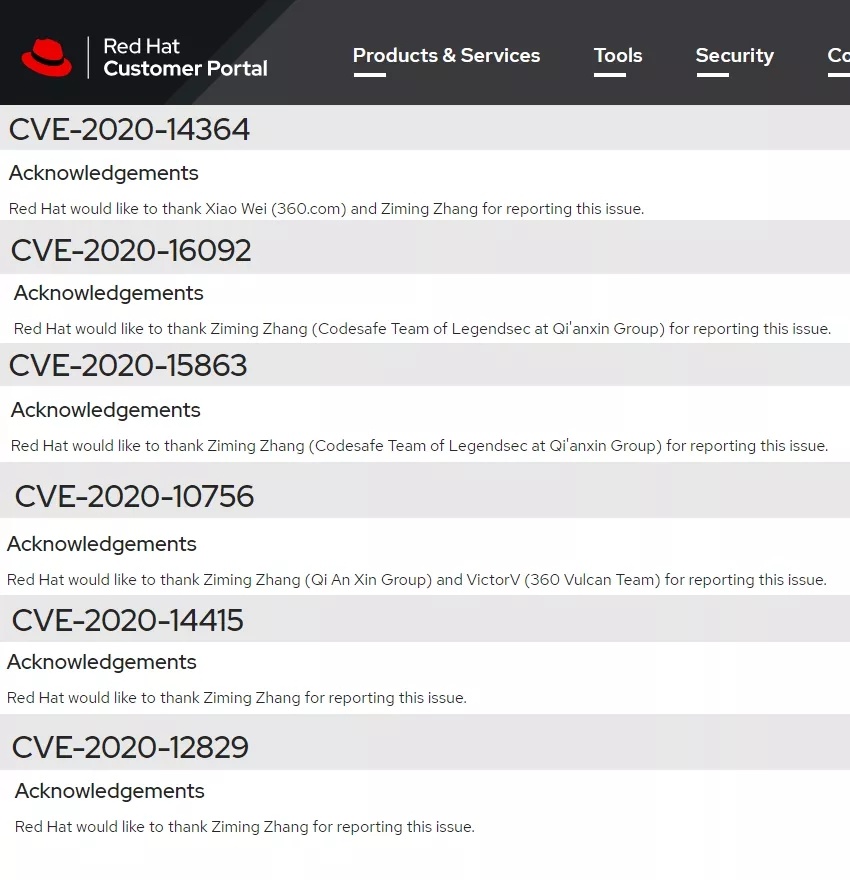
紅帽QEMU拒絕服務 |
2020-08-25 |
奇安信代碼安全實驗室 |
CVE-2020-14415 |
https://access.redhat.com/security/cve/CVE-2020-14415
|
 |
| 97 |
紅帽QEMU 仿真器的 SM501 顯示驅動實現中存在一個整數溢出漏洞 |
2020-08-25 |
奇安信代碼安全實驗室 |
CVE-2020-12829 |
https://access.redhat.com/security/cve/CVE-2020-12829
|
 |
| 96 |
紅帽QEMU 的 USB 仿真器中存在越界讀/寫訪問問題 |
2020-08-25 |
奇安信代碼安全實驗室 |
CVE-2020-14364 |
https://access.redhat.com/security/cve/CVE-2020-14364
|
 |
| 95 |
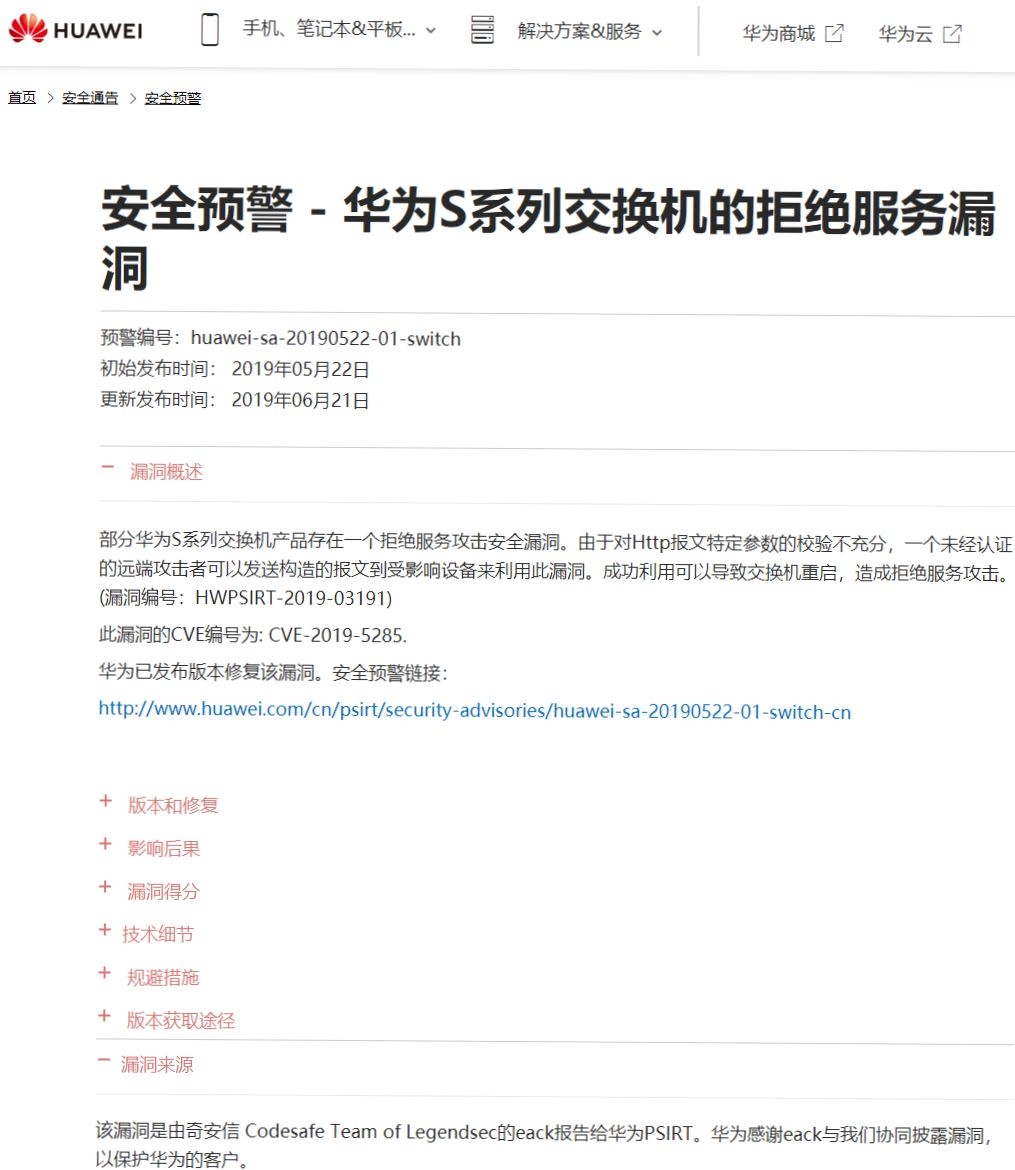
華為 Switch 系列設備漏洞 |
2019-05-22 |
奇安信代碼安全實驗室 |
CVE-2019-5285 |
https://www.huawei.com/cn/psirt/security-advisories/huawei-sa-20190522-01-switch-cn
|
 |
| 94 |
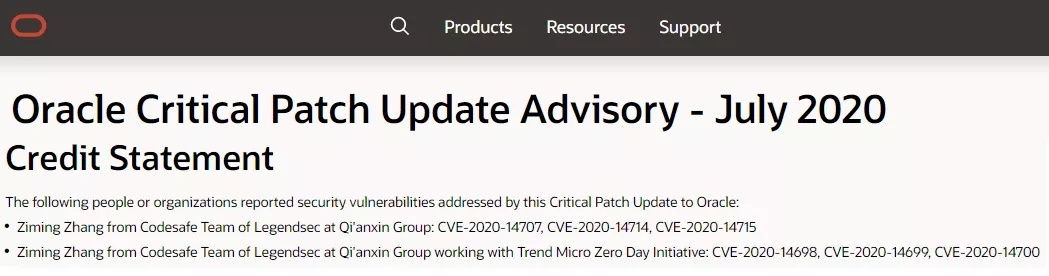
Oracle VM VirtualBox 拒絕服務漏洞 |
2020-05-22 |
奇安信代碼安全實驗室 |
CVE-2020-14715 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
| 93 |
Oracle VM VirtualBox 拒絕服務漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-14714 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
| 92 |
Oracle VM VirtualBox 拒絕服務漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-14707 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
| 91 |
Oracle VM VirtualBox 整數溢出和越界讀取漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-14700 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
| 90 |
Oracle VM VirtualBox 整數溢出和越界讀取漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-14699 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
| 89 |
Oracle VM VirtualBox 整數溢出和越界讀取漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-14698 |
https://www.oracle.com/security-alerts/cpujul2020verbose.html#OVIR
|
 |
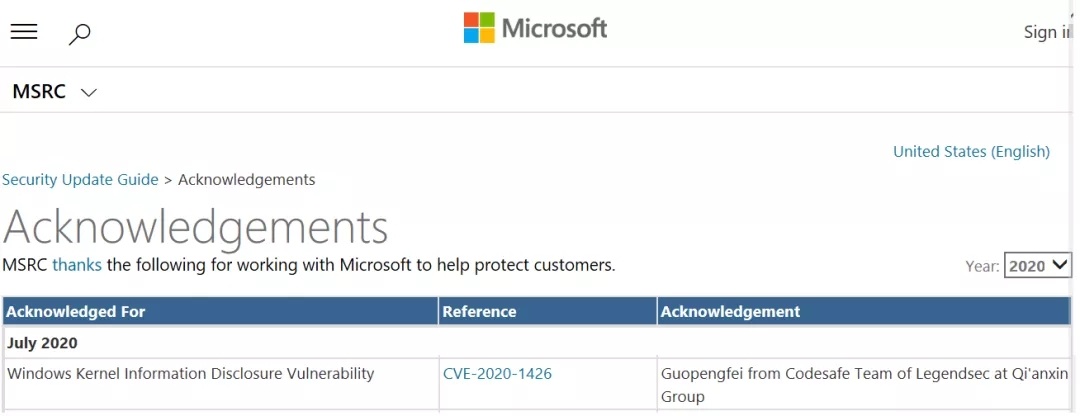
| 88 |
“重要”級別的微軟Windows 內核信息泄露漏洞 |
2020-07-15 |
奇安信代碼安全實驗室 |
CVE-2020-1426 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1426
|
 |
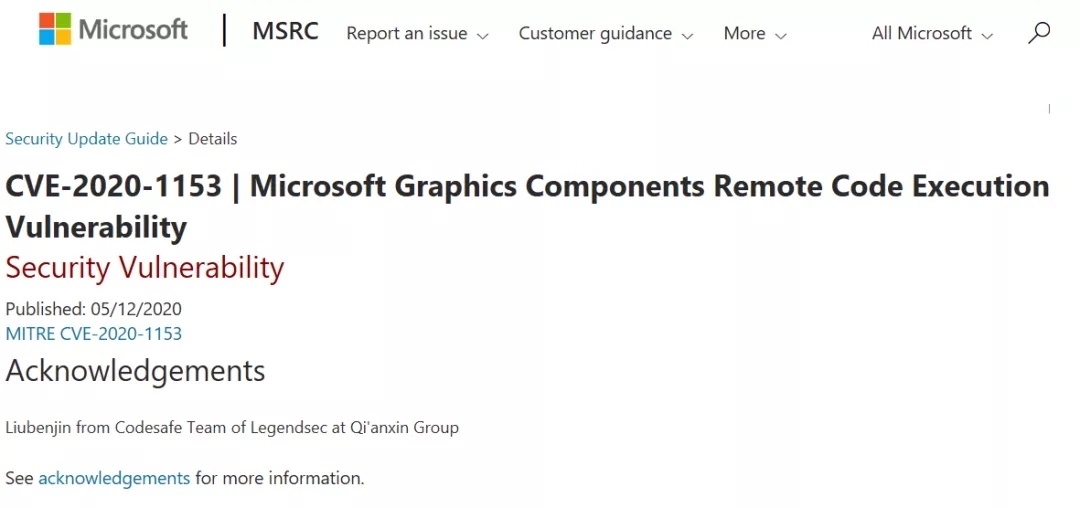
| 87 |
微軟 Graphics Components 遠程代碼執行漏洞 |
2020-05-13 |
奇安信代碼安全實驗室 |
CVE-2020-1153 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1153
|
 |
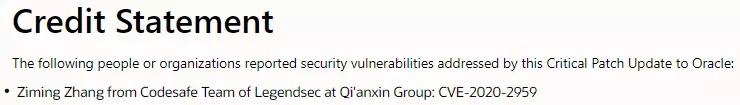
| 86 |
Oracle Virtualbox 拒絕服務漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-2959 |
https://www.oracle.com/security-alerts/cpuapr2020verbose.html#OVIR
|
 |
| 85 |
微軟Microsoft Graphics Component信息泄露漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-1005 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1005
|
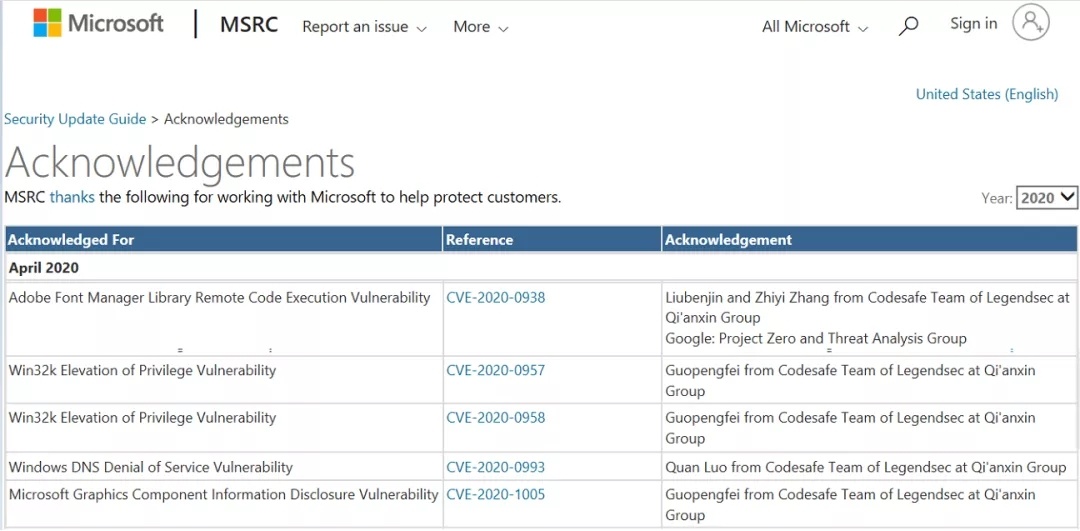 |
| 84 |
微軟Windows DNS 拒絕服務漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-0993 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0993
|
 |
| 83 |
微軟Win32k 提權漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-0958 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0958
|
 |
| 82 |
微軟Win32k 提權漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-0957 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0957
|
 |
| 81 |
微軟Adobe Font Manager Library 遠程代碼執行漏洞 |
2020-04-15 |
奇安信代碼安全實驗室 |
CVE-2020-0938 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0938
|
 |
| 80 |
微軟Win32k 提權漏洞 |
2020-03-11 |
奇安信代碼安全實驗室 |
CVE-2020-0762 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0762
|
 |
| 79 |
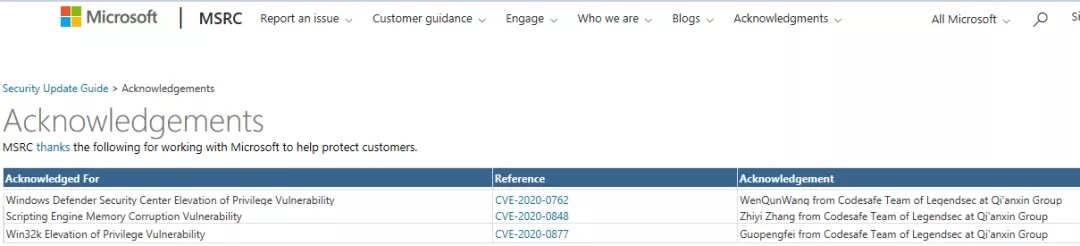
微軟WindowsDefender Security Center提權漏洞 |
2020-03-11 |
奇安信代碼安全實驗室 |
CVE-2020-0877 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0877
|
 |
| 78 |
微軟ChakraCore 腳本引擎內存損壞漏洞 |
2020-03-11 |
奇安信代碼安全實驗室 |
CVE-2020-0848 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0848
|
 |
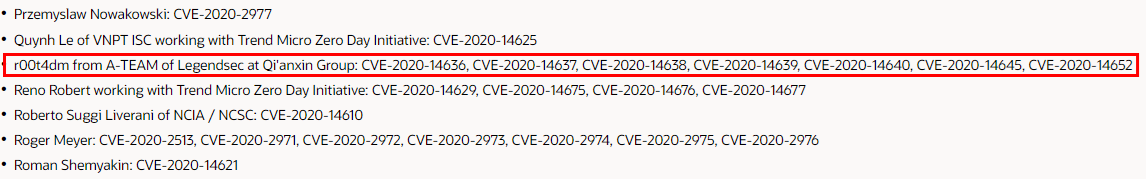
| 77 |
Oracle Fusion Middleware WebCenter Sites 安全漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14652 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 76 |
Oracle Fusion Middleware WebLogic Server Core組件安全漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14645 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 75 |
Oracle Fusion Middleware WebLogic Server 安全漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14640 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 74 |
Oracle Fusion Middleware WebLogic Server 信息泄露漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14639 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 73 |
Oracle Fusion Middleware WebLogic Server 安全漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14638 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 72 |
Oracle Fusion Middleware WebLogic Server 安全漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14637 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
| 71 |
Oracle Fusion Middleware WebLogic Server 信息泄露漏洞 |
2020-07-01 |
奇安信A-TEAM |
CVE-2020-14636 |
https://www.oracle.com/security-alerts/cpujul2020.html
|
 |
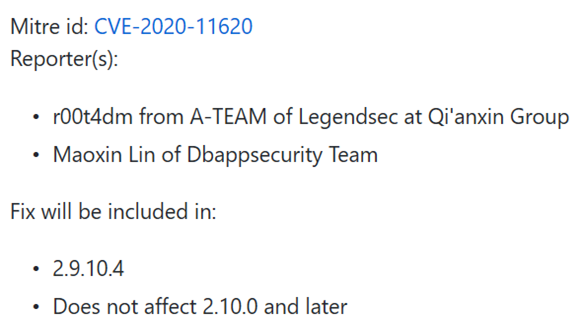
| 70 |
FasterXML jackson-databind 代碼問題漏洞 |
2020-04-01 |
奇安信 A-TEAM |
CVE-2020-11620 |
https://www.oracle.com/security-alerts/cpuapr2020.html
|
 |
| 69 |
Oracle Virtualization VM VirtualBox 安全漏洞 |
2020-04-01 |
奇安信 A-TEAM |
CVE-2020-2908 |
https://www.oracle.com/security-alerts/cpuapr2020.html
|
 |
| 68 |
Oracle Weblogic Server遠程信息泄露漏洞 |
2020-04-01 |
奇安信A-TEAM |
CVE-2020-2829 |
https://www.oracle.com/security-alerts/cpuapr2020.html
|
 |
| 67 |
Weblogic 遠程代碼執行漏洞 |
2020-04-01 |
奇安信 A-TEAM |
CVE-2020-2798 |
https://www.oracle.com/security-alerts/cpuapr2020.html
|
 |
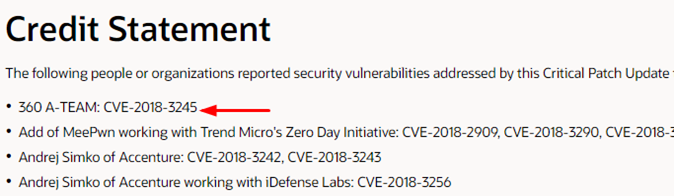
| 66 |
Weblogic遠程代碼執行漏洞 |
2018-11-07 |
奇安信 A-TEAM |
CVE-2018-3245 |
https://www.oracle.com/security-alerts/cpuoct2018.html
|
 |
| 65 |
微軟“重要”的WindowsGraphics 組件提權漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0745 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0745
|
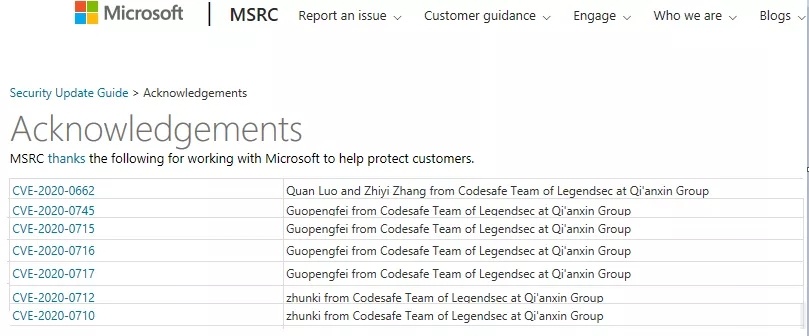 |
| 64 |
微軟“重要”的Win32k 信息泄露漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0717 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0717
|
 |
| 63 |
微軟“重要”的Win32k 信息泄露漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0716 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0716
|
 |
| 62 |
微軟“重要”的WindowsGraphics 組件提權漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0715 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0715
|
 |
| 61 |
微軟“嚴重”的腳本引擎內存損壞漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0712 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0712
|
 |
| 60 |
微軟“嚴重”的腳本引擎內存損壞漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0710 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0710
|
 |
| 59 |
微軟“嚴重”的遠程任意代碼可執行漏洞 |
2020-02-12 |
奇安信代碼安全實驗室 |
CVE-2020-0662 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0662
|
 |
| 58 |
微軟提權漏洞 |
|
奇安信代碼安全實驗室 |
CVE-2019-1434 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1434
|
 |
| 57 |
微軟提權漏洞 |
|
奇安信代碼安全實驗室 |
CVE-2019-1435 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1435
|
 |
| 56 |
微軟提權漏洞 |
|
奇安信代碼安全實驗室 |
CVE-2019-1433 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1433
|
 |
| 55 |
微軟提權漏洞 |
|
奇安信代碼安全實驗室 |
CVE-2019-1407 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1407
|
 |
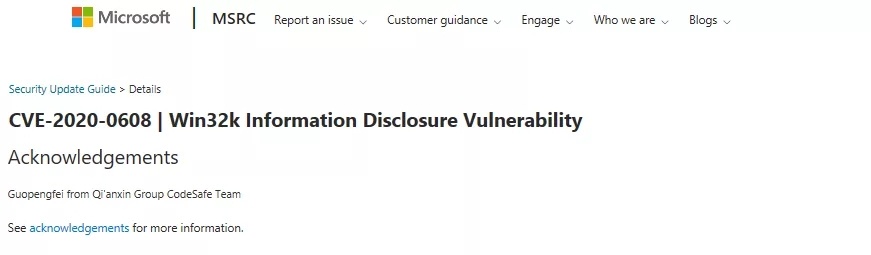
| 54 |
微軟Win32k 信息泄露漏洞 |
2020-01-15 |
奇安信代碼安全實驗室 |
CVE-2020-0608 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-0608
|
 |
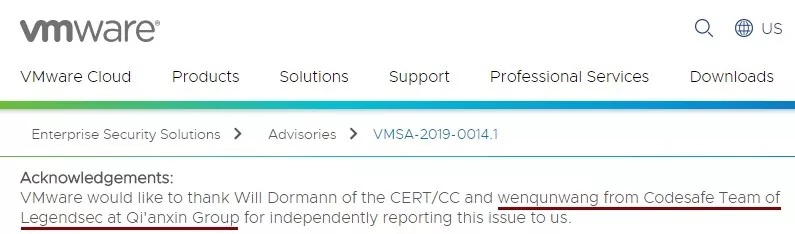
| 53 |
VMware 聲卡設備的uaf漏洞 |
2019-09-19 |
奇安信代碼安全實驗室 |
CVE-2019-5527 |
https://www.vmware.com/security/advisories/VMSA-2019-0014.html
|
 |
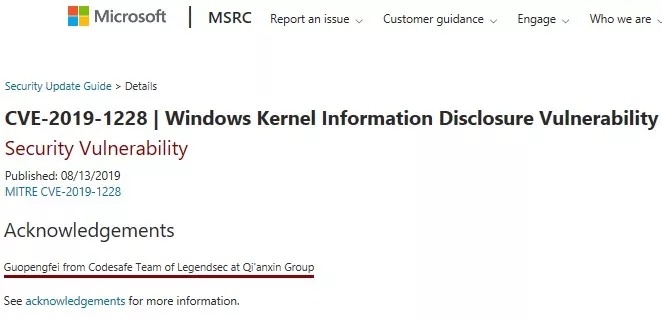
| 52 |
微軟Windows 內核信息泄漏漏洞 |
2019-08-13 |
奇安信代碼安全實驗室 |
CVE-2020-1228 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1228
|
 |
| 51 |
Buffer error |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9704 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
| 50 |
Stack exhaustion |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9703 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
| 49 |
Stack exhaustion |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9702 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
| 48 |
Buffer error |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9701 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
| 47 |
Buffer error |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9700 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
| 46 |
Buffer error |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9699 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
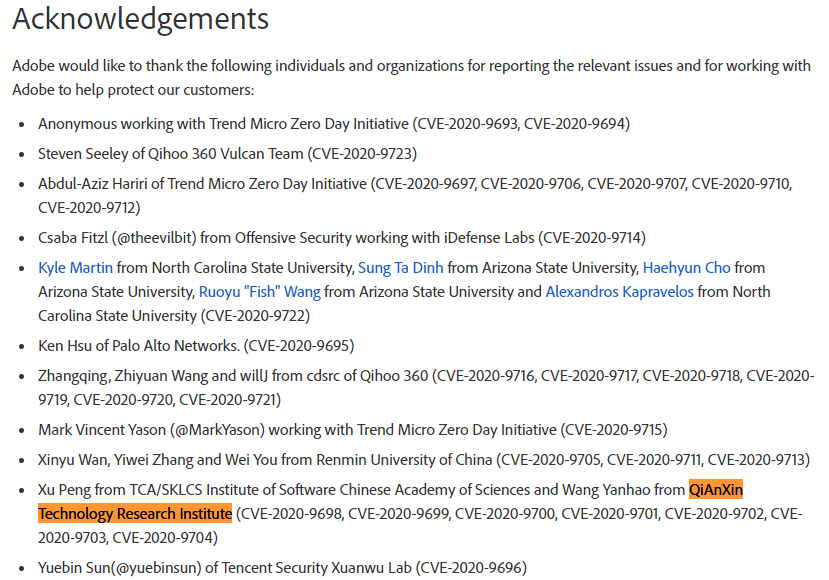
| 45 |
Buffer error |
2020-08-11 |
奇安信技術研究院 |
CVE-2020-9698 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-48.html
|
 |
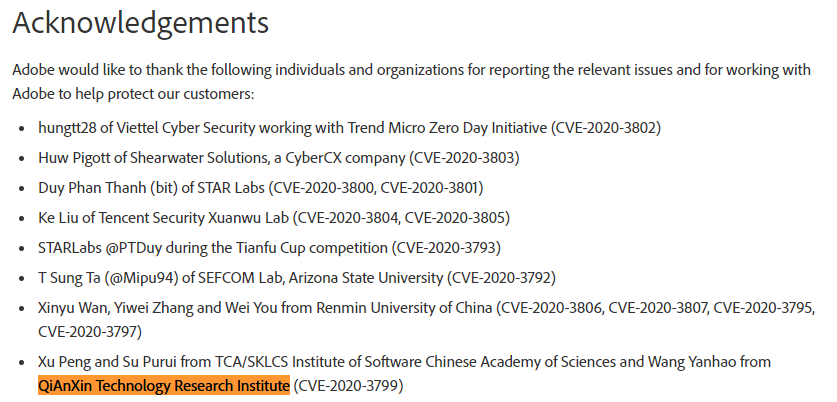
| 44 |
Stack-based buffer overflow |
2020-03-17 |
奇安信技術研究院 |
CVE-2020-3799 |
https://helpx.adobe.com/si/security/products/acrobat/apsb20-13.html
|
 |
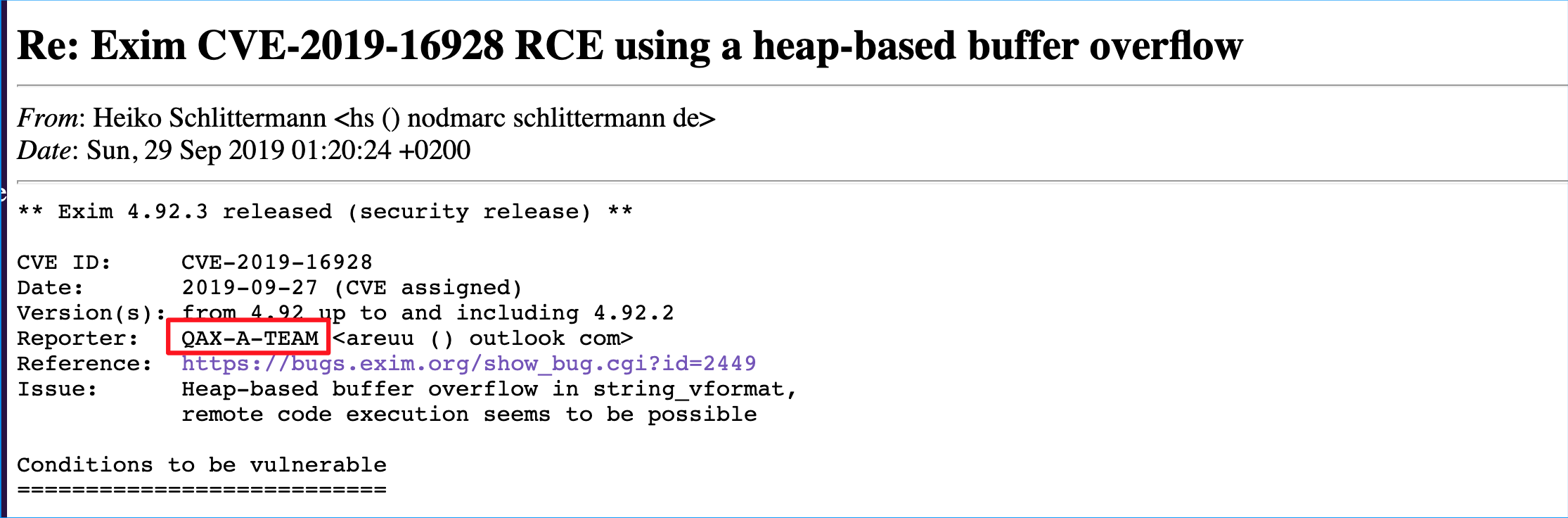
| 43 |
Exim 遠程堆溢出漏洞 |
|
|
CVE-2019-16928 |
https://seclists.org/oss-sec/2019/q3/256
|
 |
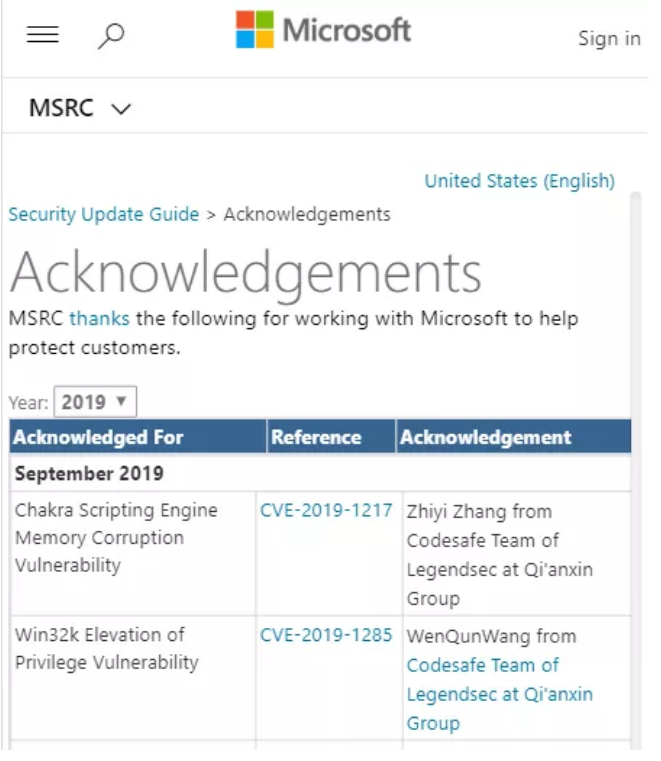
| 42 |
Windows內核高危漏洞 |
|
|
CVE-2019-1285 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1285
|
 |
| 41 |
Edge瀏覽器高危漏洞 |
|
|
CVE-2019-1217 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1217
|
 |
| 40 |
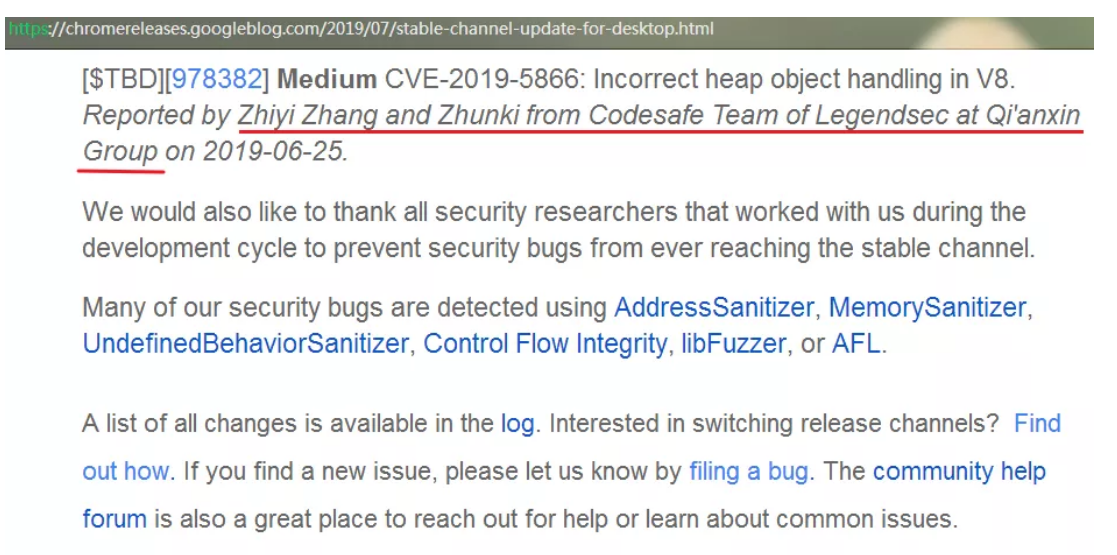
Chrome瀏覽器中的UAF漏洞 |
|
|
CVE-2019-5866 |
https://chromereleases.googleblog.com/2019/07/stable-channel--for-desktop.html
|
 |
| 39 |
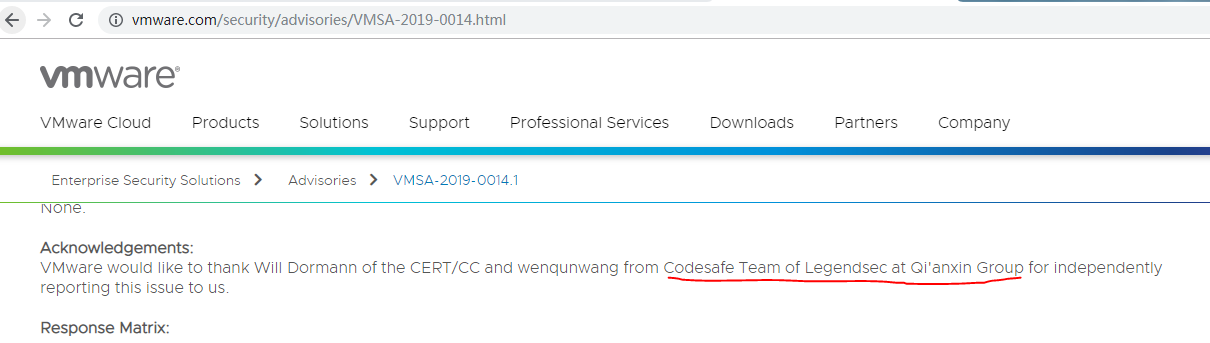
Vmware 溢出漏洞 |
|
|
CVE-2019-5527 |
https://www.vmware.com/security/advisories/VMSA-2019-0014.html
|
 |
| 38 |
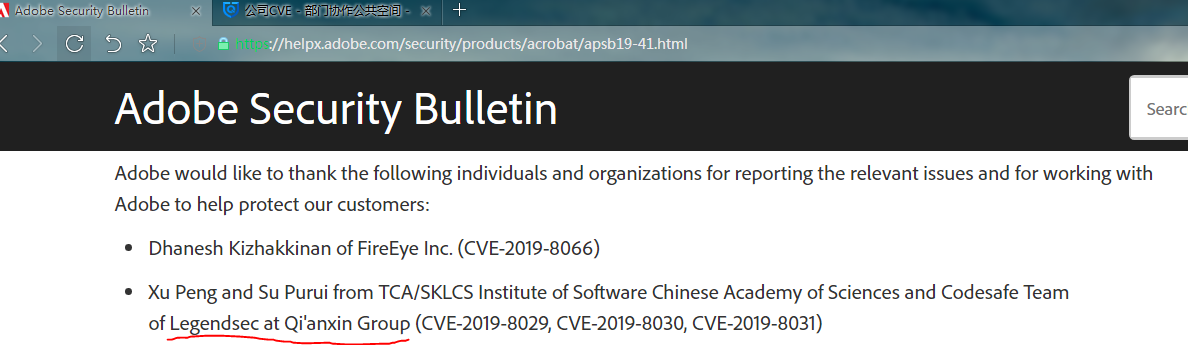
Acrobat Reader DC中的uaf漏洞 |
|
|
CVE-2019-8031 |
https://helpx.adobe.com/security/products/acrobat/apsb19-41.html
|
 |
| 37 |
Acrobat Reader DC中的uaf漏洞 |
|
|
CVE-2019-8030 |
https://helpx.adobe.com/security/products/acrobat/apsb19-41.html
|
 |
| 36 |
Acrobat Reader DC中的uaf漏洞 |
|
|
CVE-2019-8029 |
https://helpx.adobe.com/security/products/acrobat/apsb19-41.html
|
 |
| 35 |
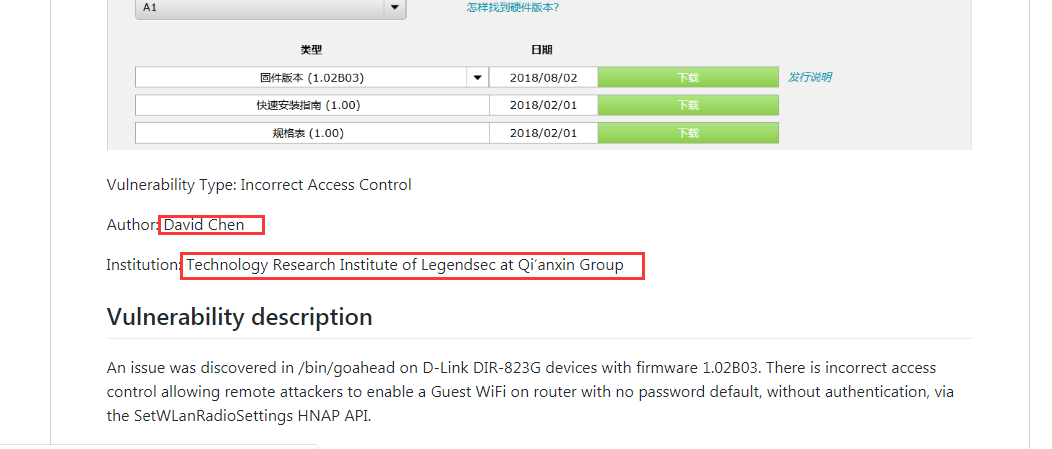
越權啓用WiFi DIR-823G SetWLanRadioSettings Guest-WiFi Enable |
|
|
CVE-2019-8392 |
https://github.com/leonW7/D-Link/blob/master/Vul_6.md
|
 |
| 34 |
局域網DNS劫持 DIR-823G SetWanSettings DNS Hijack |
|
|
CVE-2019-7390 |
http://www.securityfocus.com/bid/106855
https://github.com/leonW7/D-Link/blob/master/Vul_5.md
|
 |
| 33 |
遠程拒絕服務 DIR-823G SetFactoryDefault DoS |
|
|
CVE-2019-7389 |
http://www.securityfocus.com/bid/106853
https://github.com/leonW7/D-Link/blob/master/Vul_4.md
|
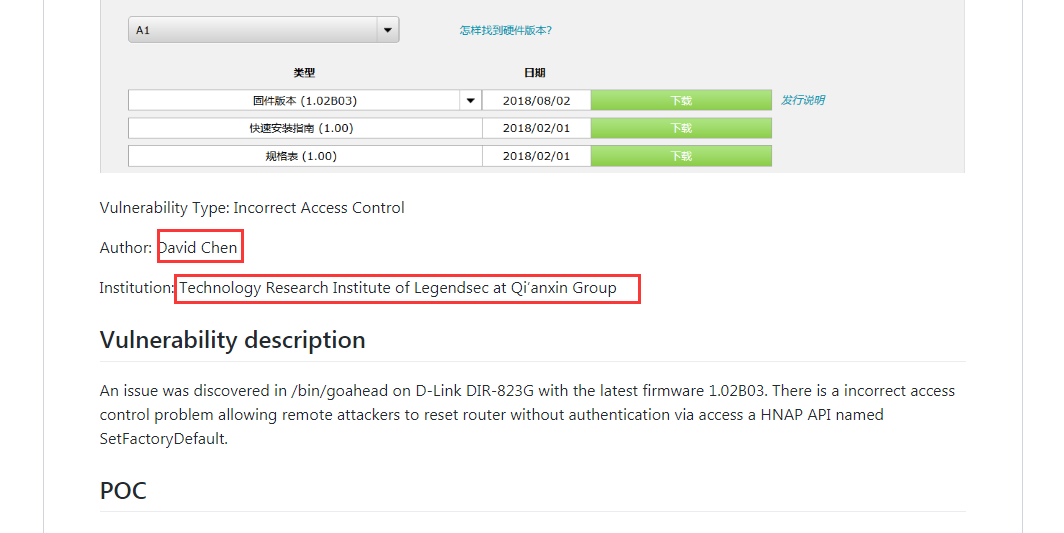 |
| 32 |
遠程信息泄露 DIR-823G GetClientInfo InfoLeak |
|
|
CVE-2019-7388 |
http://www.securityfocus.com/bid/106852
https://github.com/leonW7/D-Link/blob/master/Vul_3.md
|
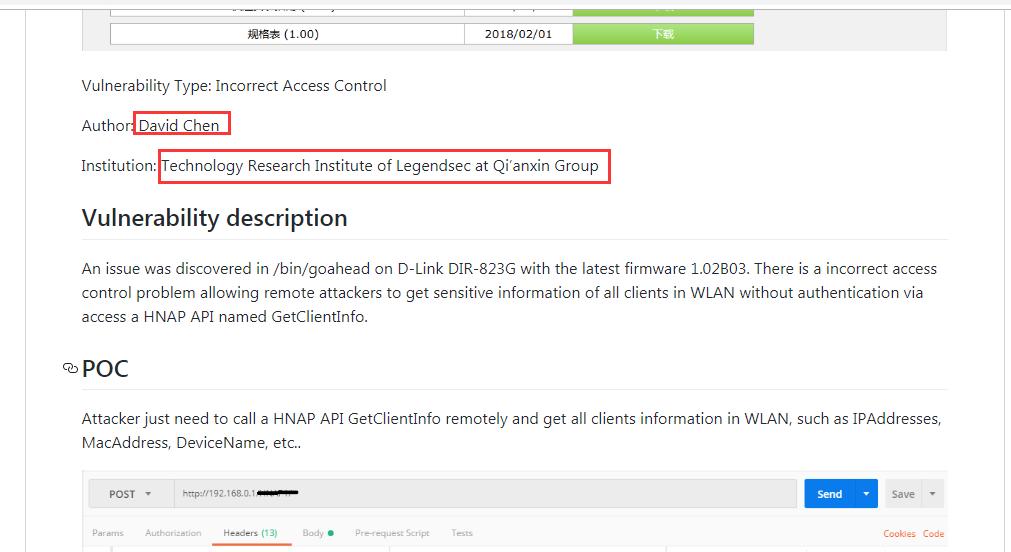 |
| 31 |
遠程命令注入 DIR-823G HNAP_Entry_Func CMD Injection |
|
|
CVE-2019-7298 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7298
http://www.securityfocus.com/bid/106814
|
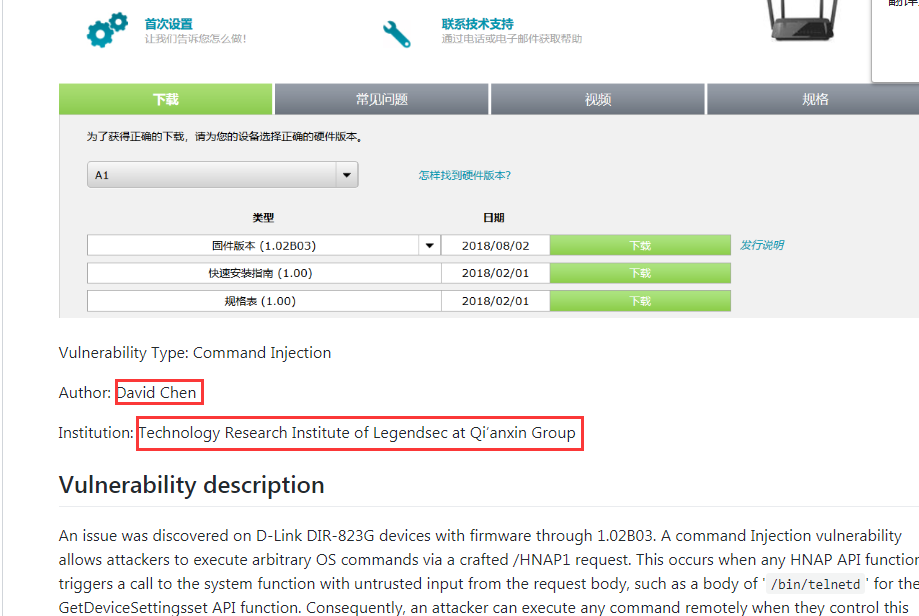 |
| 30 |
遠程命令注入 DIR-823G GetNetwork TomographyResult CMD Injection |
|
|
CVE-2019-7297 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7297
http://www.securityfocus.com/bid/106815
|
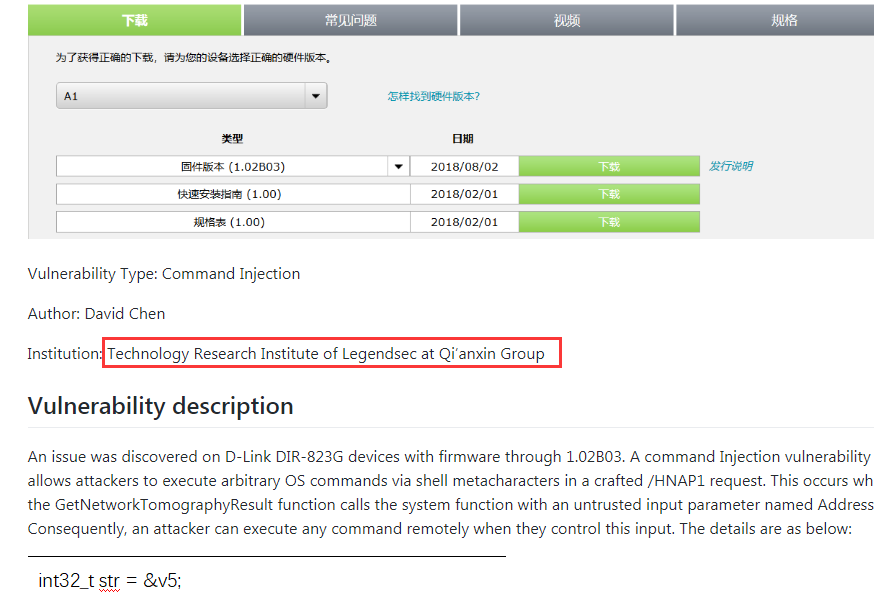 |
| 29 |
Win32k Elevation of Privilege Vulnerability |
|
|
CVE-2019-0960 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0960
|
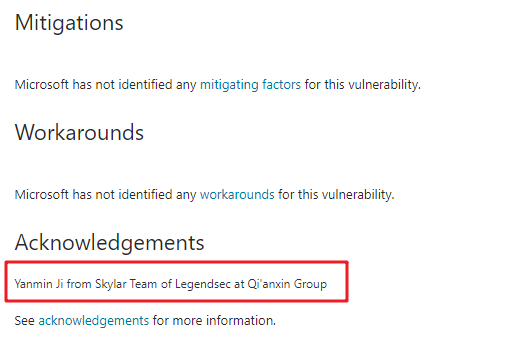 |
| 28 |
Windows NTLM Tampering Vulnerability |
|
|
CVE-2019-1040 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1040
|
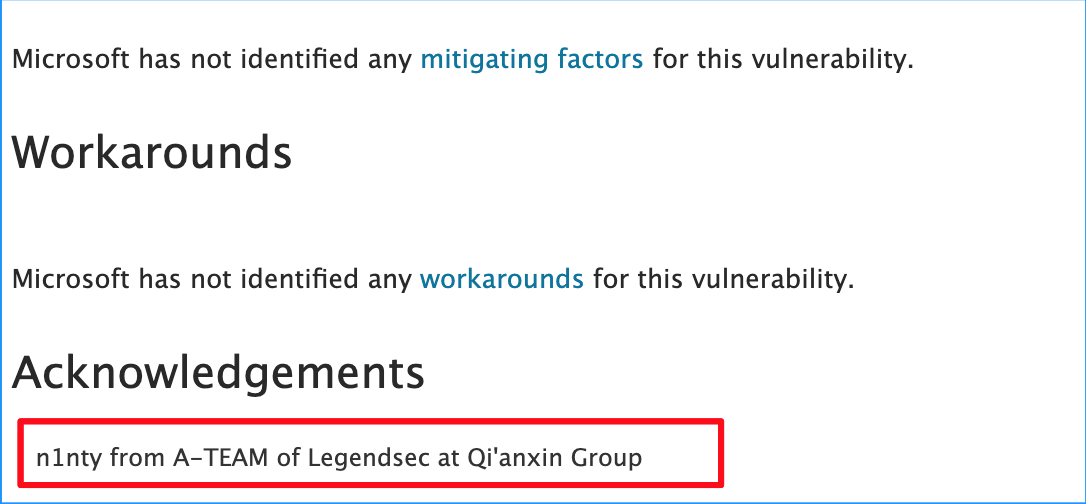 |
| 27 |
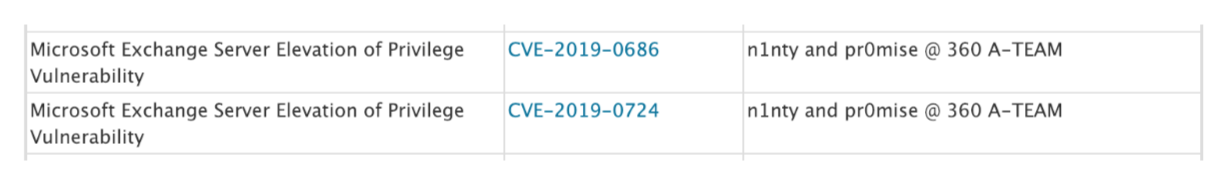
Microsoft Exchange Server Elevation of Privilege Vulnerability |
|
|
CVE-2019-0724 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0724
|
 |
| 26 |
Microsoft Exchange Server Elevation of Privilege Vulnerability |
|
|
CVE-2019-0686 |
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0686
|
 |
| 25 |
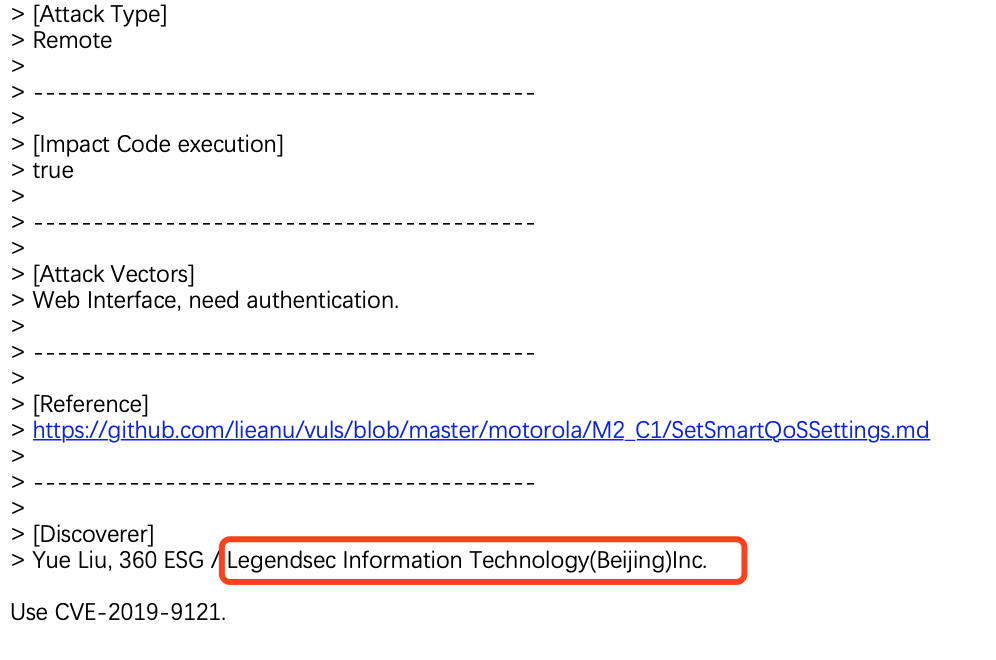
Motorola SetSmartQoSSettings CMD Injection |
|
|
CVE-2019-9121 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9121
https://github.com/lieanu/vuls/blob/master/motorola/M2_C1/SetSmartQoSSettings.md
|
 |
| 24 |
Motorola SetWLanACLSettings CMD Injection |
|
|
CVE-2019-9120 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9120
https://github.com/lieanu/vuls/blob/master/motorola/M2_C1/SetWLanACLSettings.md
|
 |
| 23 |
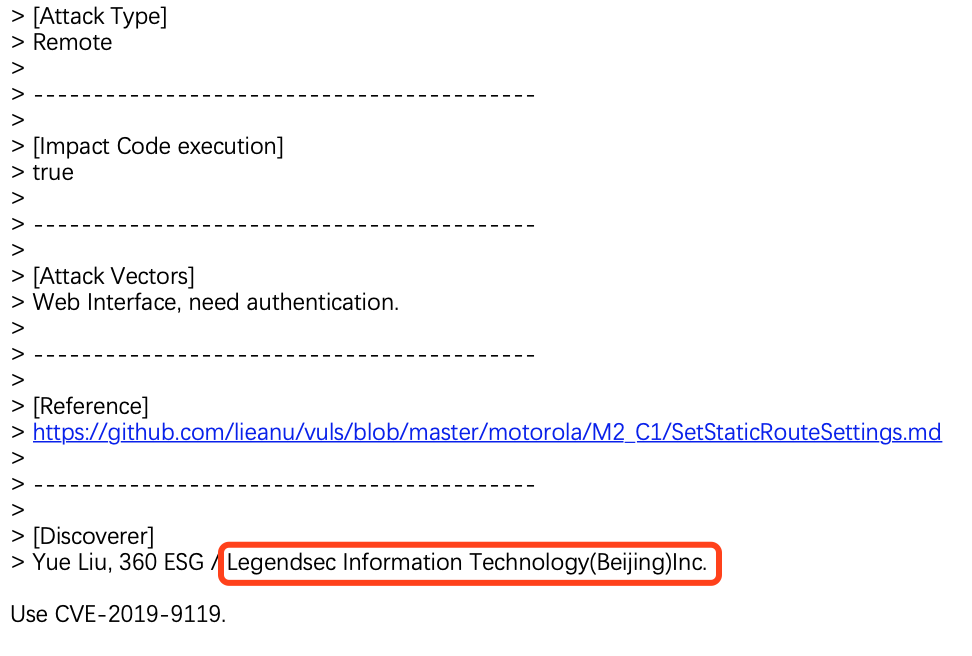
Motorola SetStaticRouteSettings CMD Injection |
|
|
CVE-2019-9119 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9119
https://github.com/lieanu/vuls/blob/master/motorola/M2_C1/SetStaticRouteSettings.md
|
 |
| 22 |
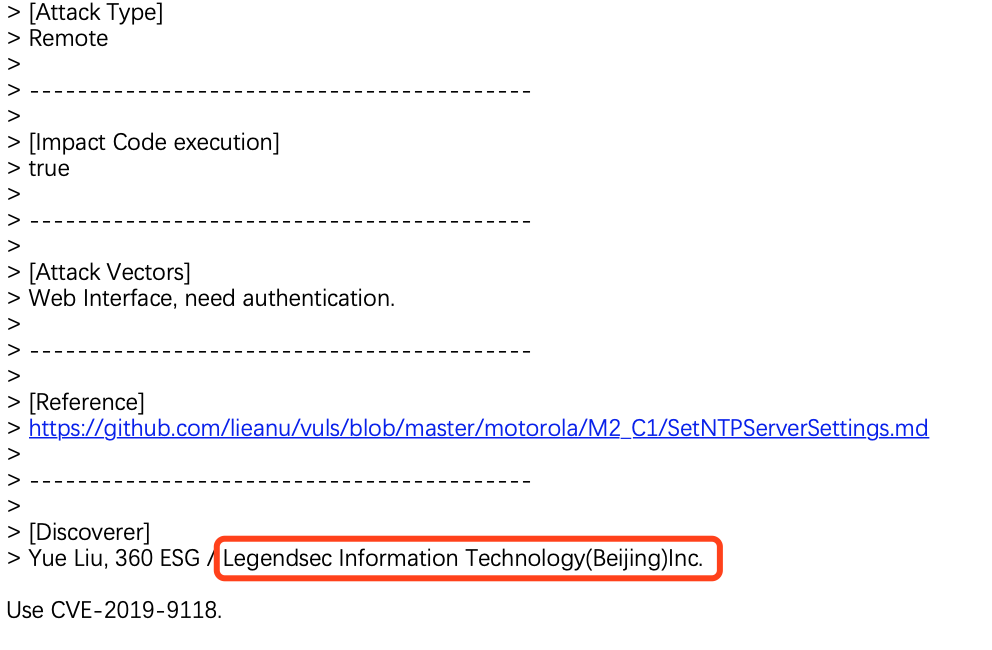
Motorola SetStaticRouteSettings CMD Injection |
|
|
CVE-2019-9118 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9118
https://github.com/lieanu/vuls/blob/master/motorola/M2_C1/SetNTPServerSettings.md
|
 |
| 21 |
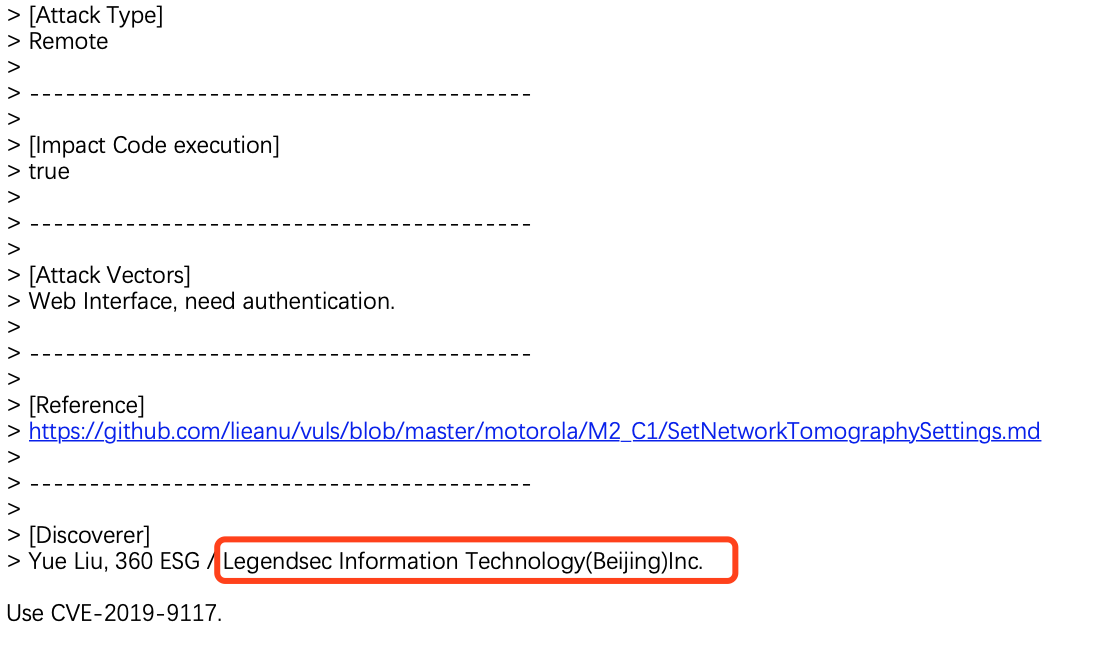
Motorola SetStaticRouteSettings CMD Injection |
|
|
CVE-2019-9117 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9117
https://github.com/lieanu/vuls/blob/master/motorola/M2_C1/SetNetworkTomographySettings.md
|
 |
| 20 |
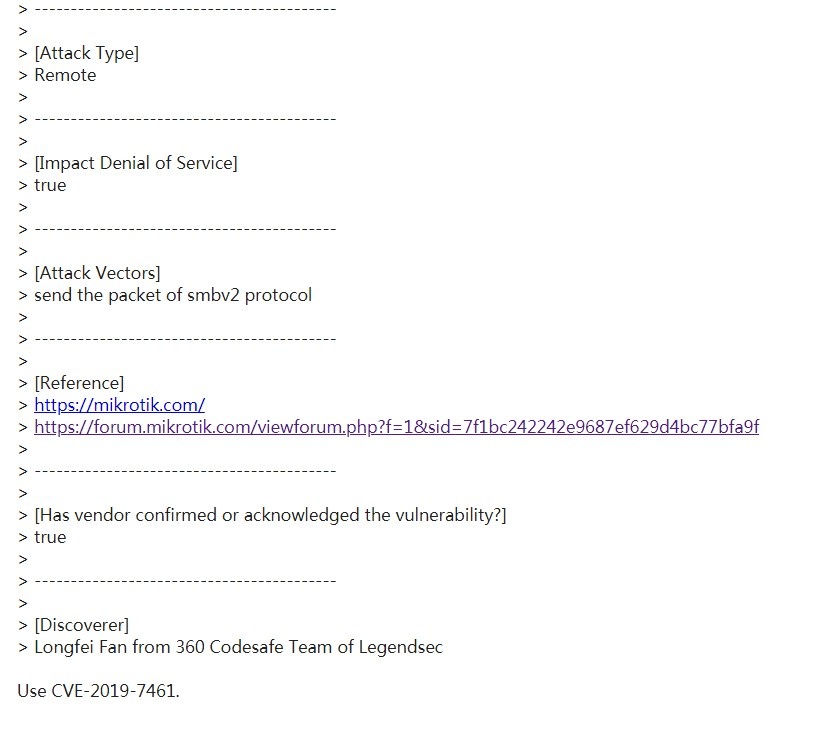
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7461 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7461
|
 |
| 19 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7460 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7460
|
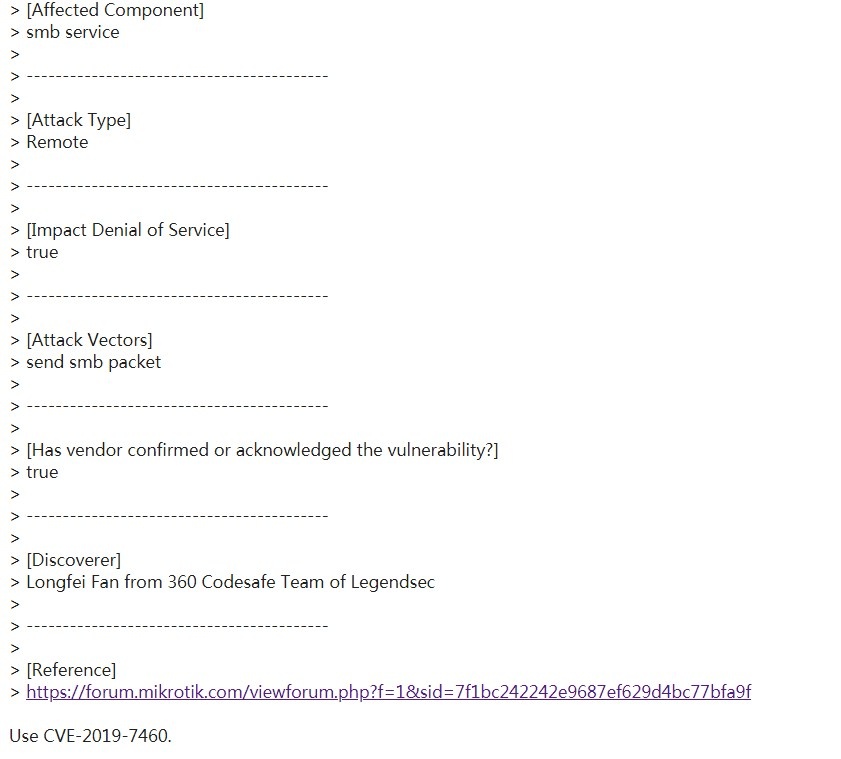 |
| 18 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7459 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7459
|
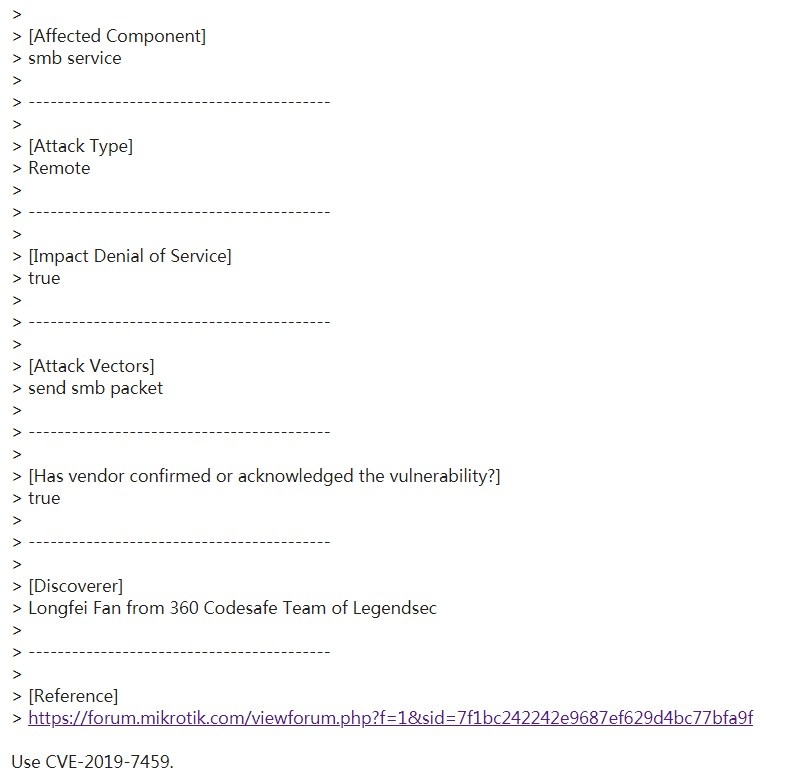 |
| 17 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7458 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7458
|
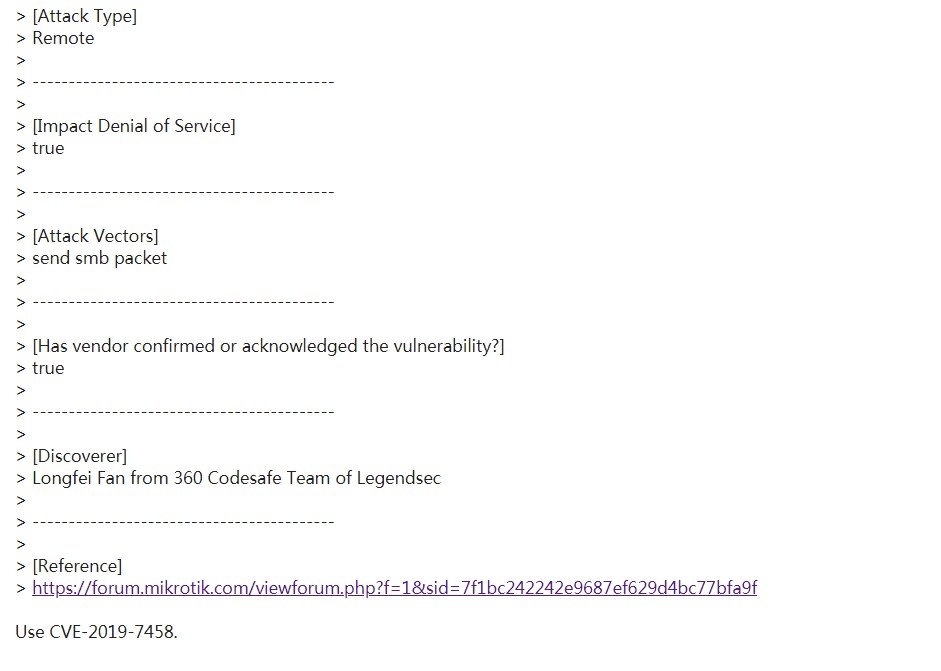 |
| 16 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7457 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7457
|
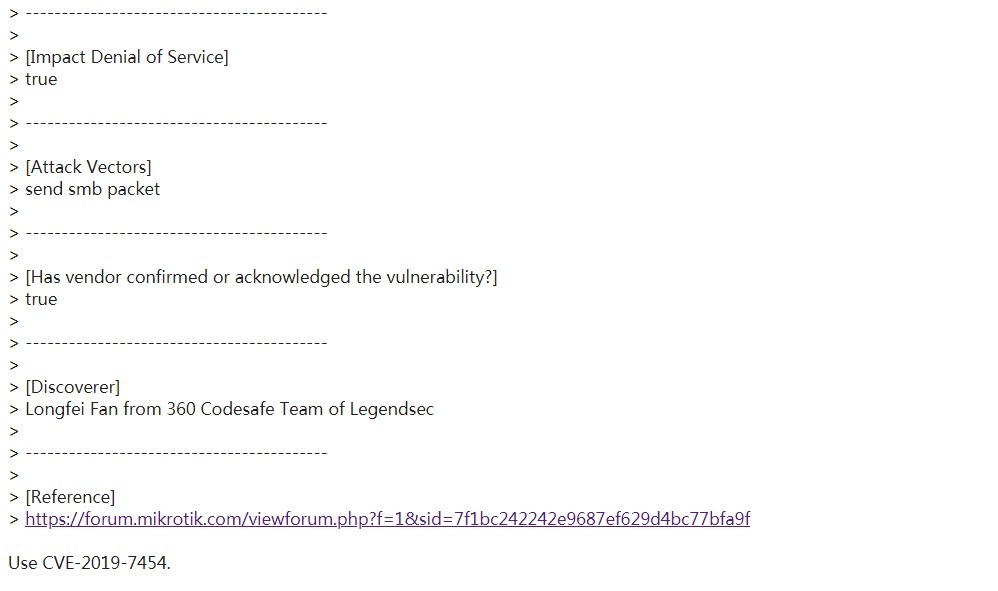 |
| 15 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7456 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7456
|
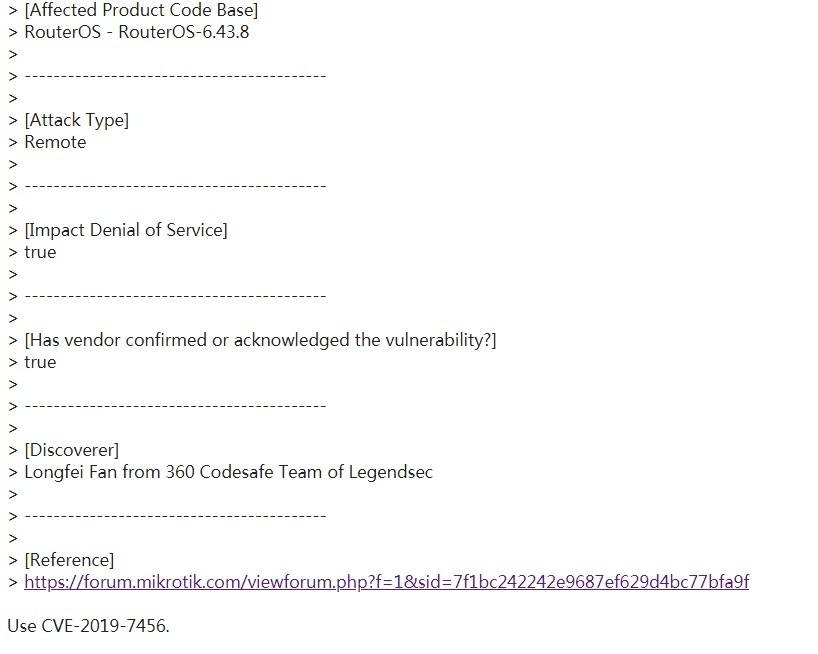 |
| 14 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7455 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7455
|
 |
| 13 |
內存溢出 Mikrotik RouteOS smb remote DOS |
|
|
CVE-2019-7454 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7454
|
 |
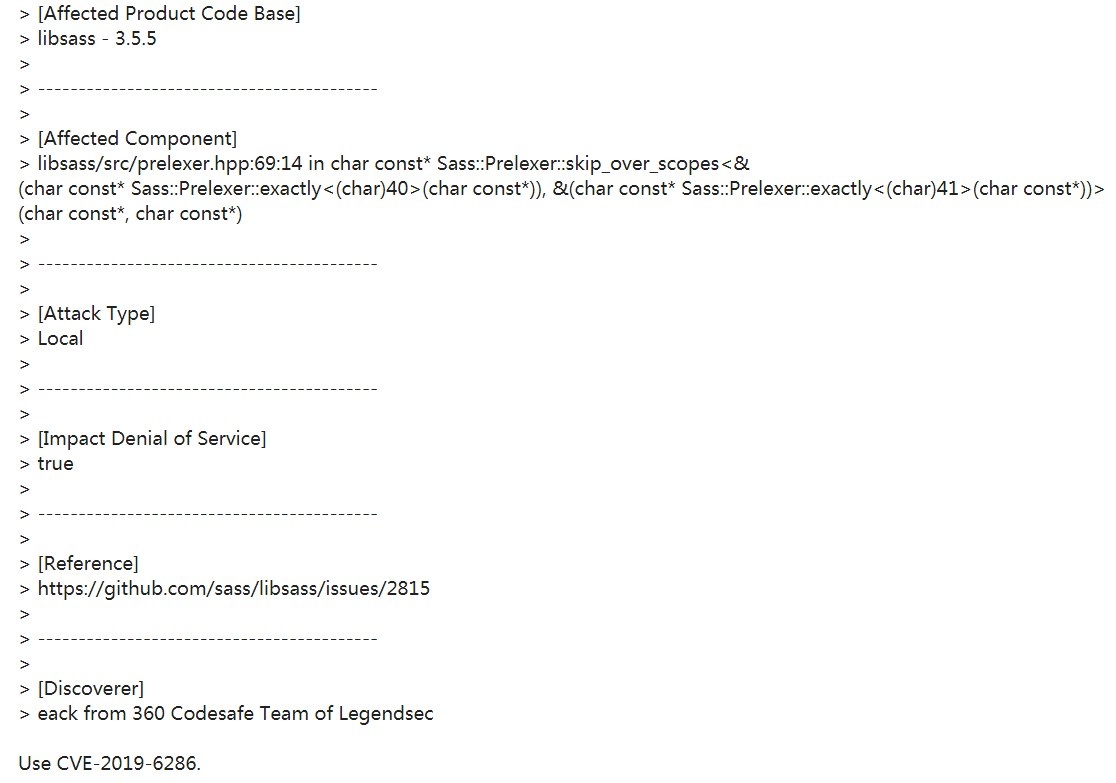
| 12 |
libsass內存溢出漏洞 |
|
|
CVE-2019-6286 |
https://github.com/sass/libsass/issues/2815
|
 |
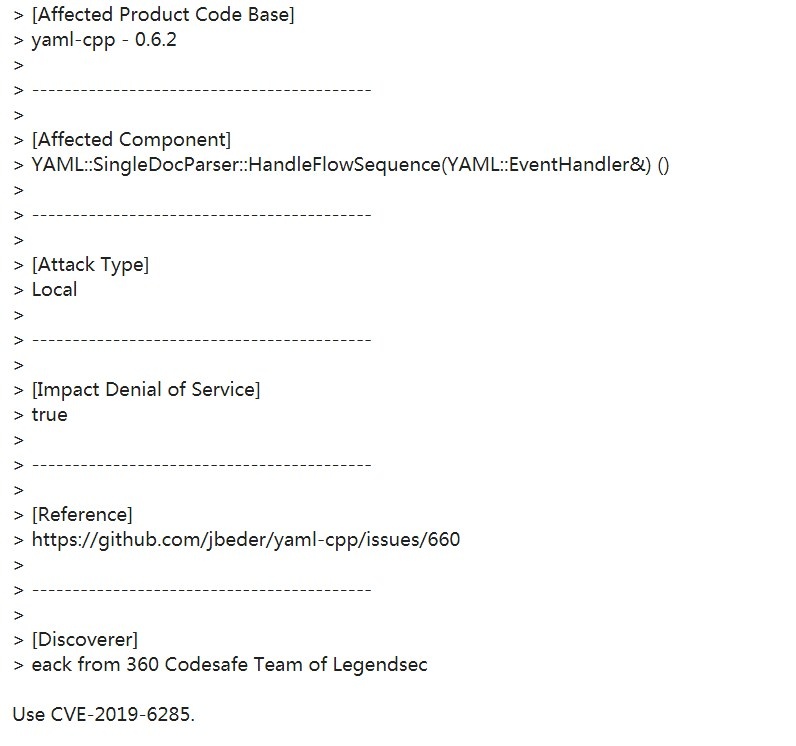
| 11 |
yaml-cpp內存溢出漏洞 |
|
|
CVE-2019-6285 |
https://github.com/jbeder/yaml-cpp/issues/660
|
 |
| 10 |
libsass內存溢出漏洞 |
|
|
CVE-2019-6284 |
https://github.com/sass/libsass/issues/2816
|
 |
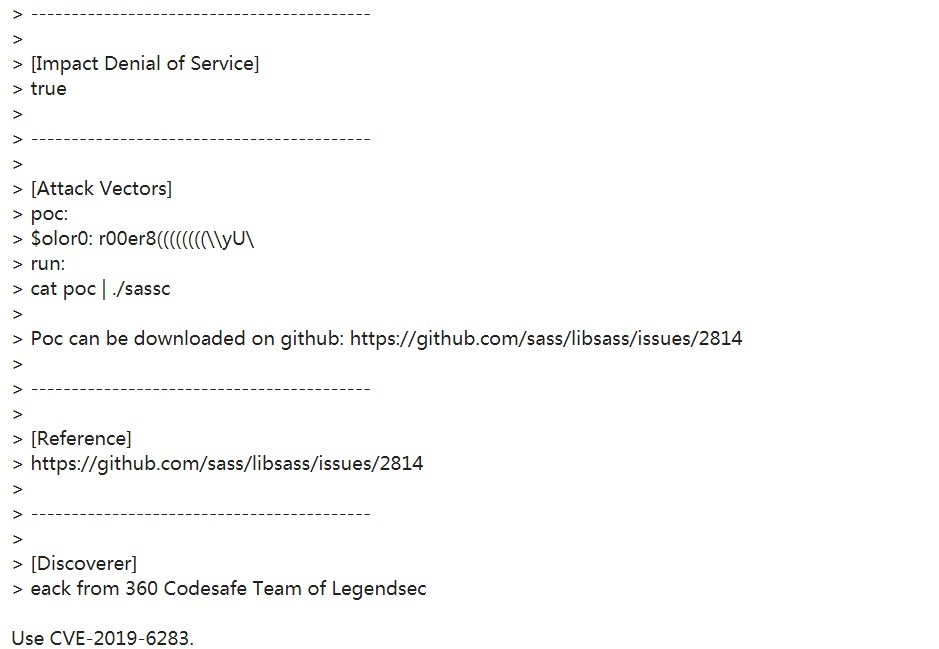
| 9 |
libsass內存溢出漏洞 |
|
|
CVE-2019-6283 |
https://github.com/sass/libsass/issues/2814
|
 |
| 8 |
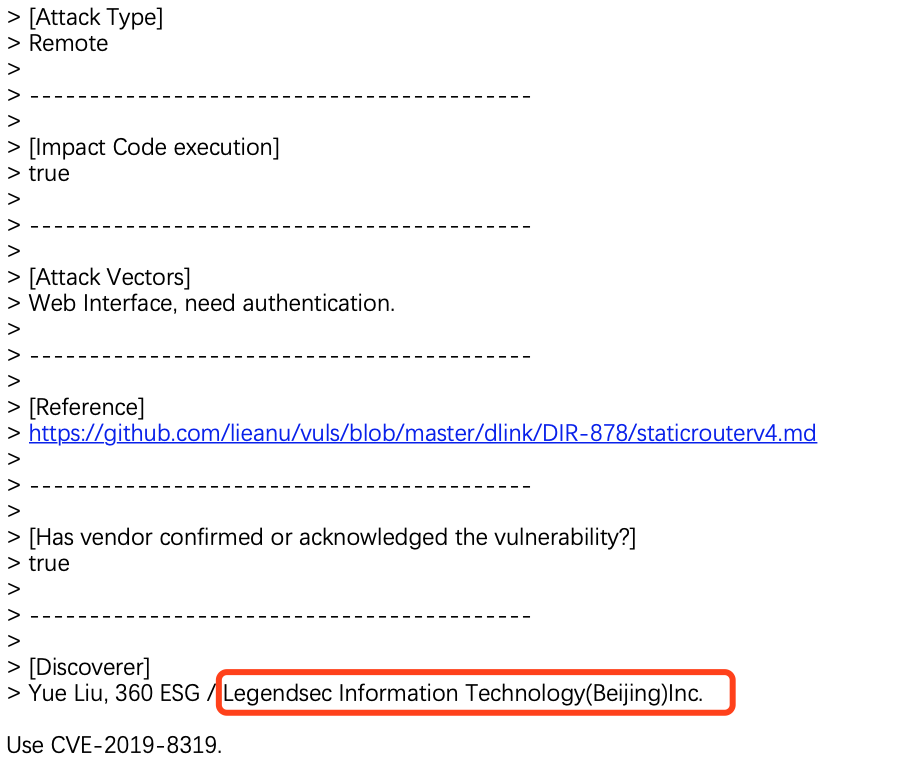
D-Link SetStaticRoute CMD Injection |
|
|
CVE-2019-8319 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8319
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/staticrouterv4.md
|
 |
| 7 |
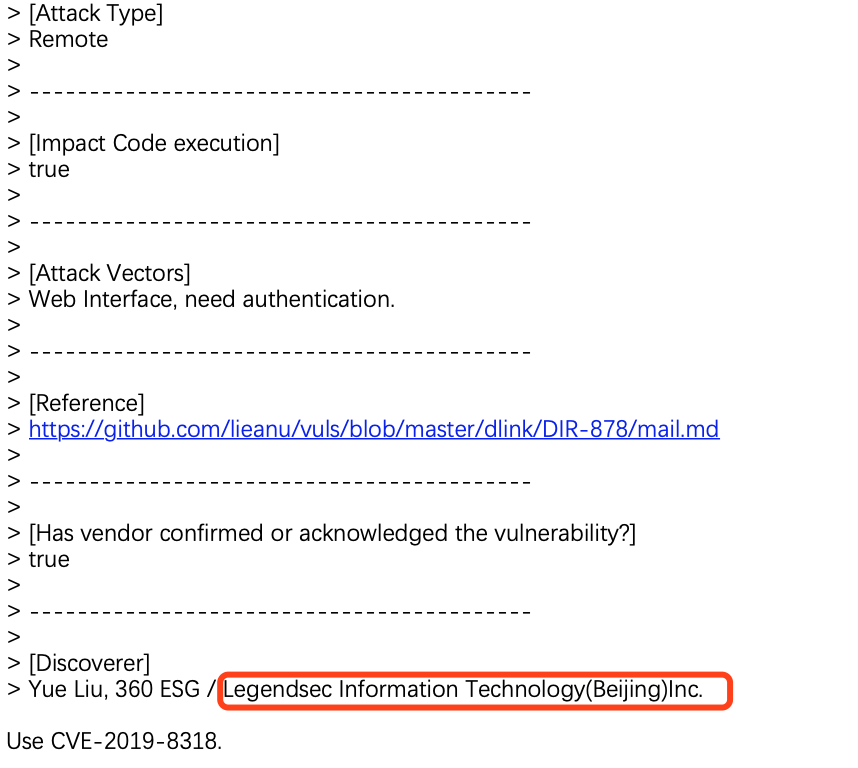
D-Link SetSysEmailSettings CMD Injection |
|
|
CVE-2019-8318 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8318
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/mail.md
|
 |
| 6 |
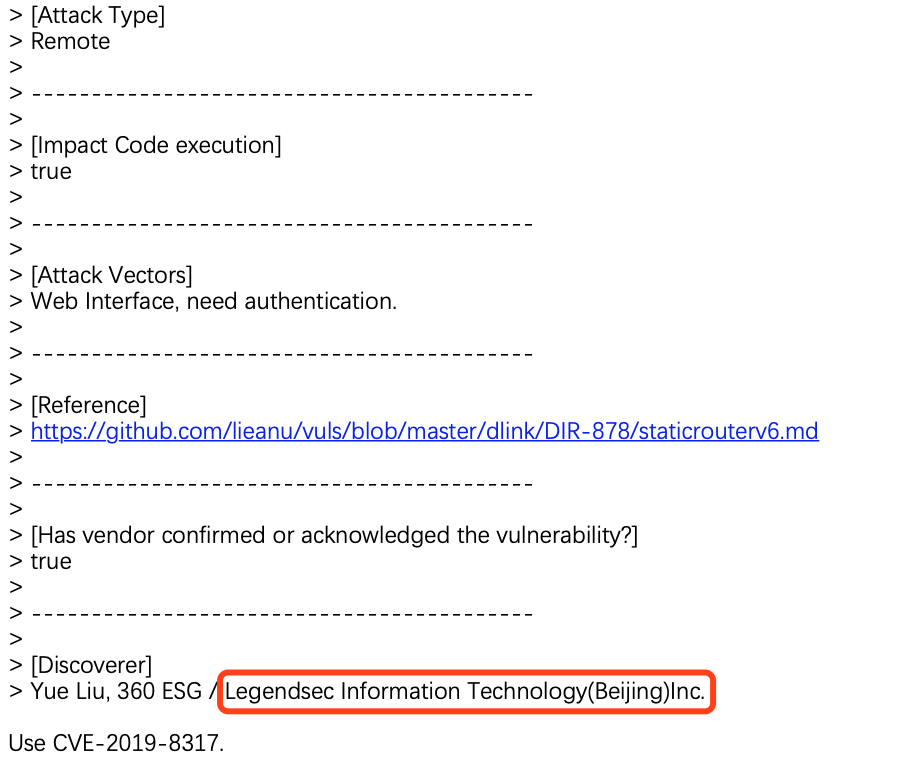
D-Link SetStaticRoute CMD Injection |
|
|
CVE-2019-8317 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8317
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/staticrouterv6.md
|
 |
| 5 |
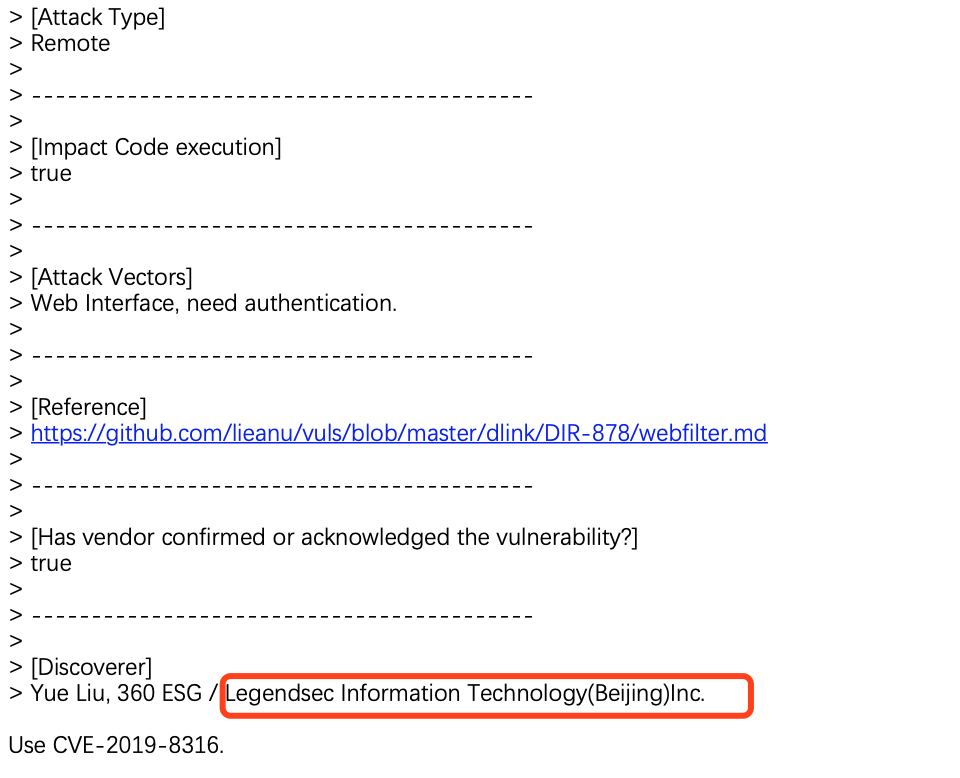
D-Link SetWebFilterSettings CMD Injection |
|
|
CVE-2019-8316 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8316
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/webfilter.md
|
 |
| 4 |
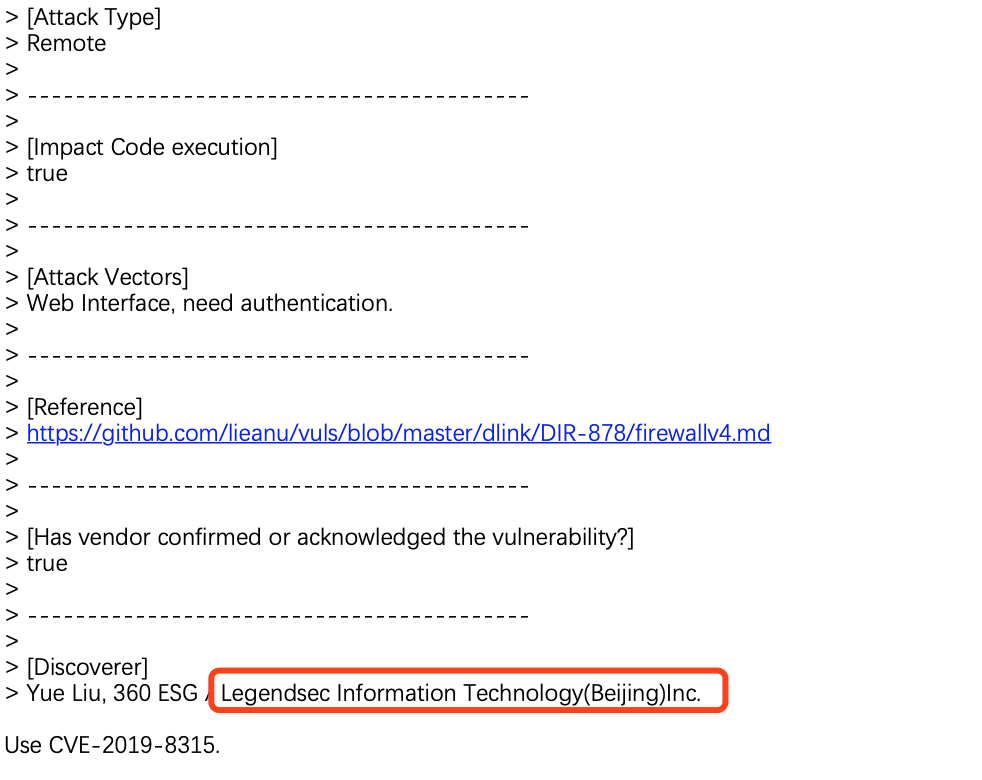
D-Link SetStaticRoute CMD Injection |
|
|
CVE-2019-8315 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8315
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/firewallv4.md
|
 |
| 3 |
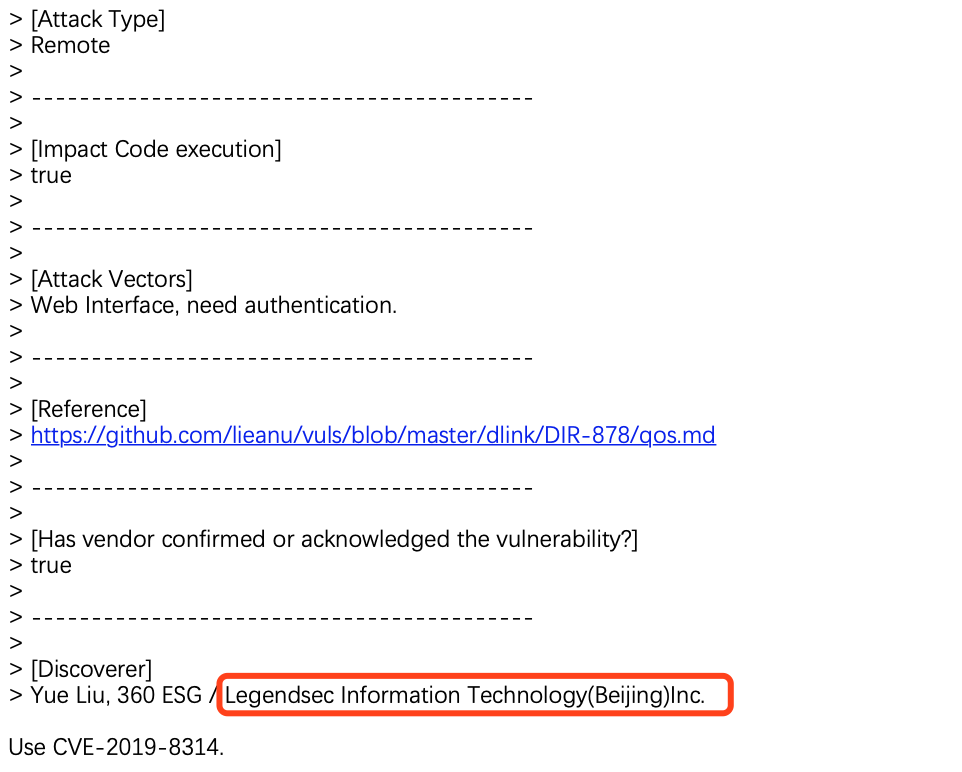
D-Link SetQoSSettings CMD Injection |
|
|
CVE-2019-8314 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8314
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/qos.md
|
 |
| 2 |
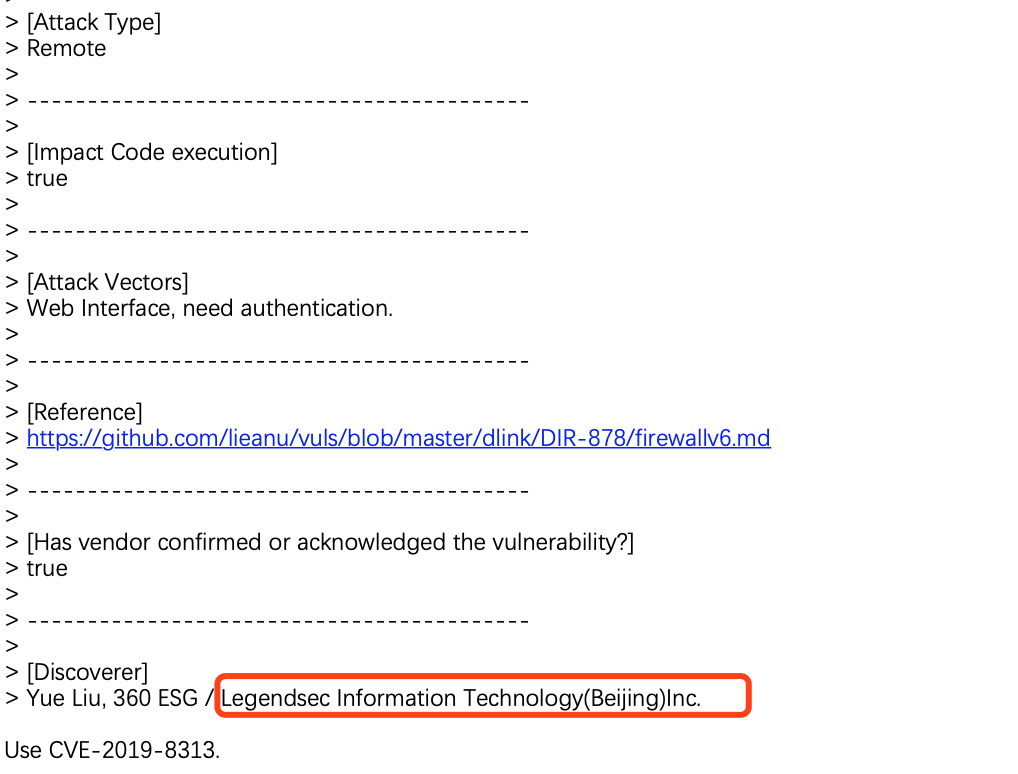
D-Link SetIPv6FirewallSettings CMD Injection |
|
|
CVE-2019-8313 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8313
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/firewallv6.md
|
 |
| 1 |
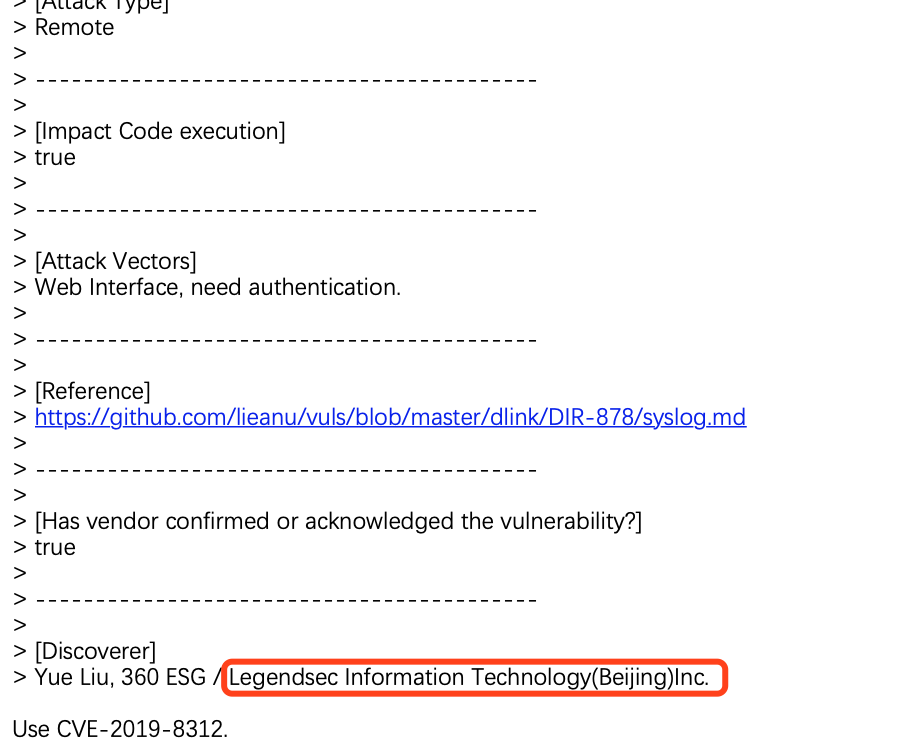
D-linkSetSysLogSettingsCMD Injection |
|
|
CVE-2019-8312 |
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8312
https://github.com/lieanu/vuls/blob/master/dlink/DIR-878/syslog.md
|
 |